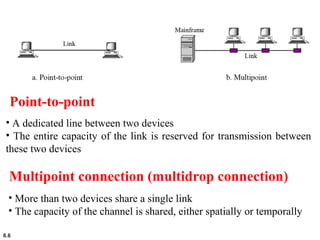
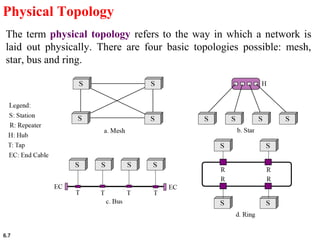
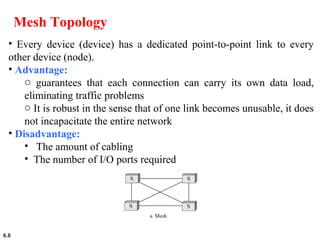
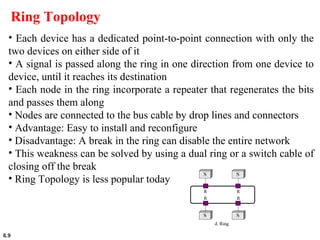
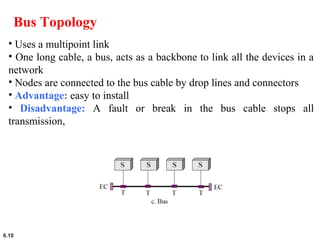
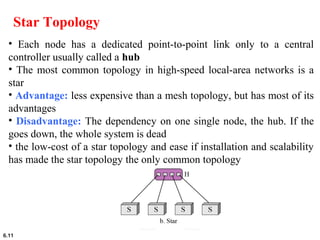
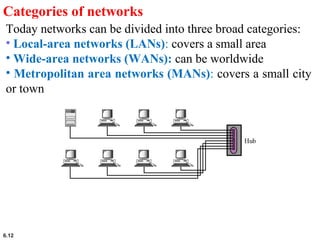
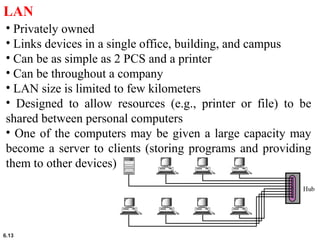
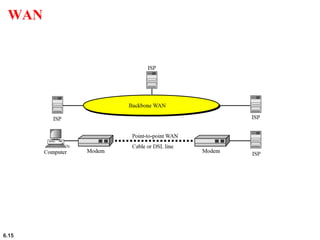
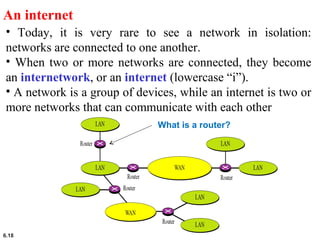
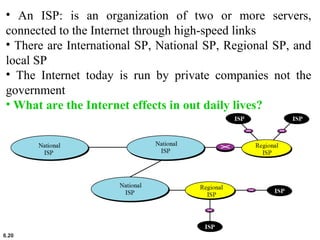
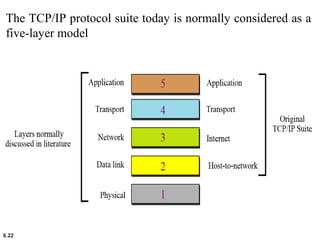
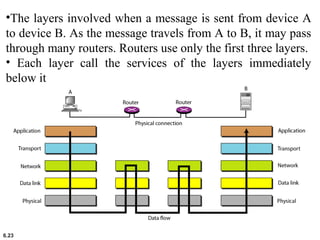
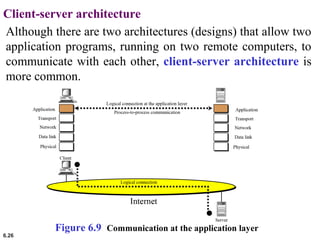
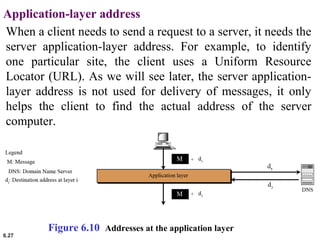
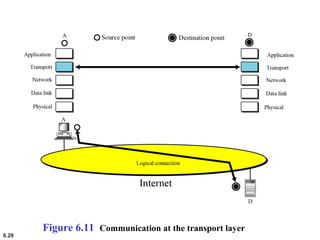
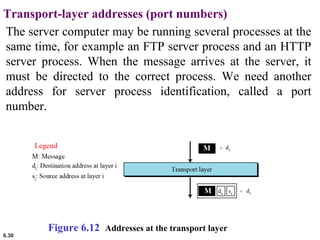
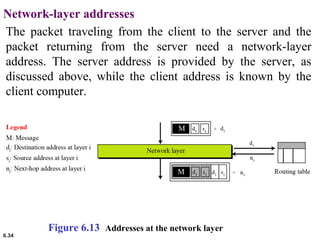
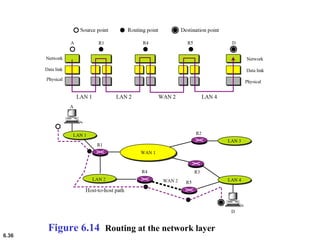
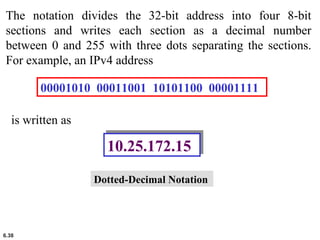
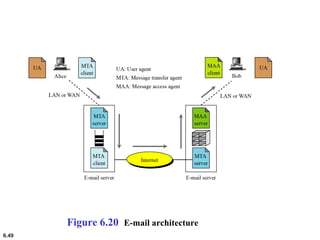
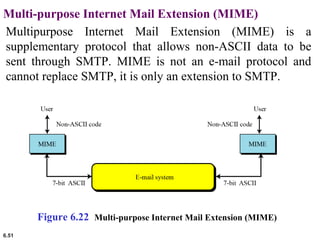
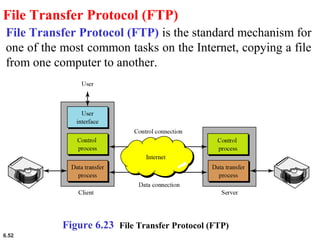
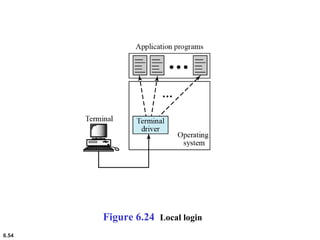
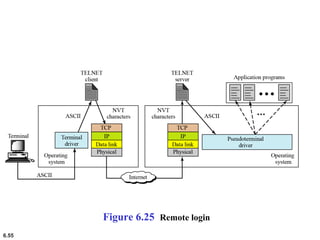
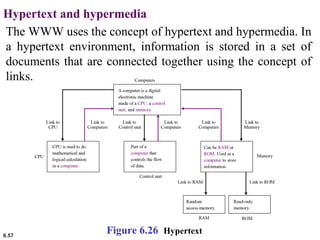
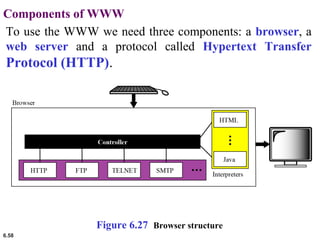
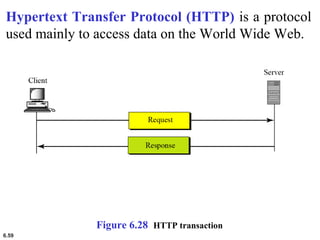
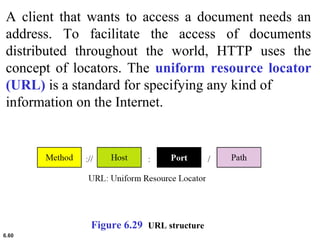
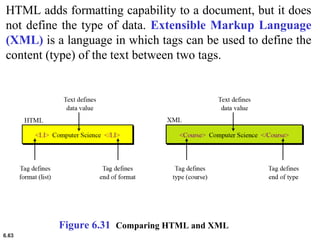
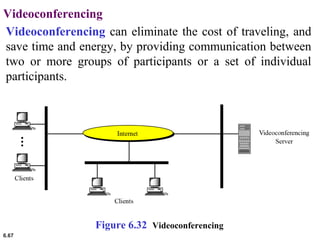
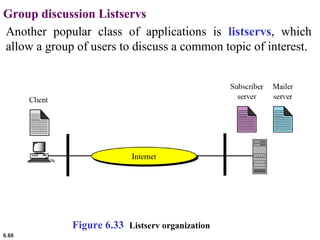
This document provides an overview of computer networks and the TCP/IP protocol suite. It describes network criteria like performance and reliability. It discusses physical network structures like point-to-point, multipoint, mesh, star, bus and ring topologies. It also defines categories of networks such as local area networks (LANs), wide area networks (WANs) and metropolitan area networks (MANs). A key point is that the TCP/IP protocol suite, which controls the Internet, is organized into five layers: application, transport, internet, network interface and physical. The layers are described along with how a message travels through them.