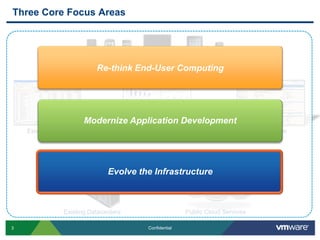
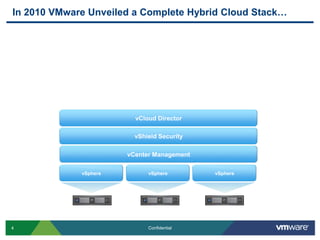
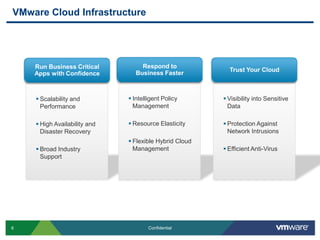
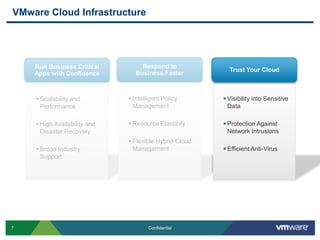
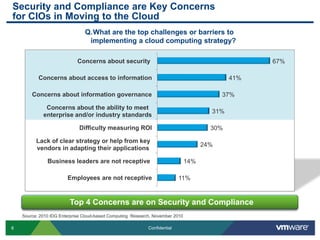
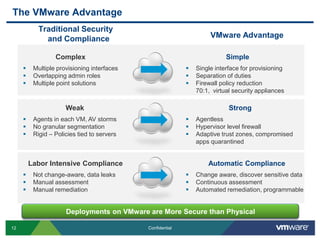
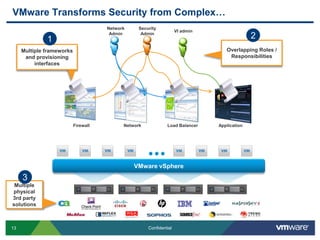
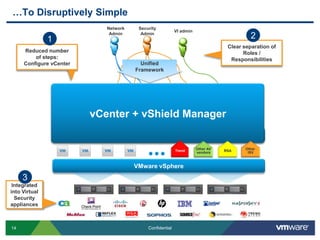
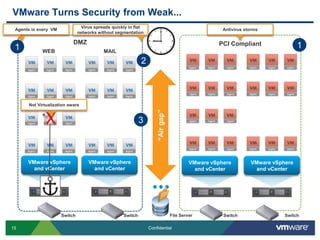
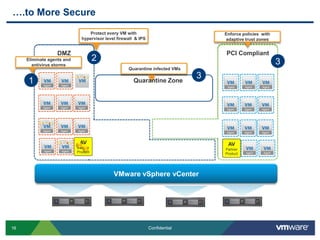
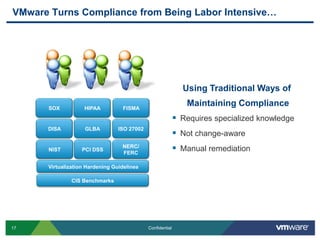
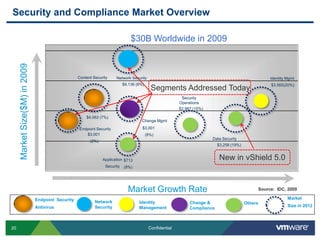
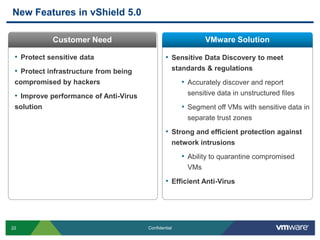
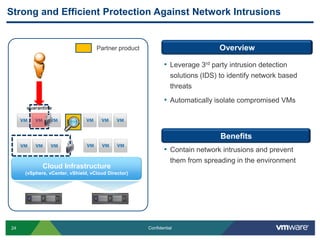
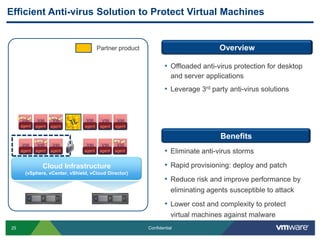
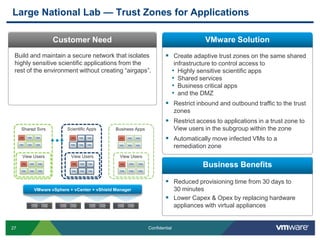
VMware is introducing major upgrades to its cloud infrastructure stack in 2011, including vSphere 5.0, vCloud Director 1.5, and vShield 5.0. The new vShield 5.0 release addresses customer concerns around security and compliance in the cloud with new features such as sensitive data discovery, intrusion prevention, and efficient antivirus protection using virtual appliances. These new capabilities help customers secure sensitive data and infrastructure, segment networks into trust zones, and automate compliance audits, allowing them to trust running business critical applications in the cloud.