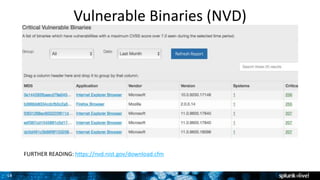
Brian Fennimore discusses how threat data can be useful for security operations. He explains that threat data provides information like IP addresses and file hashes that can help identify threats. This data can be used in many ways, such as blocking malicious IPs or scanning for vulnerable files. Fennimore also describes how his company Virtustream uses threat data with Splunk for security monitoring, automation of compliance reporting, and enrichment of security information. He advocates consuming high quality threat data from various sources to help prevent security issues rather than just detect them after the fact.