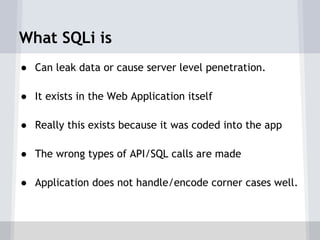
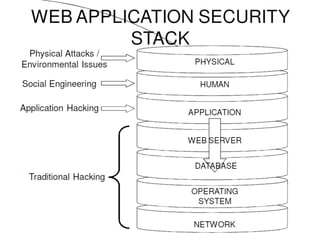
This document summarizes a presentation on SQL injection prevention. It introduces the three presenters - Colin Buckton from OWASP, David Klassen who will demonstrate SQL injection, and Jose Kaharian who will discuss the BSIMM study. Buckton covers OWASP resources and describes SQL injection vulnerabilities. Klassen demonstrates SQL injection in a code sample and how to prevent it. Kaharian discusses a study of software security initiatives in businesses and how secure coding is becoming a priority in hiring. The presentation aims to raise awareness of SQL injection risks and prevention best practices.