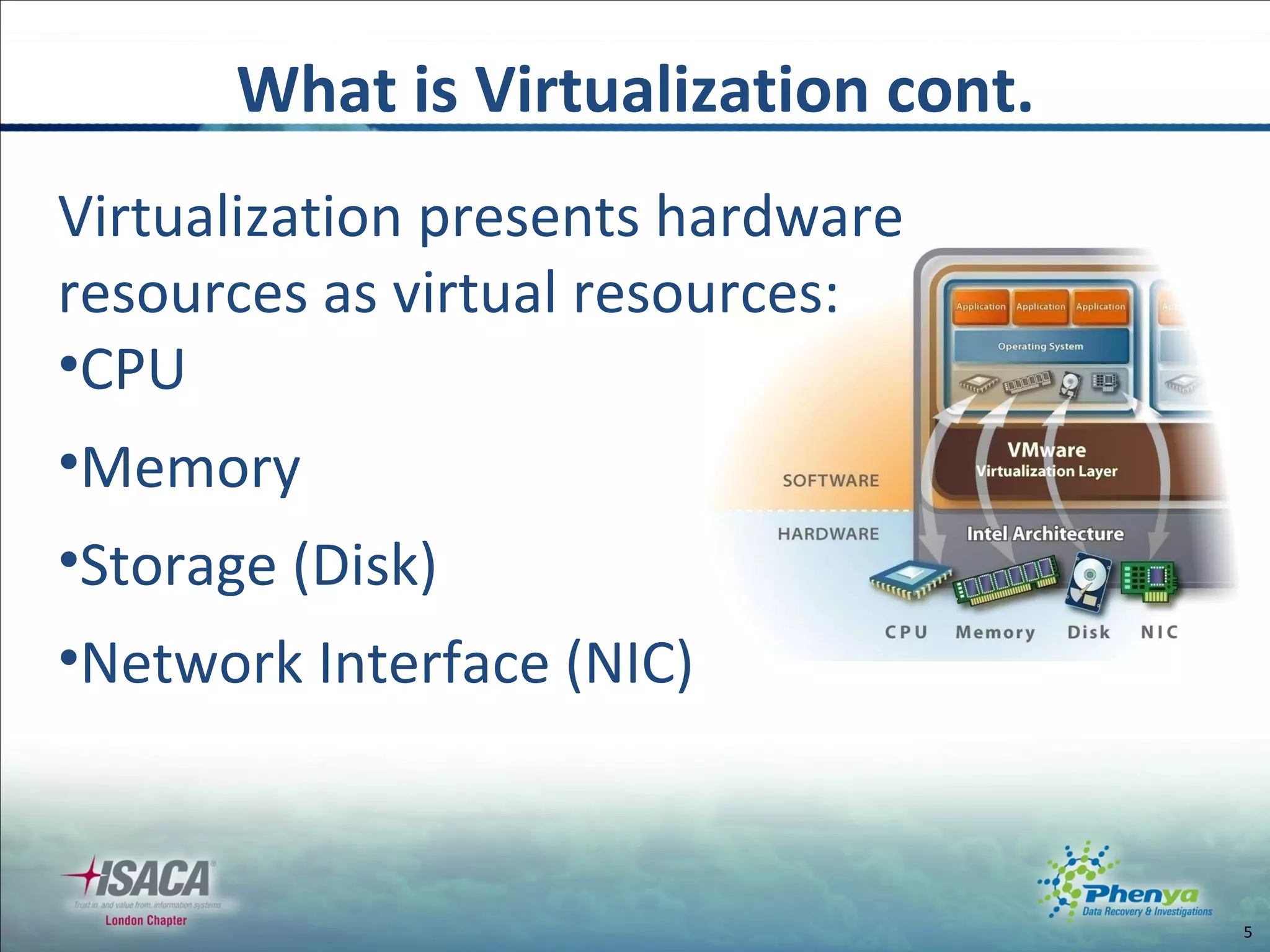
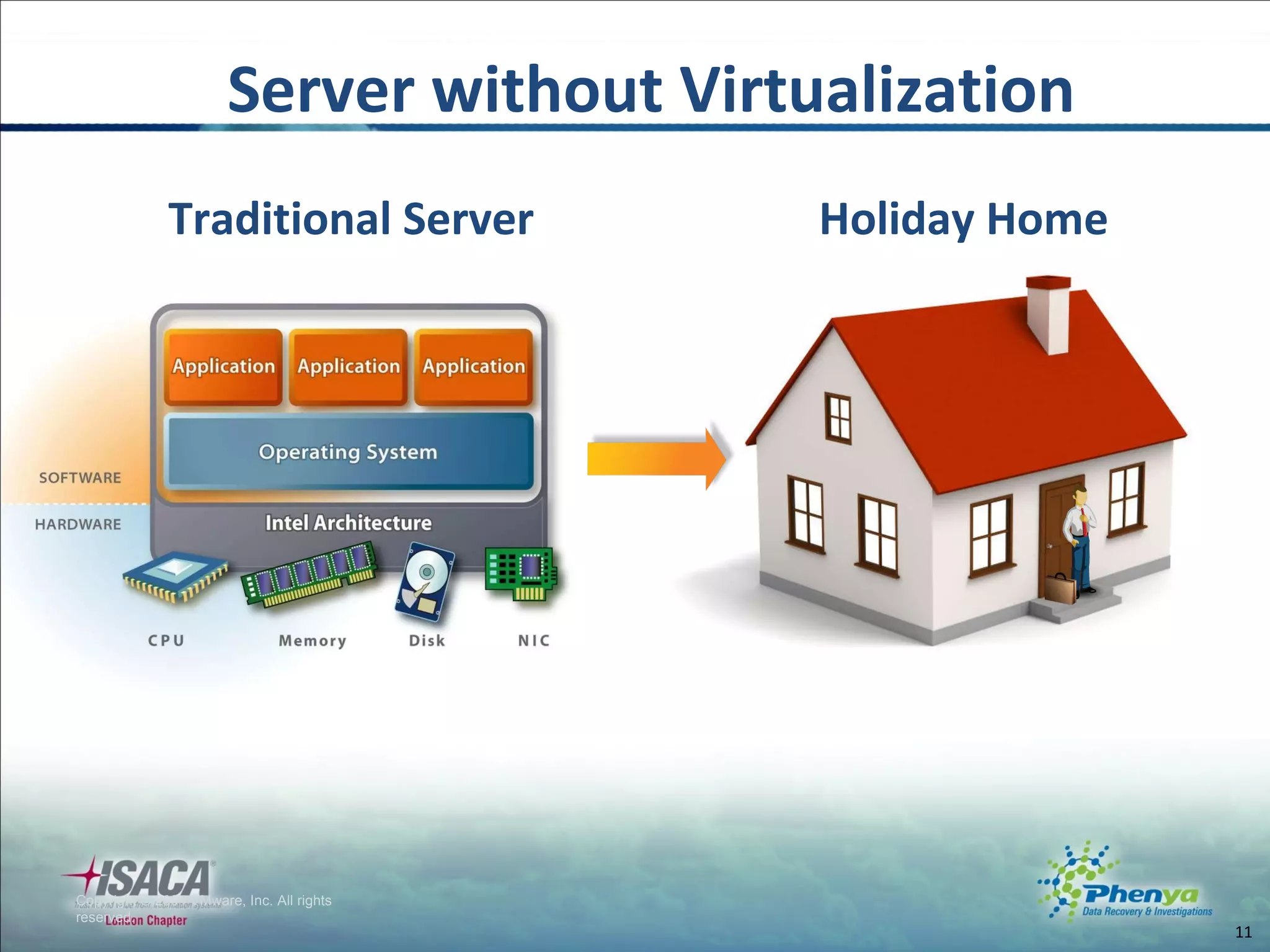
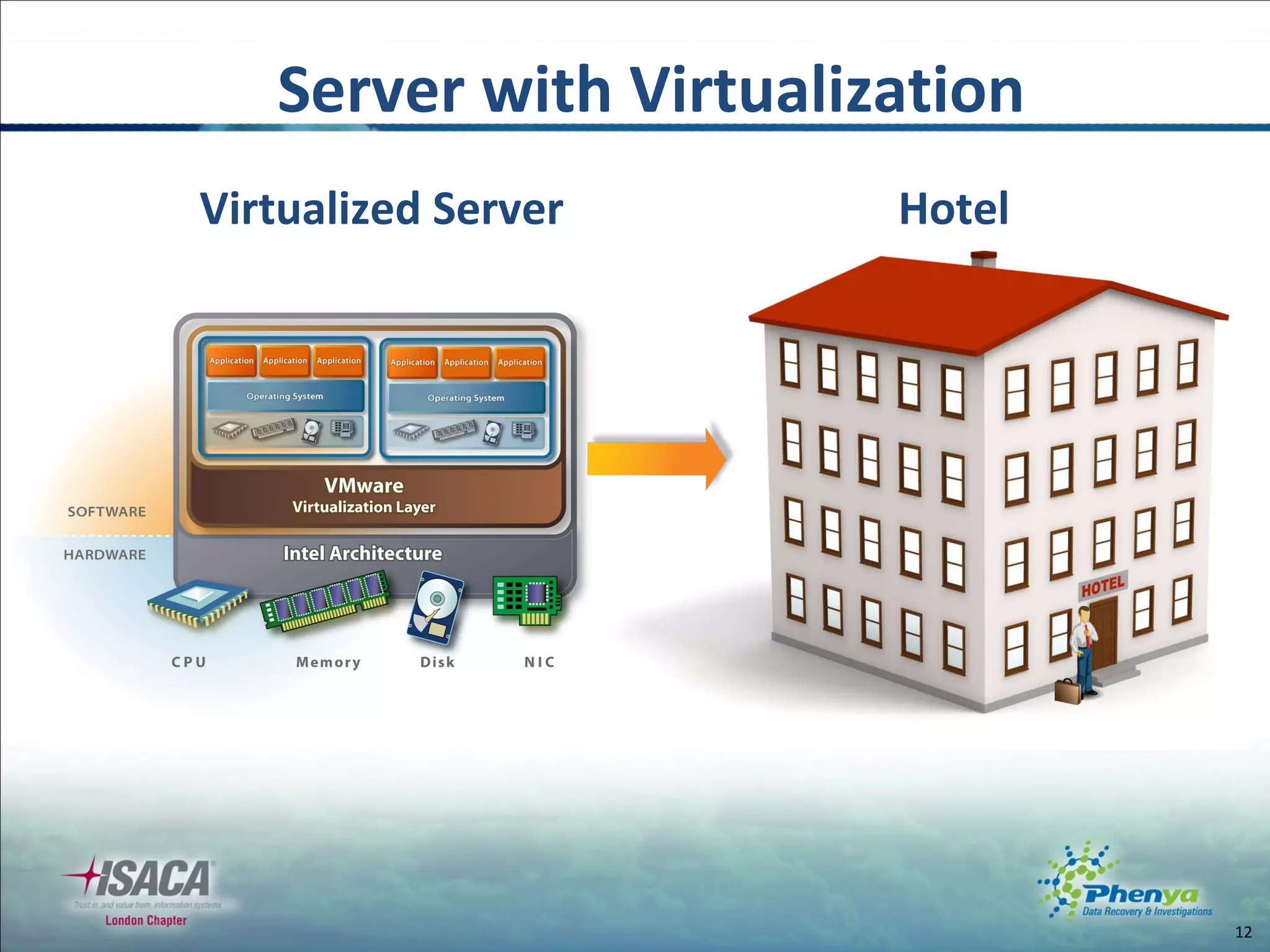
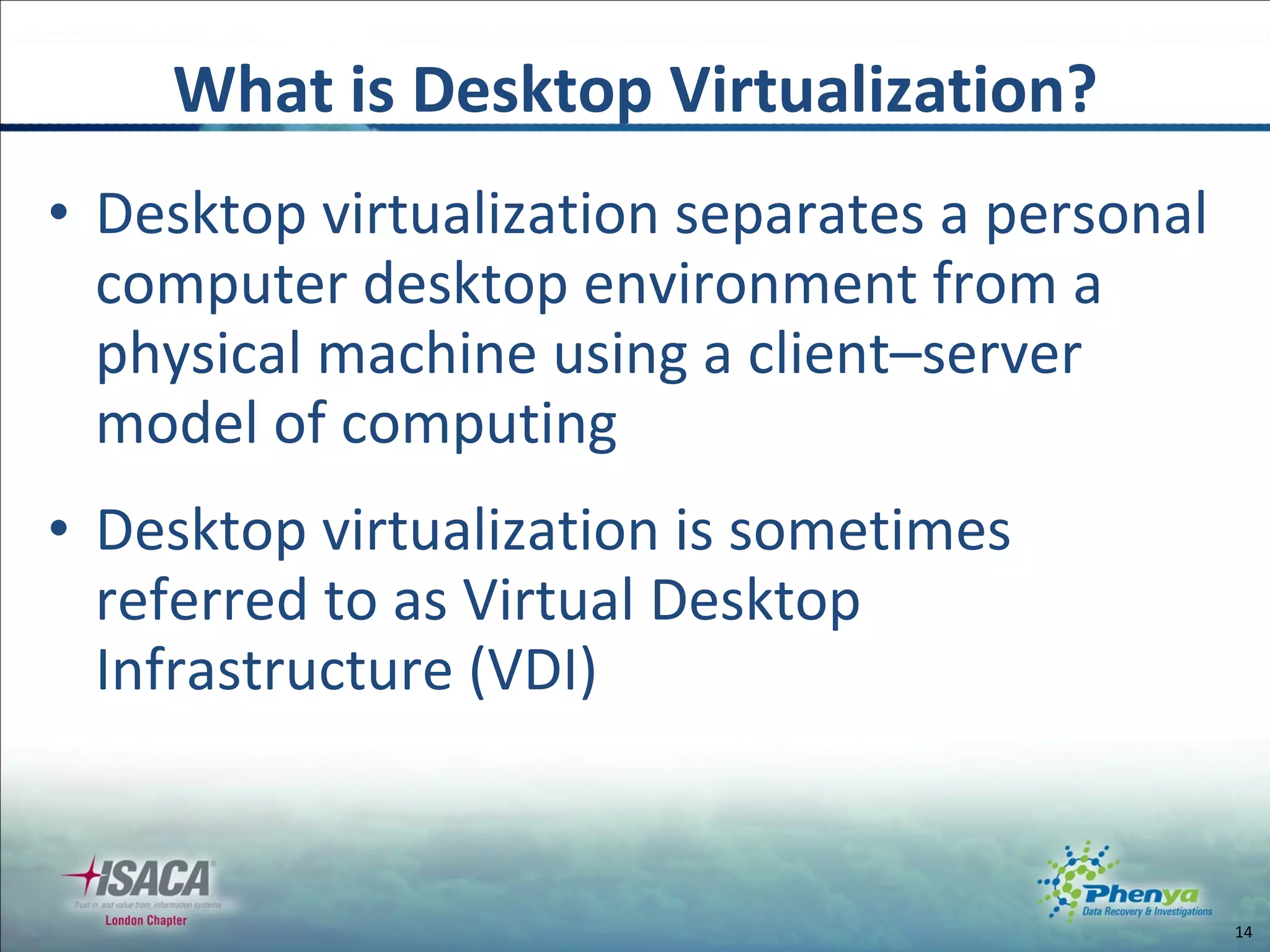
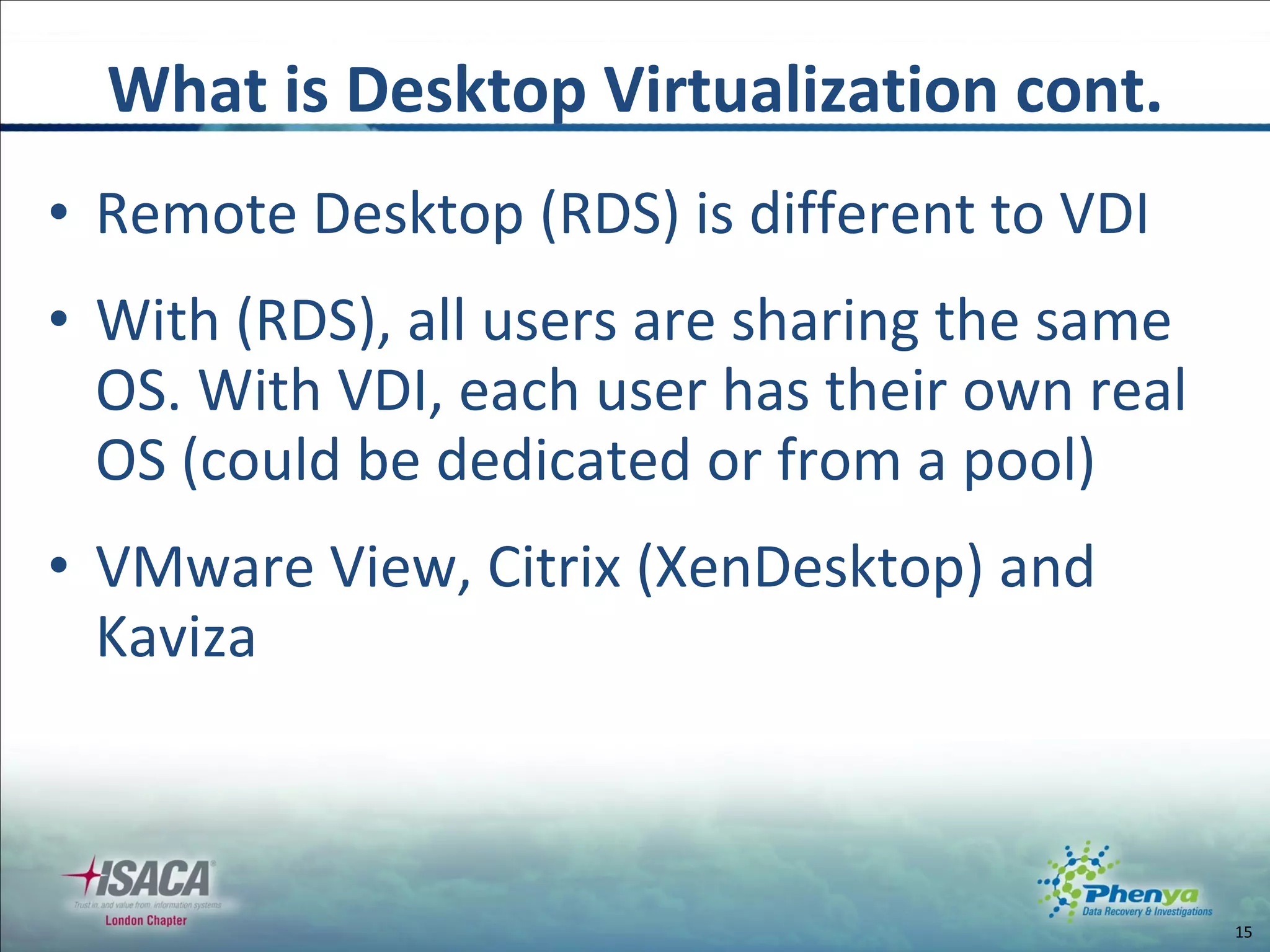
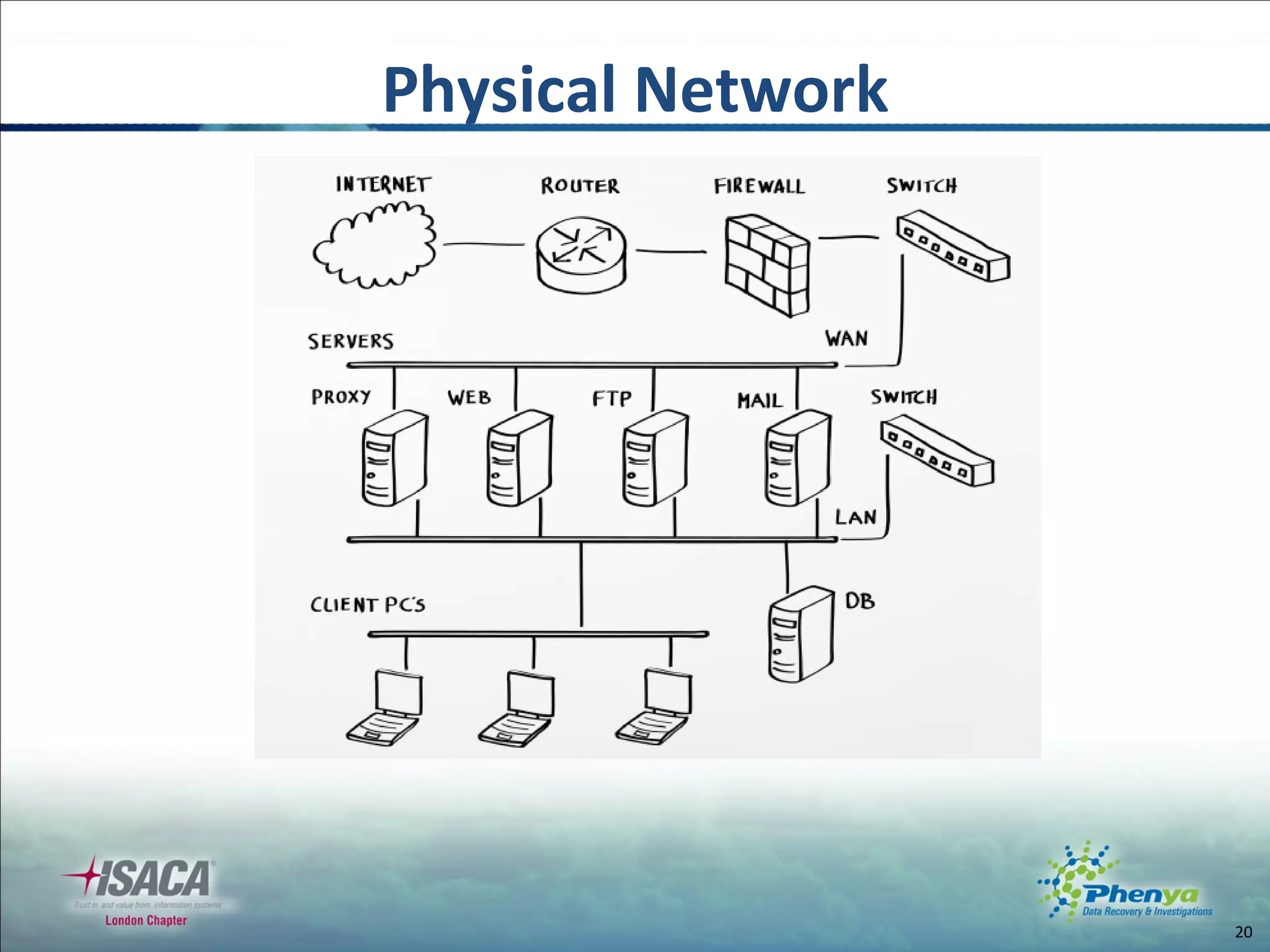
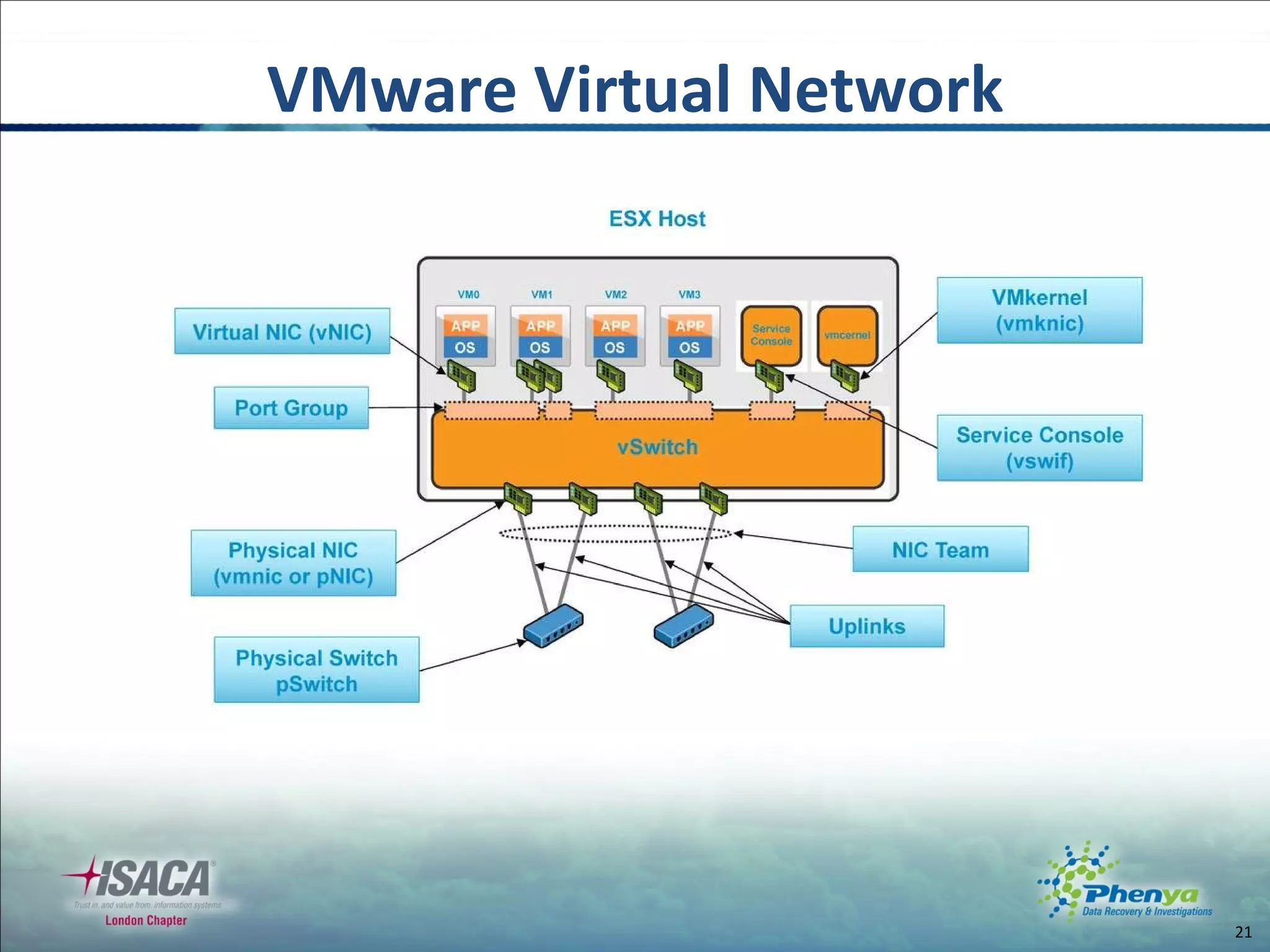
The document discusses various topics related to virtualization and cloud computing including definitions, types, security issues and compliance challenges. It defines virtualization as the creation of virtual versions of hardware resources like CPU, memory and storage. The main types of virtualization covered are server, desktop, application, network and storage virtualization. Private clouds are discussed as being operated solely for an organization, while raising similar security controls as virtualization. Resources on virtualization security best practices from NIST, VMware and Cloud Security Alliance are also referenced.



















![Questions? Kevin Wharram [email_address]](https://image.slidesharecdn.com/kevinwharram-110305054818-phpapp02/75/Kevin-wharram-39-2048.jpg)