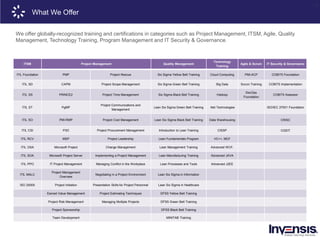
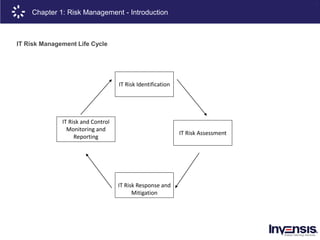
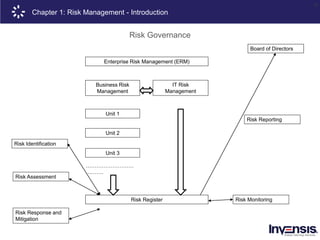
The document details the CRISC® training course offered by Invensis Learning, a global provider of certification training in IT and technical fields. It includes an overview of risk management, highlighting various types of risks, risk governance, and the risk management lifecycle, along with methodologies and techniques for risk identification and assessment. Additionally, it emphasizes the importance of aligning risk appetite and tolerance with organizational strategies to ensure effective risk management practices.