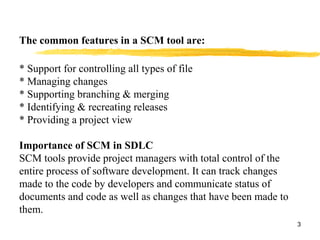
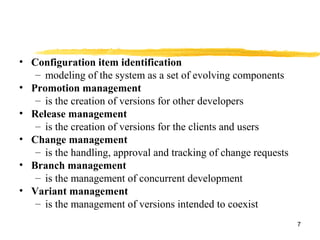
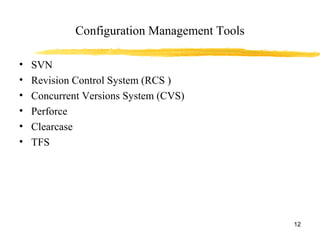
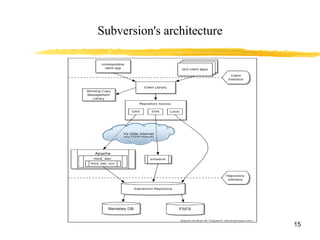
Software configuration management (SCM) is the process of managing changes to software code throughout the development lifecycle. SCM tools provide version control, tracking of code changes, and facilitate collaboration between developers. Key SCM concepts include configuration items, change requests, versions, promotions, and releases. SCM activities involve configuration identification, control of changes, tracking configuration status, auditing, and management of the development environment and process. Common SCM tools include SVN, CVS, Perforce, Clearcase, and TFS.

![2
Definition of SCM
• Software configuration management is the discipline of
managing the evolution of complex software systems [IEEE
STD 1987].
• Software configuration management is the process of
identifying, organizing & controlling changes to the software
during development & maintenance. SCM Operates throughout
software development lifecycle (SDLC). From the software
developer's perspective, SCM facilitates the development &
change implementation activities.](https://image.slidesharecdn.com/scm-130618125330-phpapp02/85/Scm-PPT-2-320.jpg)