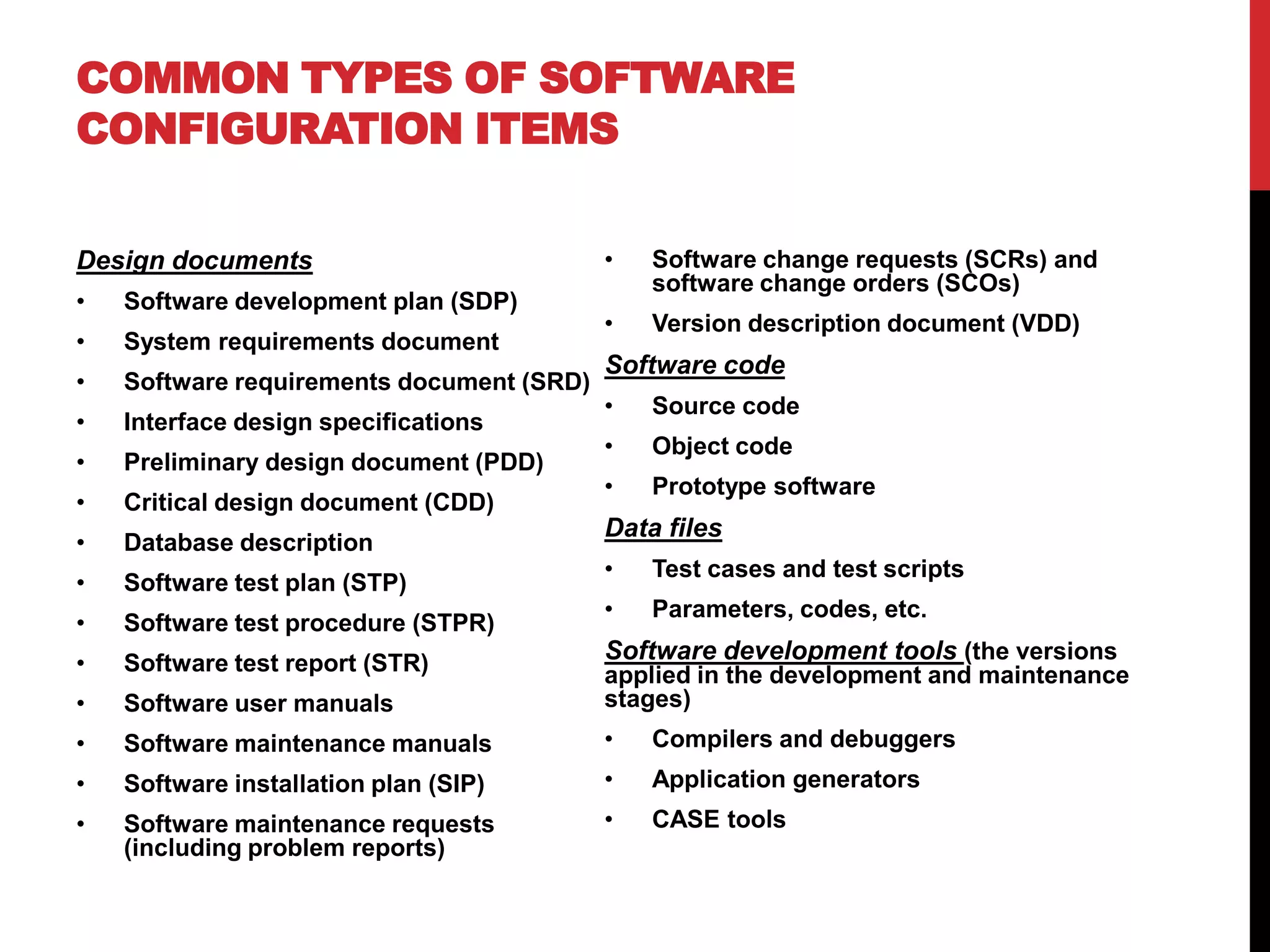
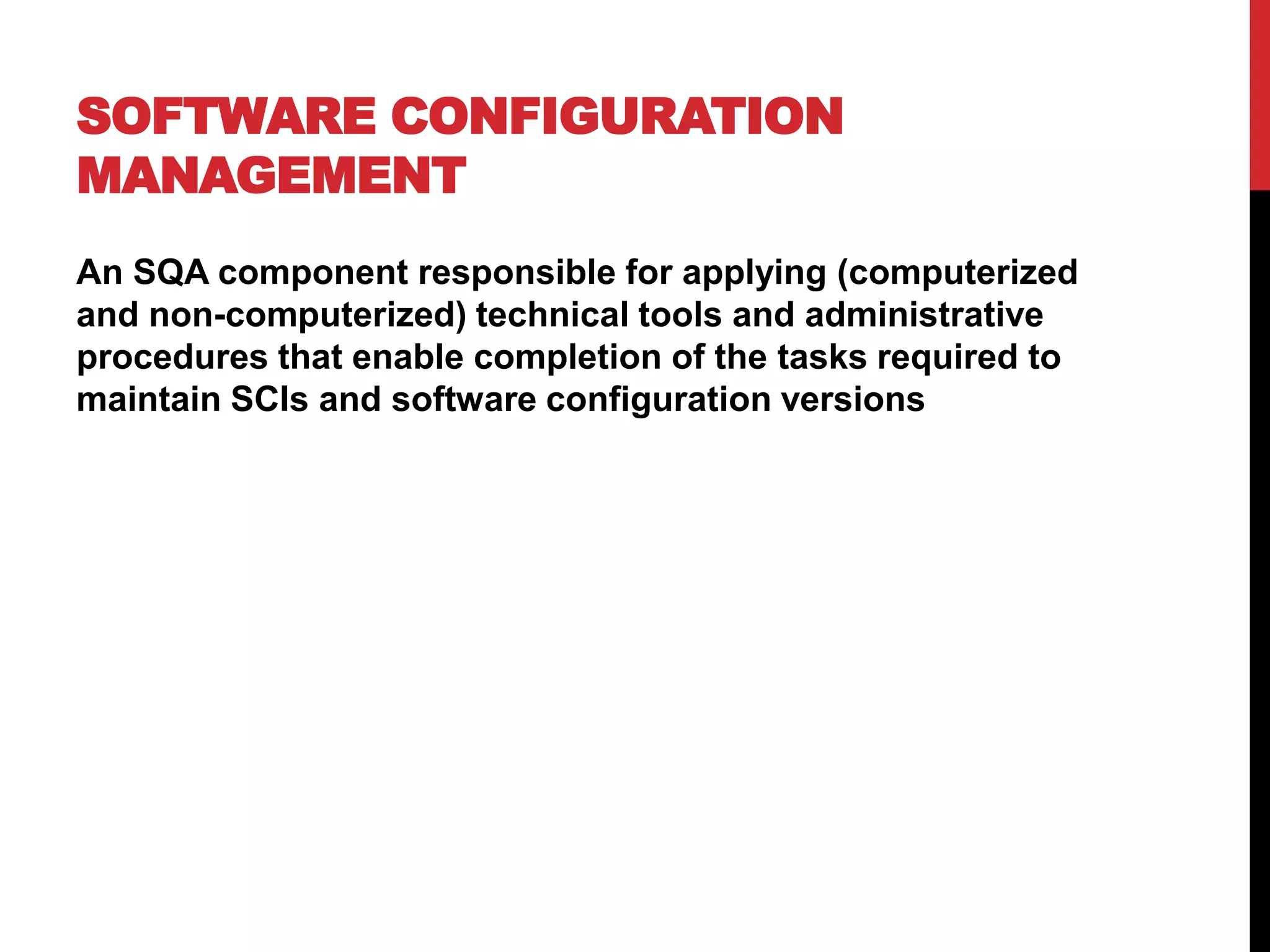
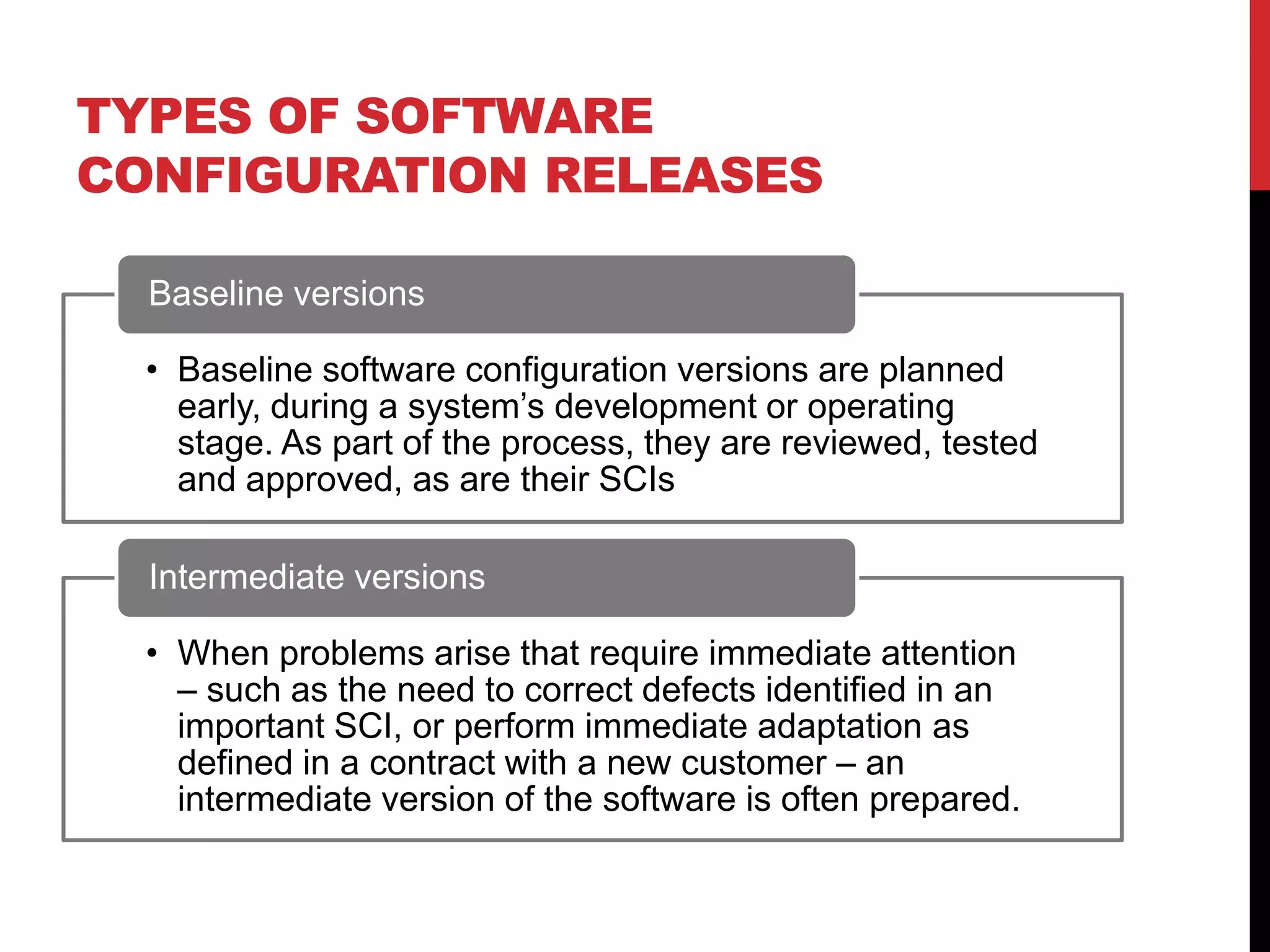
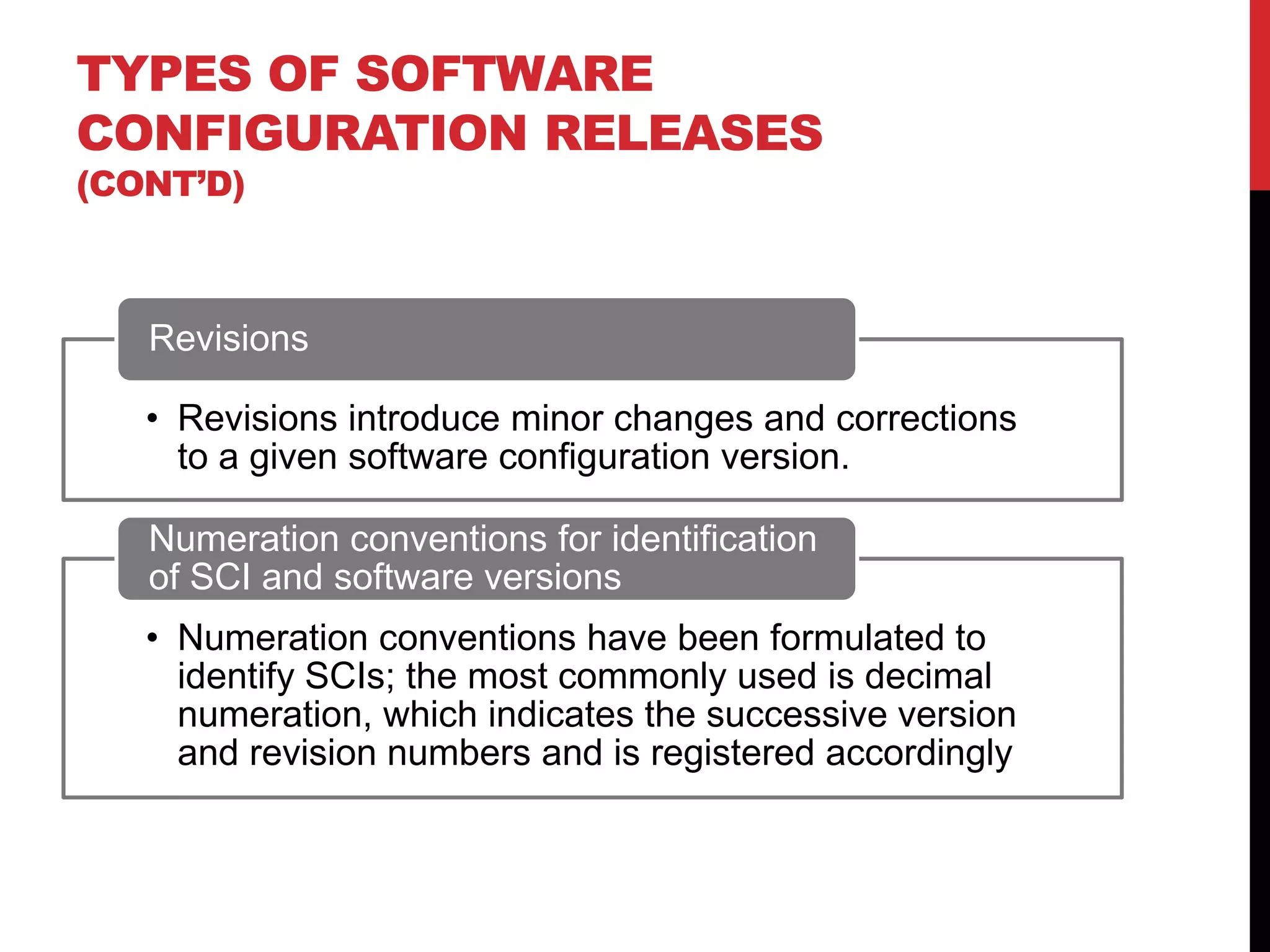
This document discusses software configuration management. It defines key terms like software configuration item and version. It describes the four main classes of SCIs - design documents, software code, data files, and development tools. It outlines the main tasks of SCM like control of software changes, release of versions, provision of information, and compliance verification. It also discusses topics like change control, approval of changes, release types, numeration conventions, configuration management plans, and evolution models.