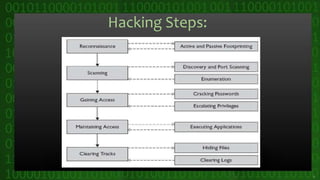
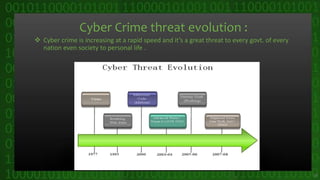
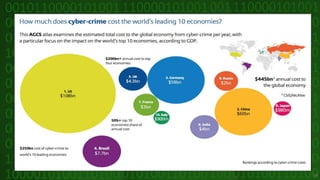
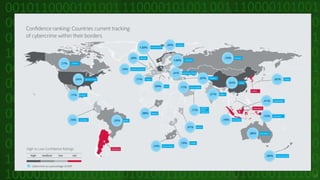
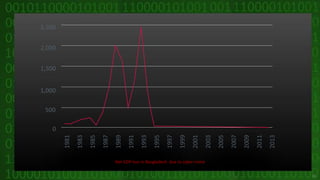
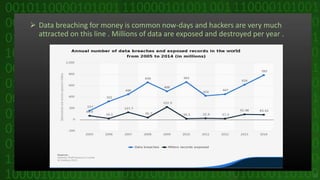
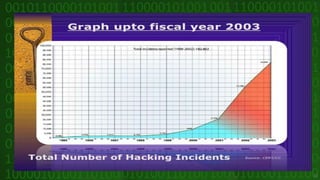
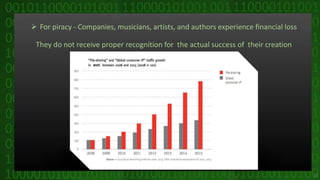
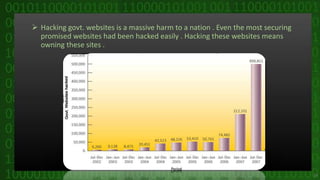
This document discusses cyber crime and security. It begins by defining cyber crime as any criminal act dealing with computers and networks, including traditional crimes conducted online. The document then covers the history of cyber crime, categories of cyber crime such as those against persons, property, and government. It discusses various types of cyber crimes like hacking, computer vandalism, DoS attacks, and their impact. The document also covers cyber security, ethics, laws, and tips for staying safe online.