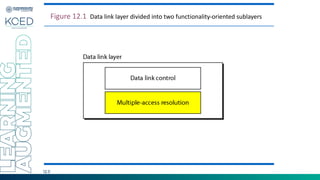
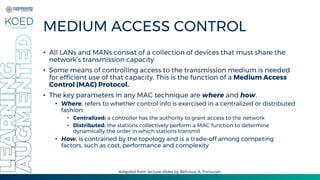
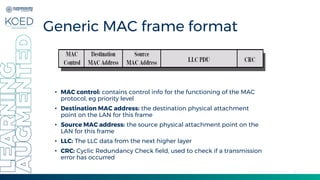
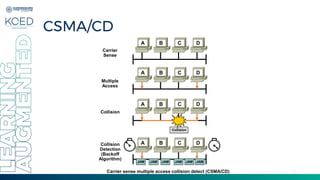
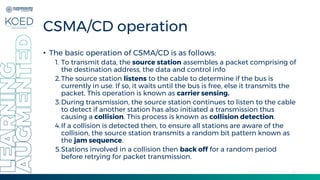
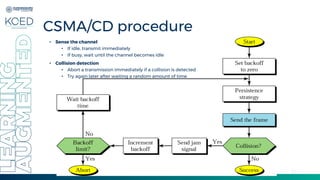
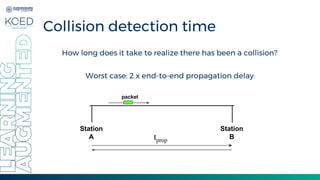
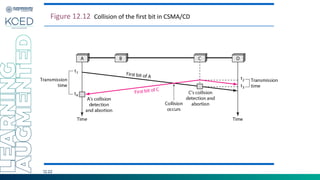
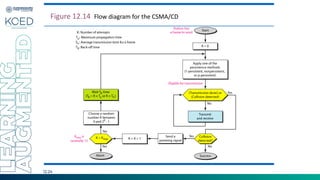
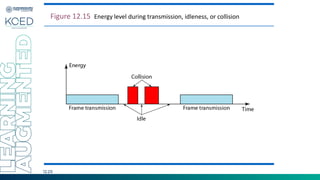
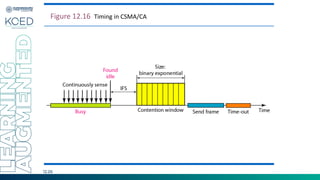
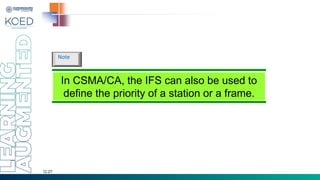
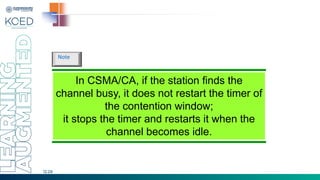
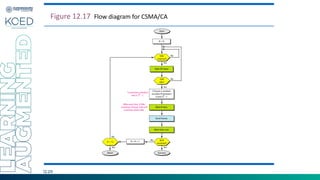
This document provides an overview of Medium Access Control (MAC) protocols, which govern how devices access the transmission medium in Local Area Networks (LANs) and Metropolitan Area Networks (MANs). It discusses key MAC techniques, including Carrier Sense Multiple Access with Collision Detection (CSMA/CD) and Collision Avoidance (CSMA/CA), and outlines their operational procedures, advantages, and use cases. The lecture material is adapted from slides by Behrouz A. Forouzan, offering insights into frame formats, contention methods, and collision management strategies.