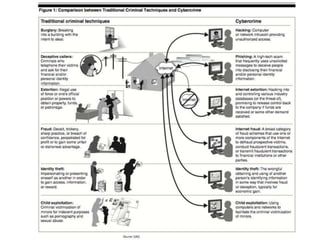
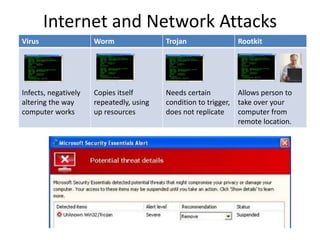
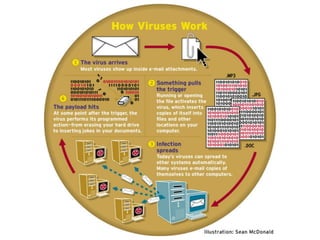
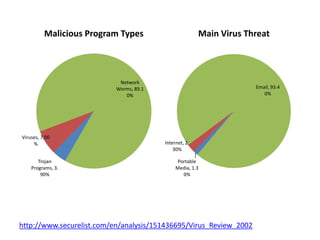
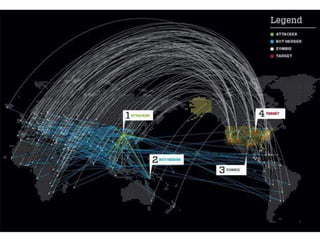
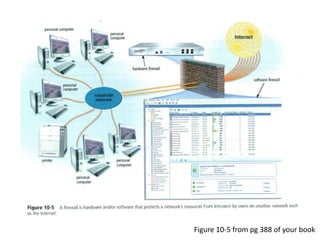
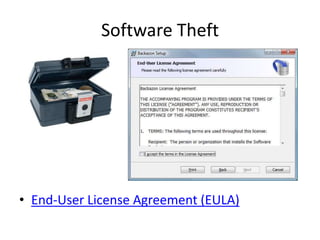
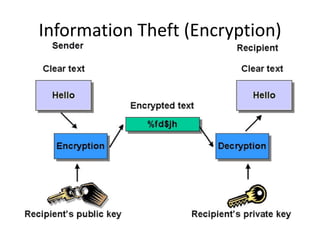
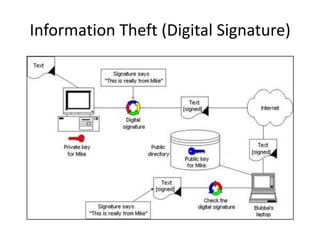
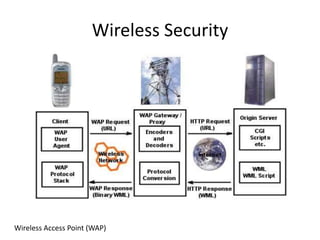
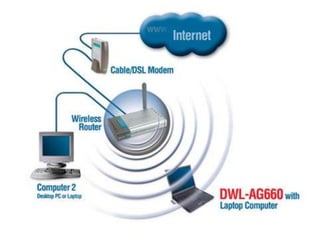
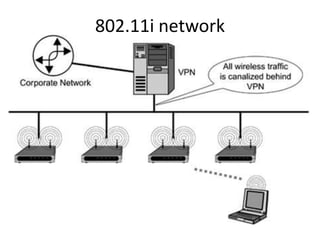
This document provides an overview of computer security topics including types of malicious programs like viruses, worms, and trojans. It discusses how these programs spread and common threats. The document also outlines different safeguards against security issues such as hardware theft, software theft, information theft, system failure, and wireless vulnerabilities. Students are assigned to read the rest of the computer security booklet and prepare for a take home test.