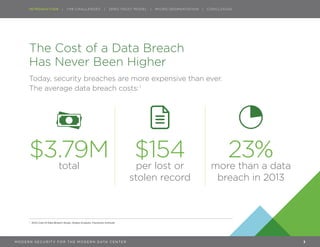
The document discusses the increasing risk of data center breaches and the transition towards more secure models, particularly micro-segmentation, which is enabled by network virtualization. It highlights the inadequacies of traditional perimeter-centric security and introduces the zero trust model as a necessary approach to securing data centers. Micro-segmentation allows for fine-grained security policies that protect workloads by isolating threats, ultimately enabling faster, flexible, and dynamic security services.