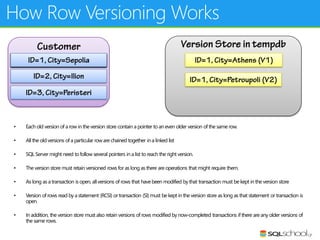
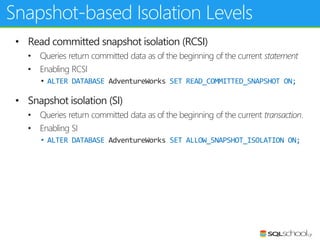
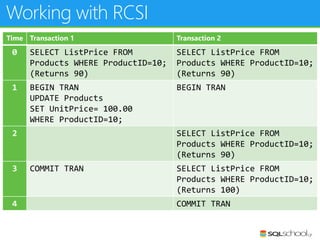
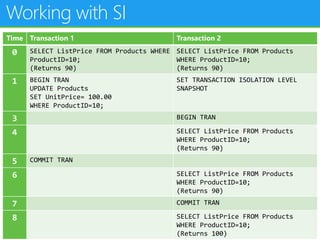
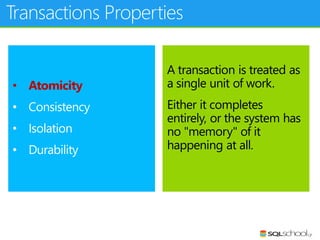
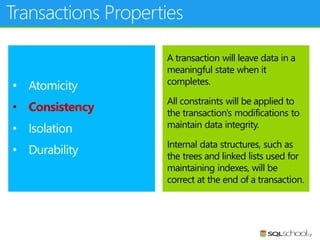
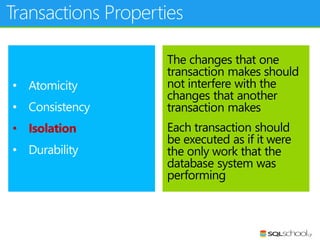
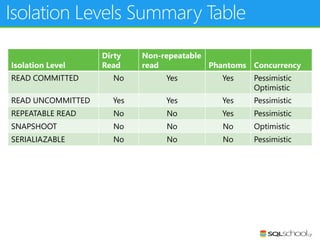
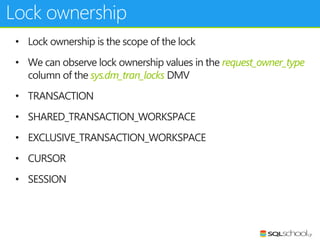
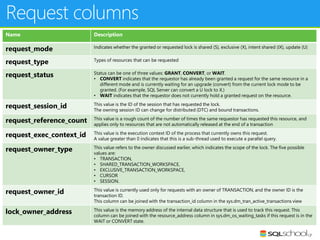
This document provides an outline for a presentation on concurrency in SQL Server. The presentation introduction discusses sessions, locking, blocking, deadlocks, and pressure. It then covers transactions, isolation levels, and phenomena like dirty reads, non-repeatable reads, and phantom reads. The document discusses the speaker's background and certifications. It concludes with an outline of topics to be covered, including locking basics, advanced locking concepts, controlling locking, pessimistic and optimistic concurrency approaches.




















![• Only one copy of a compiled stored procedure plan is generally
in cache at any given time
• Compile locks are acquired during the parts of the compilation
process that must be serialized.
• SQL Server holds the locks for a very short period but
• when many sessions are trying to execute the same procedure
simultaneously, and if the procedure is not schema-qualified when called
• we may end up with noticeable concurrency problems due to compile locks
• The Rolling blocking situation.
• LCK_M_X [COMPILE]
• This type of blocking has a very easy fix
• always schema qualify your stored procedure names
Other Types of Locks - Compile locks](https://image.slidesharecdn.com/ssn0024-concurrencyinsqlserver-140610150909-phpapp01/85/Concurrency-in-SQL-Server-SQL-Night-24-45-320.jpg)