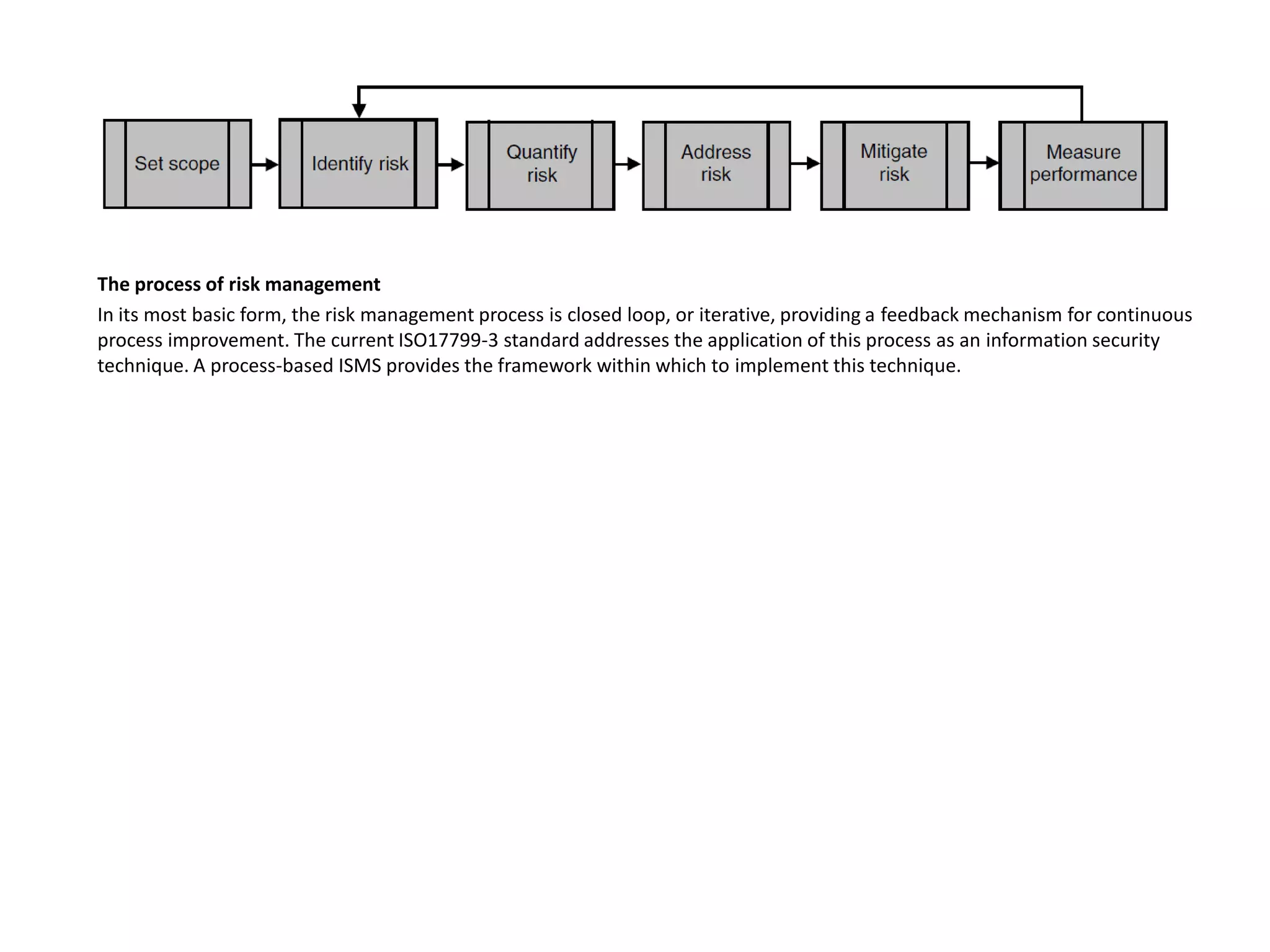
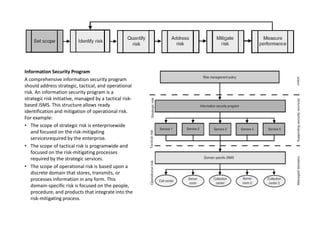
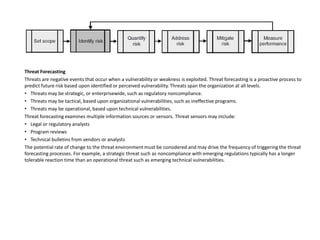
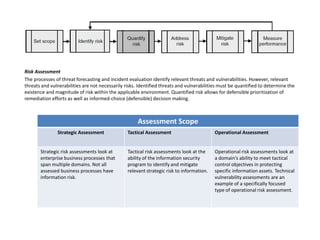
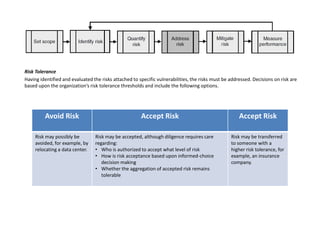
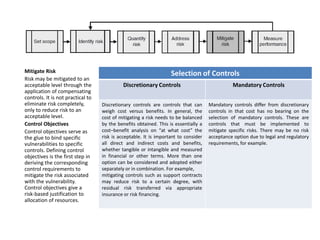
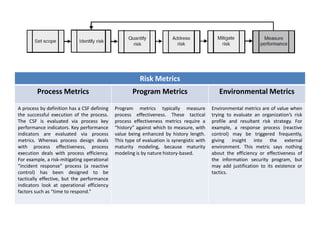
The process of risk management involves continuous improvement through a closed loop feedback mechanism. An information security management system (ISMS) provides the framework to implement the risk management process technique. A comprehensive information security program should address strategic, tactical, and operational risks. Threat forecasting examines information sources to predict future risks based on identified or perceived vulnerabilities at the strategic, tactical, and operational levels. Risk assessments quantify relevant threats and vulnerabilities to determine the existence and magnitude of risk. Controls are selected to mitigate risk to an acceptable level based on the organization's risk tolerance through either discretionary or mandatory controls. Process, program, and environmental metrics are used to evaluate the risk management process.