This document provides an overview of key concepts in distributed systems including:
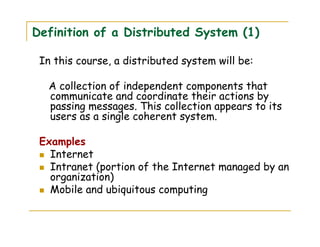
1) A distributed system is defined as a collection of independent components that communicate and coordinate their actions by passing messages, appearing as a single coherent system to users.
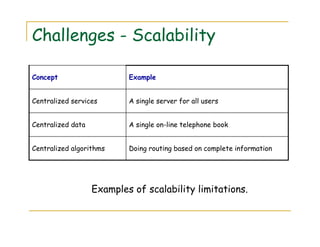
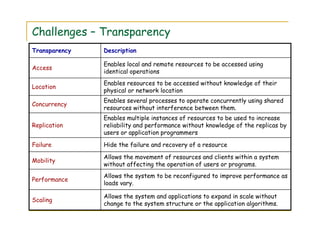
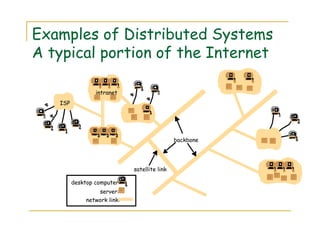
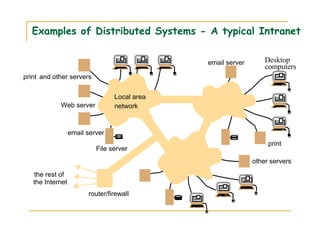
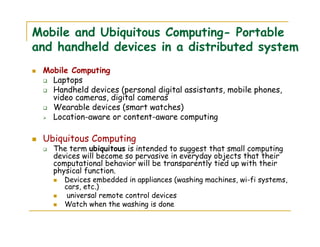
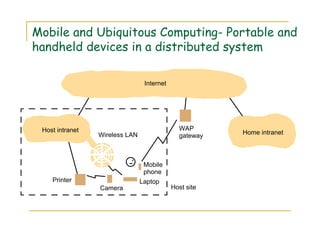
2) Examples of distributed systems include the Internet, intranets, mobile computing systems, and ubiquitous computing devices. Distributed systems face challenges related to concurrency, failures, scalability, heterogeneity, security and transparency.
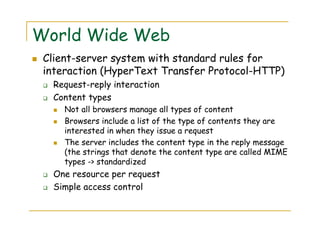
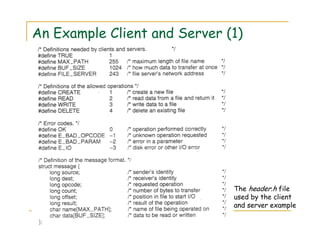
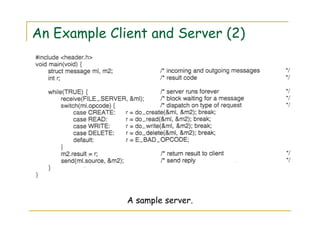
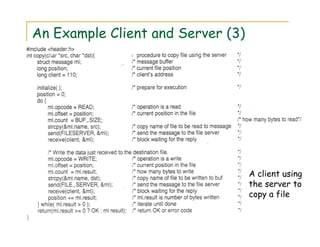
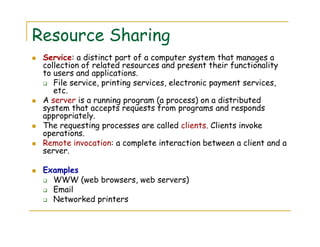
3) The document discusses several examples of distributed systems in detail, including the World Wide Web which allows sharing of documents and services via HTTP, URLs, HTML and web servers/browsers. Client-server interaction and dynamic content are also described.





![Web servers and web browsers
Internet
BrowsersWeb servers
www.google.com
www.cdk3.net
www.w3c.org
Protocols
Activity.html
http://www.w3c.org/Protocols/Activity.html
http://www.google.comlsearch?q=kindberg
http://www.cdk3.net/
File system of
www.w3c.org
http://servername[:port] [/pathname] [?query] [#fragment]
~username, ~/public_html, index.html](https://image.slidesharecdn.com/cs556-section1-140529142201-phpapp02/85/Cs556-section1-13-320.jpg)