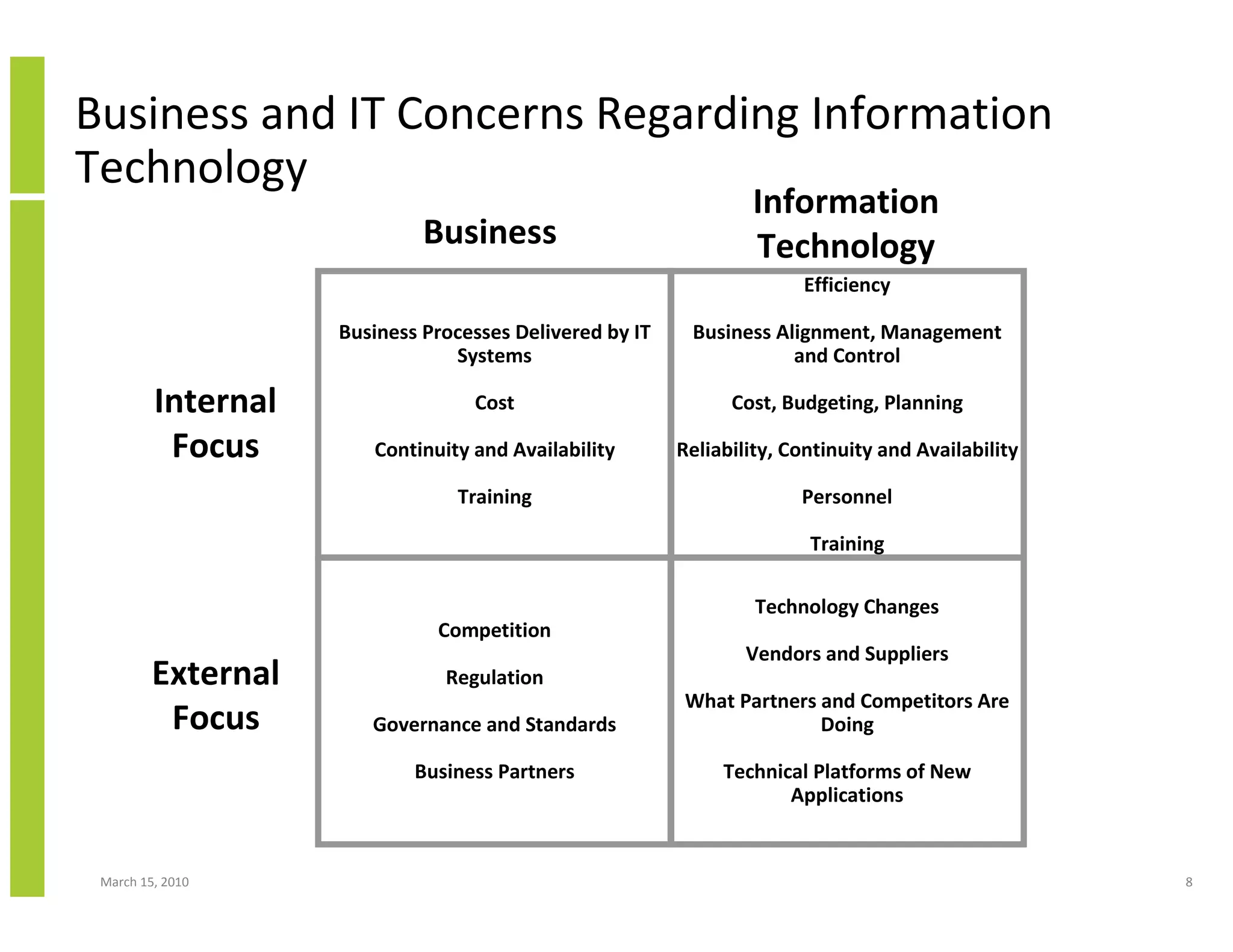
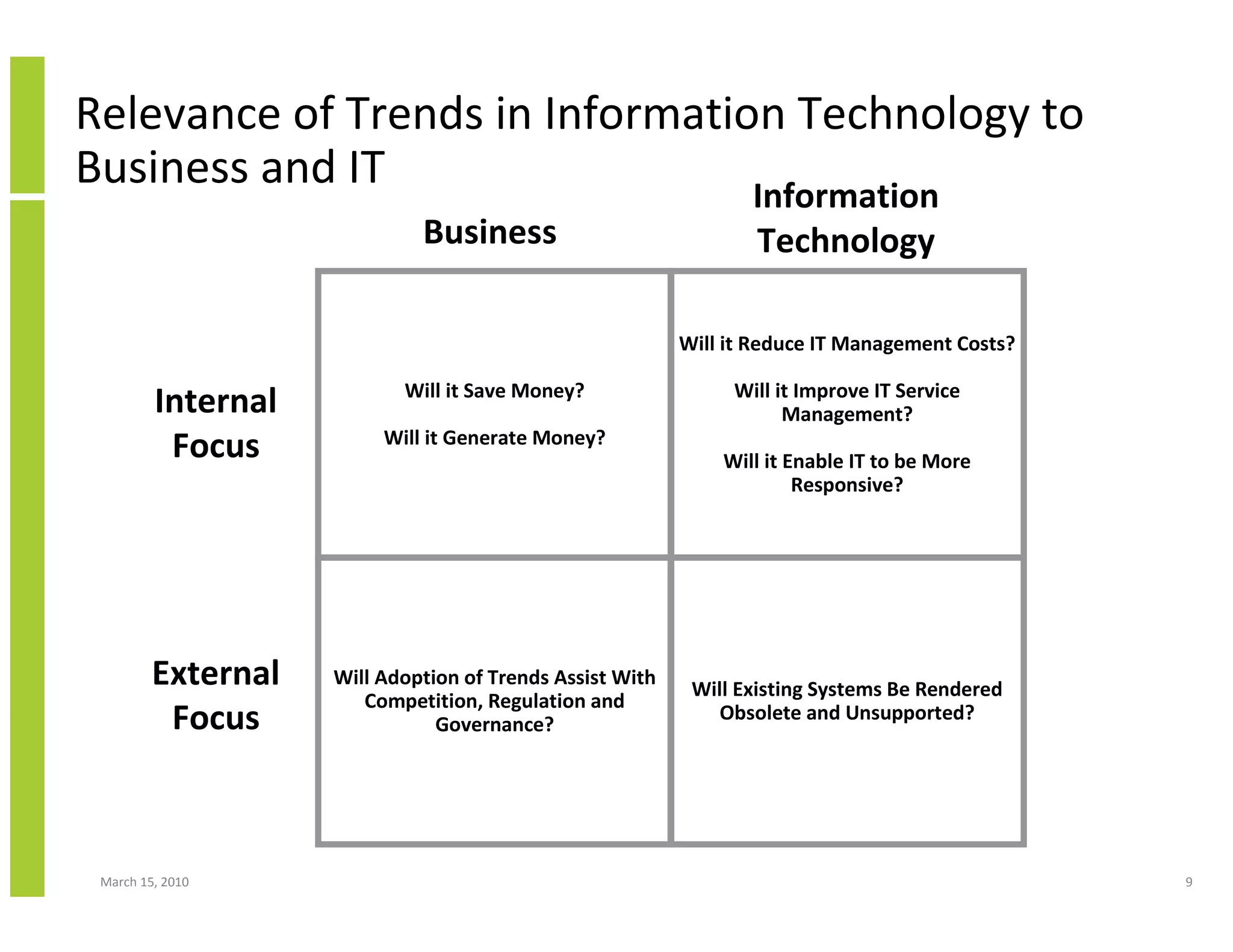
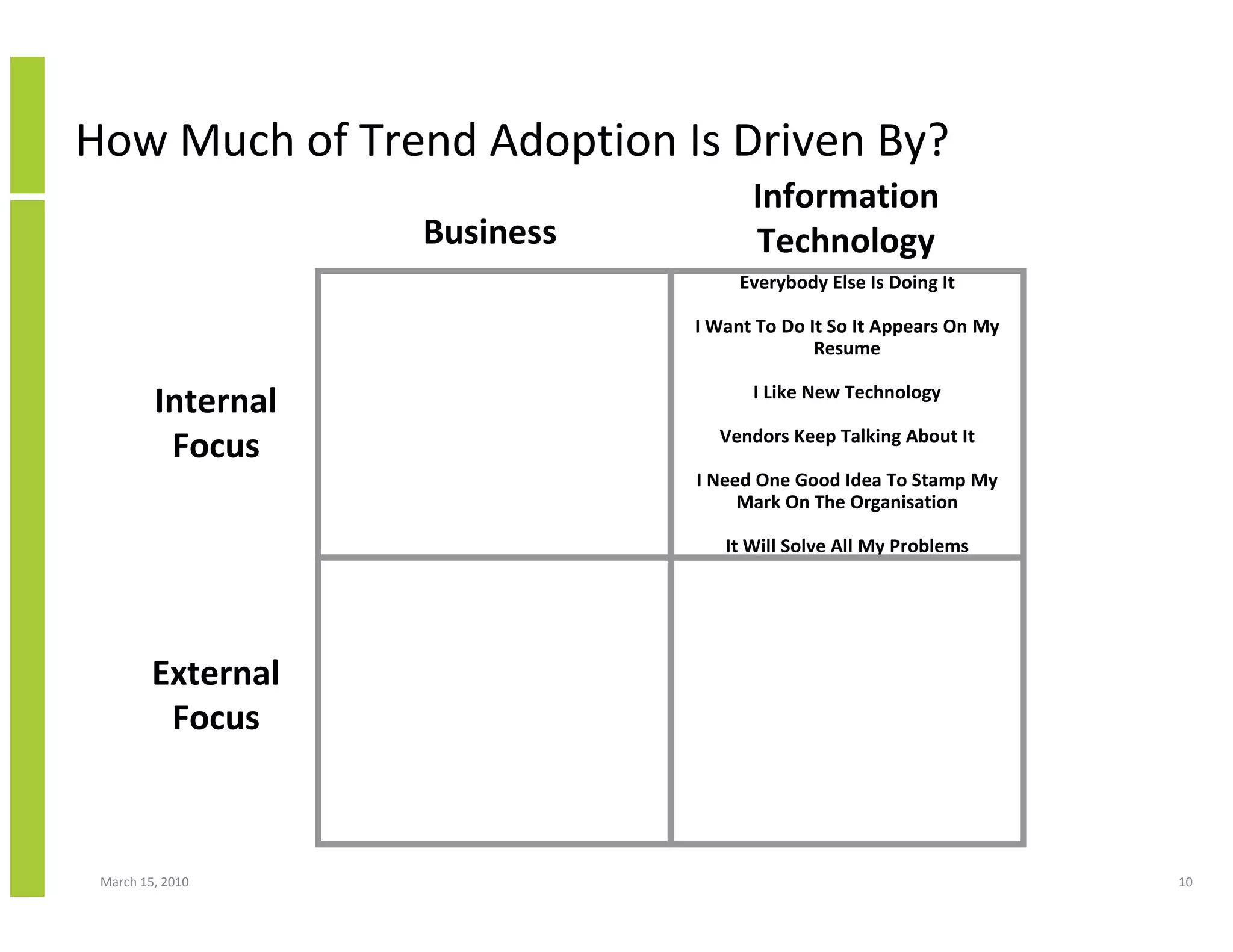
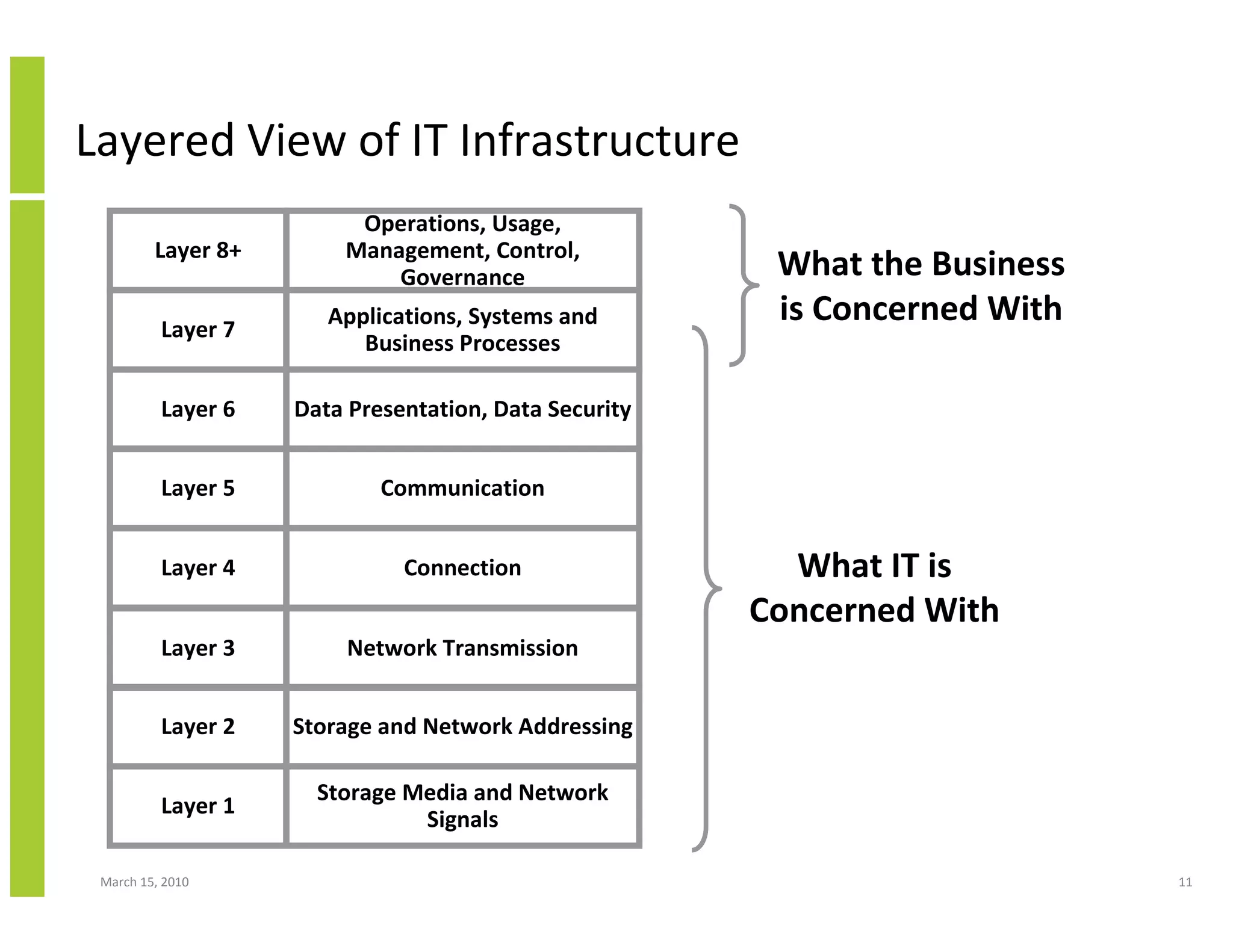
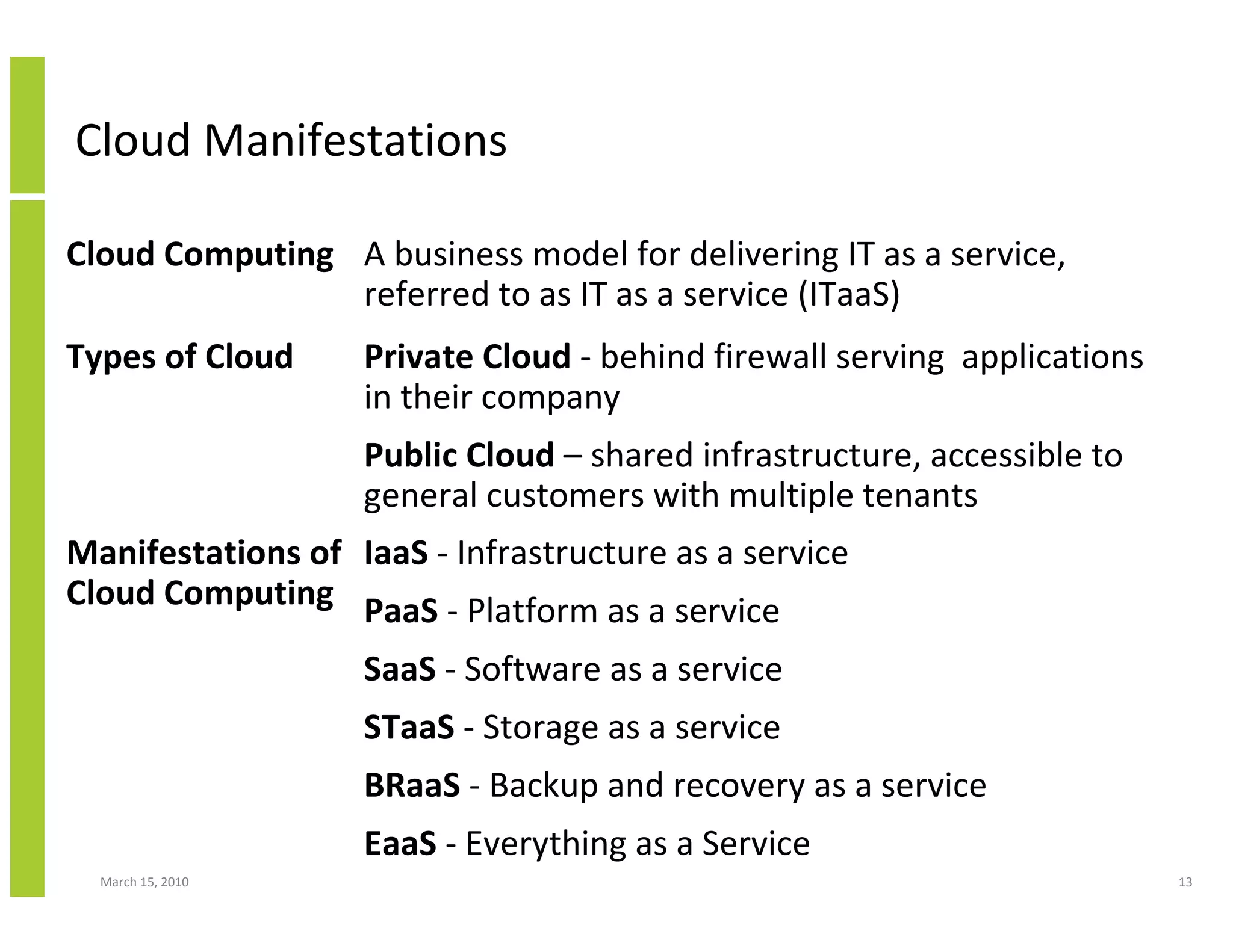
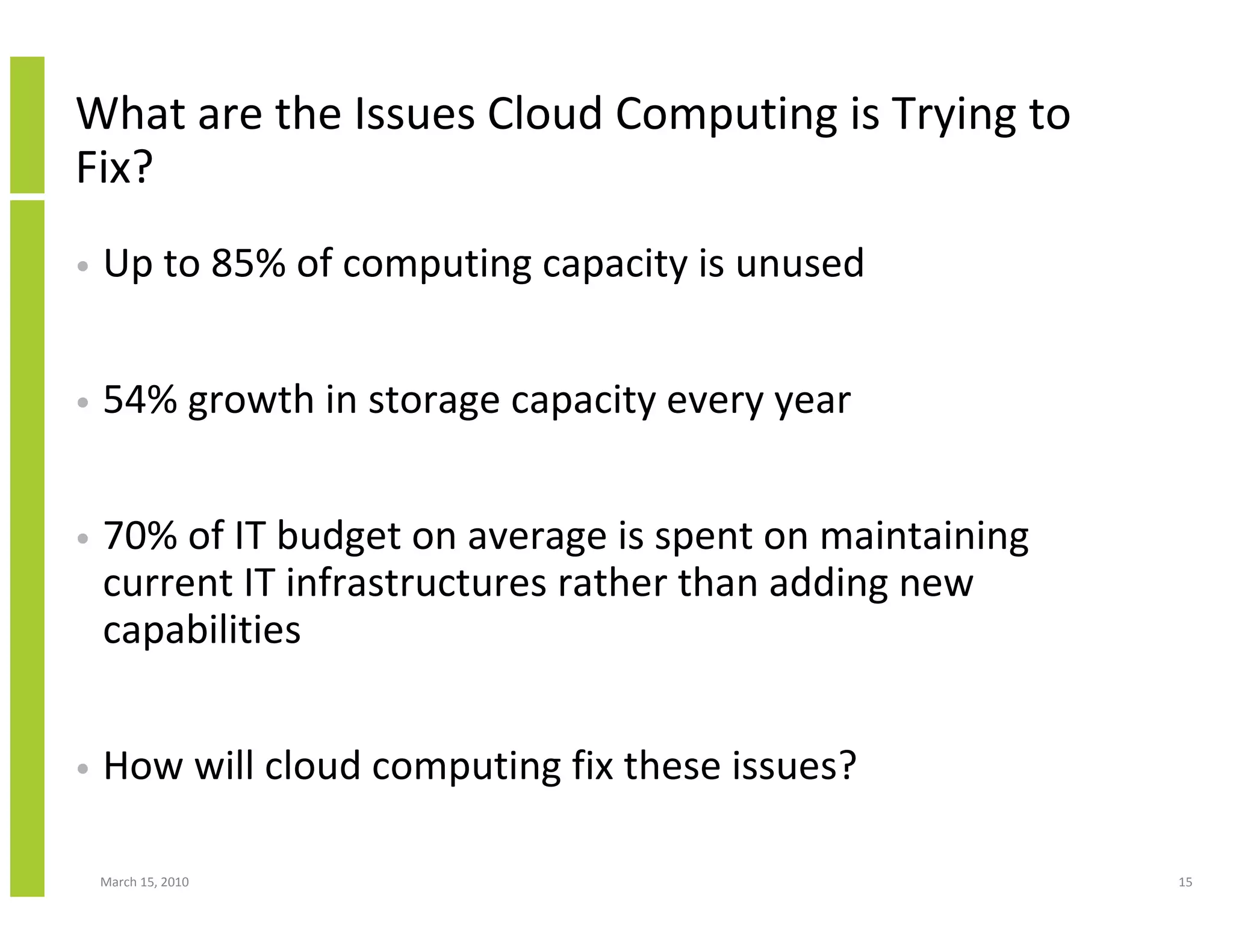
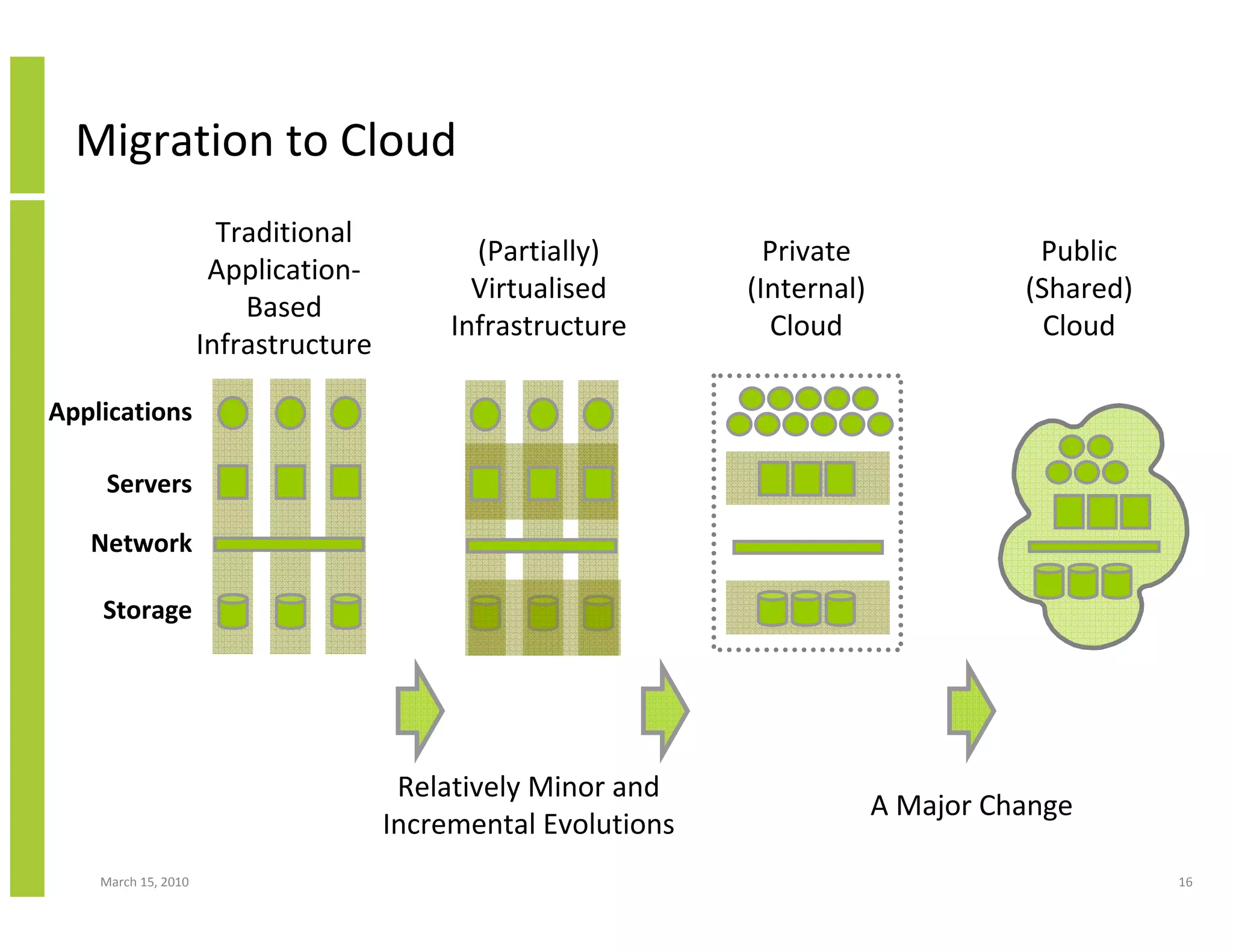
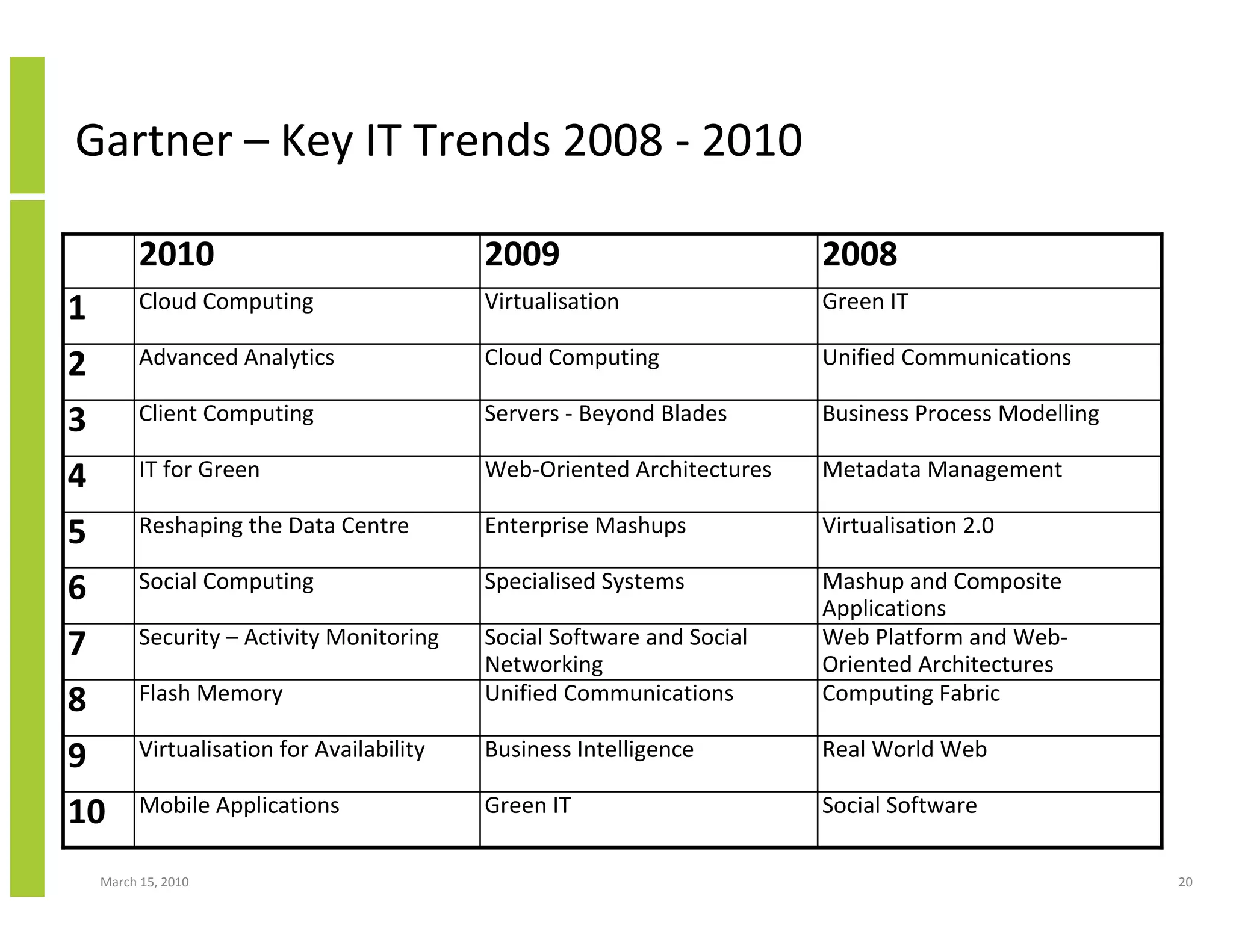
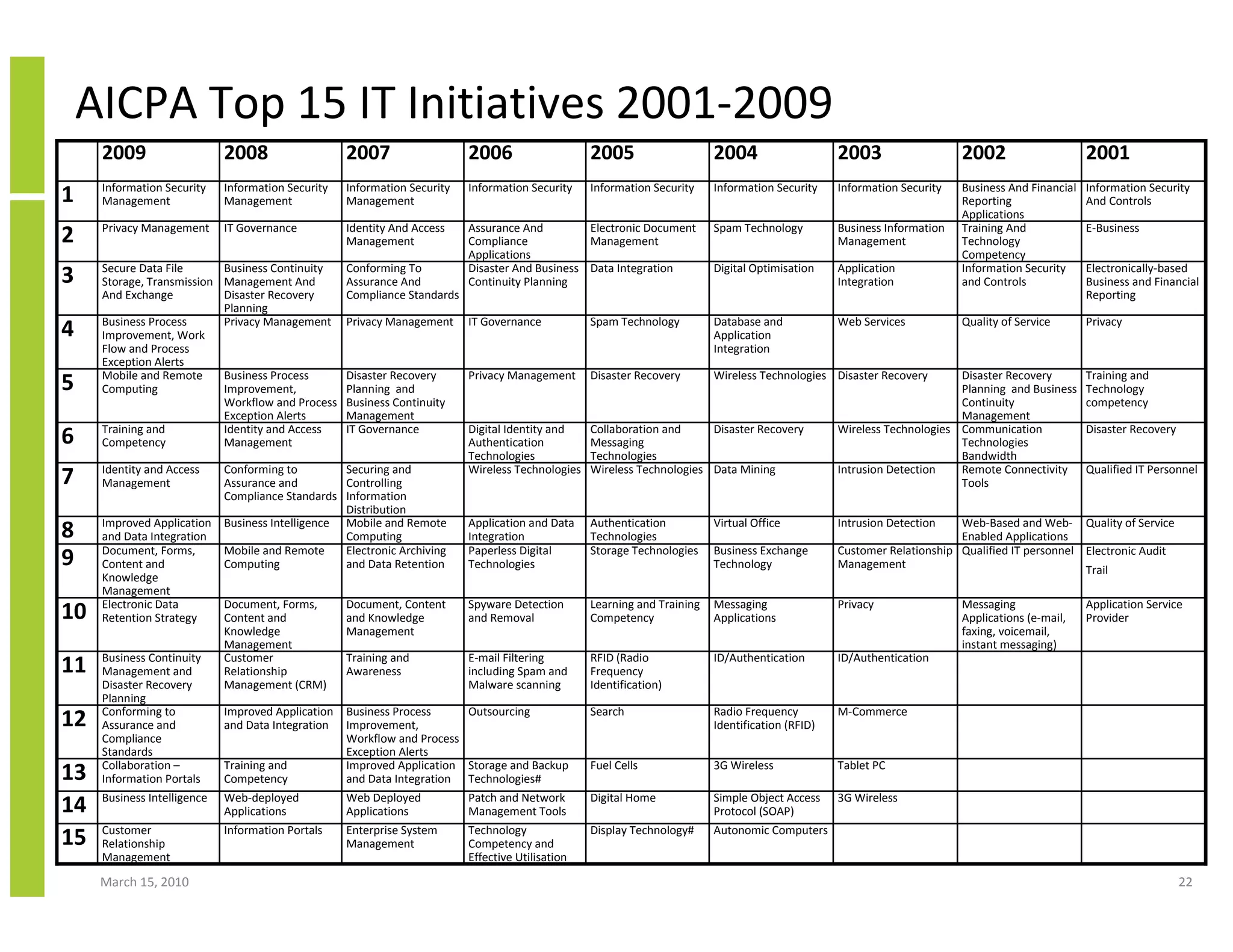
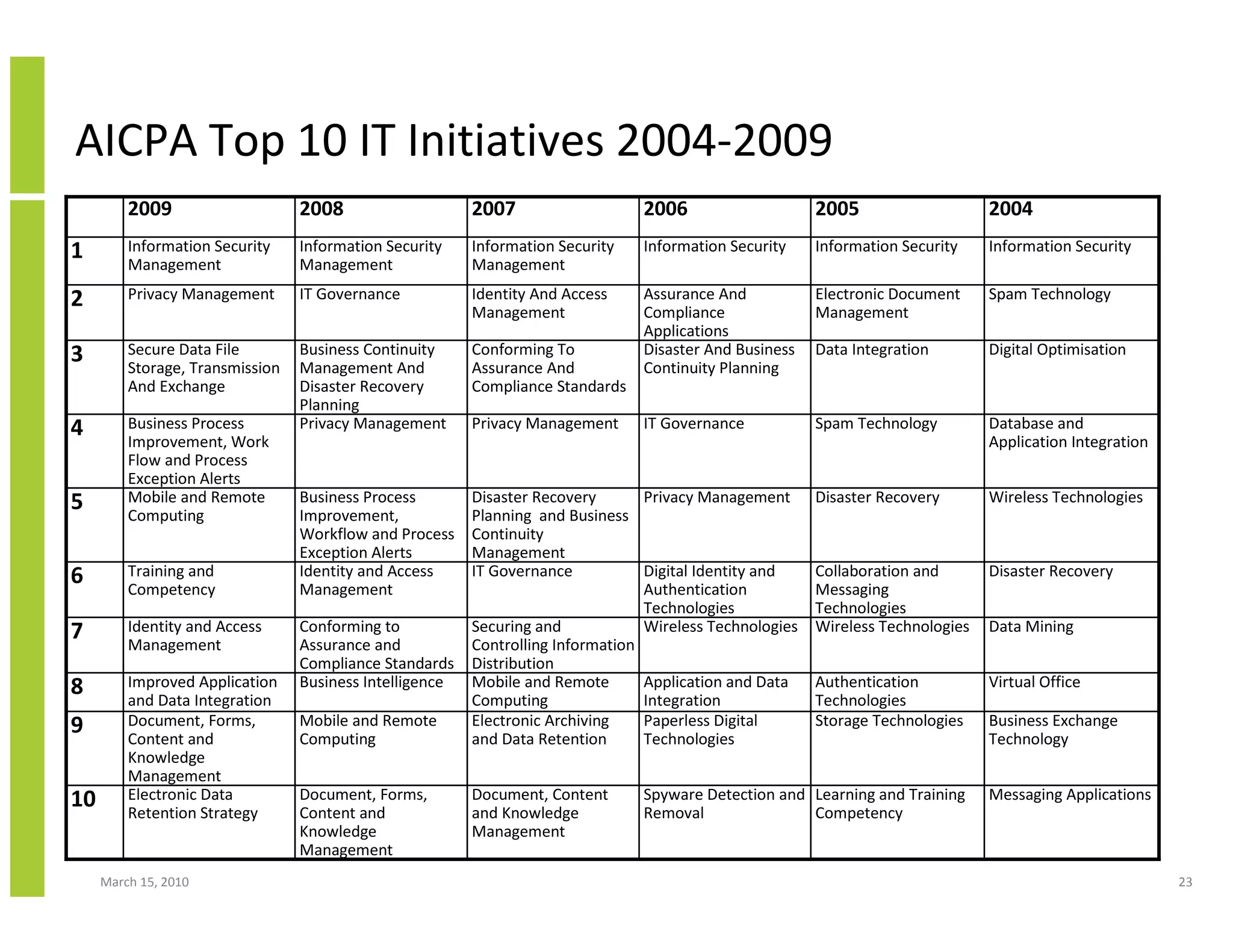
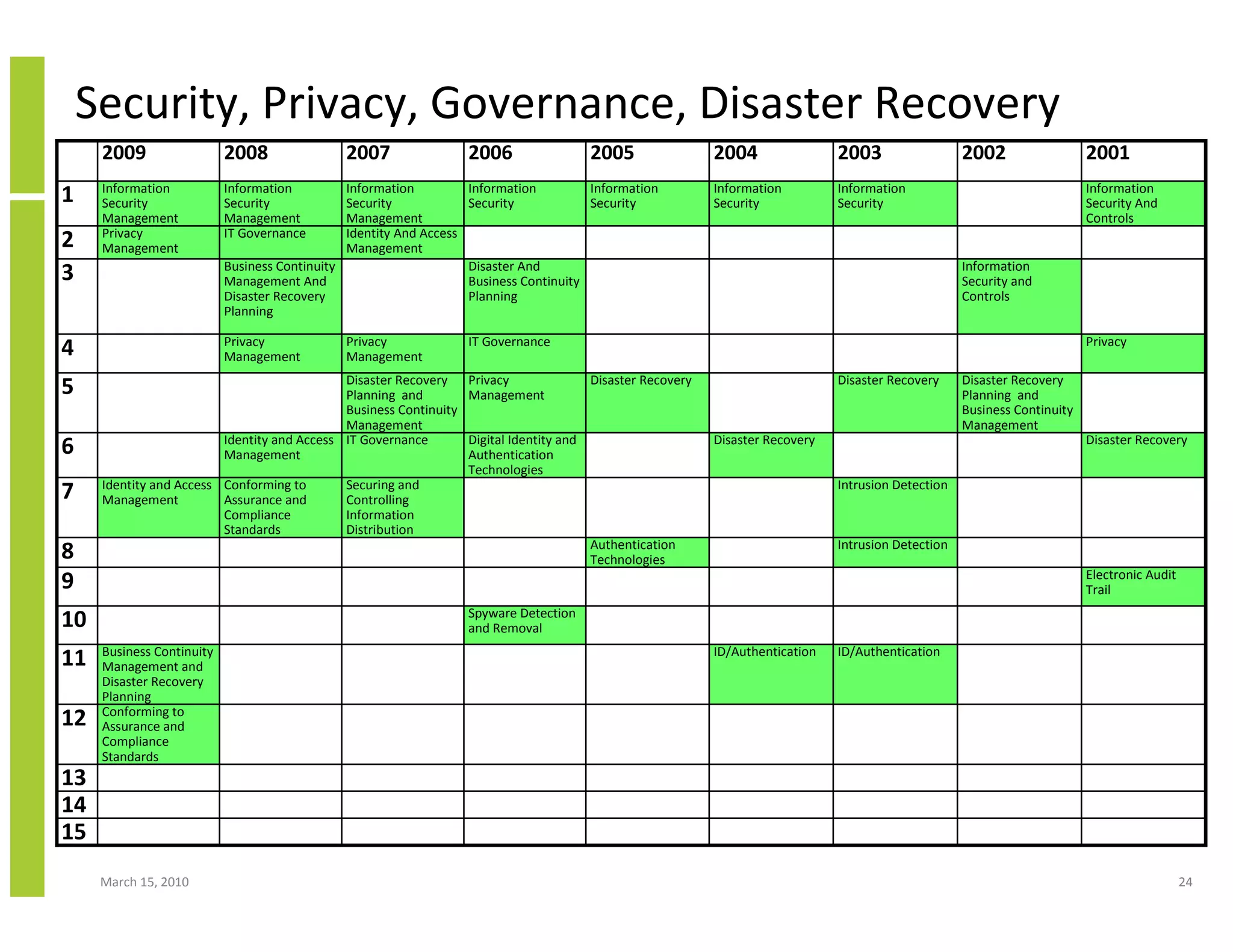
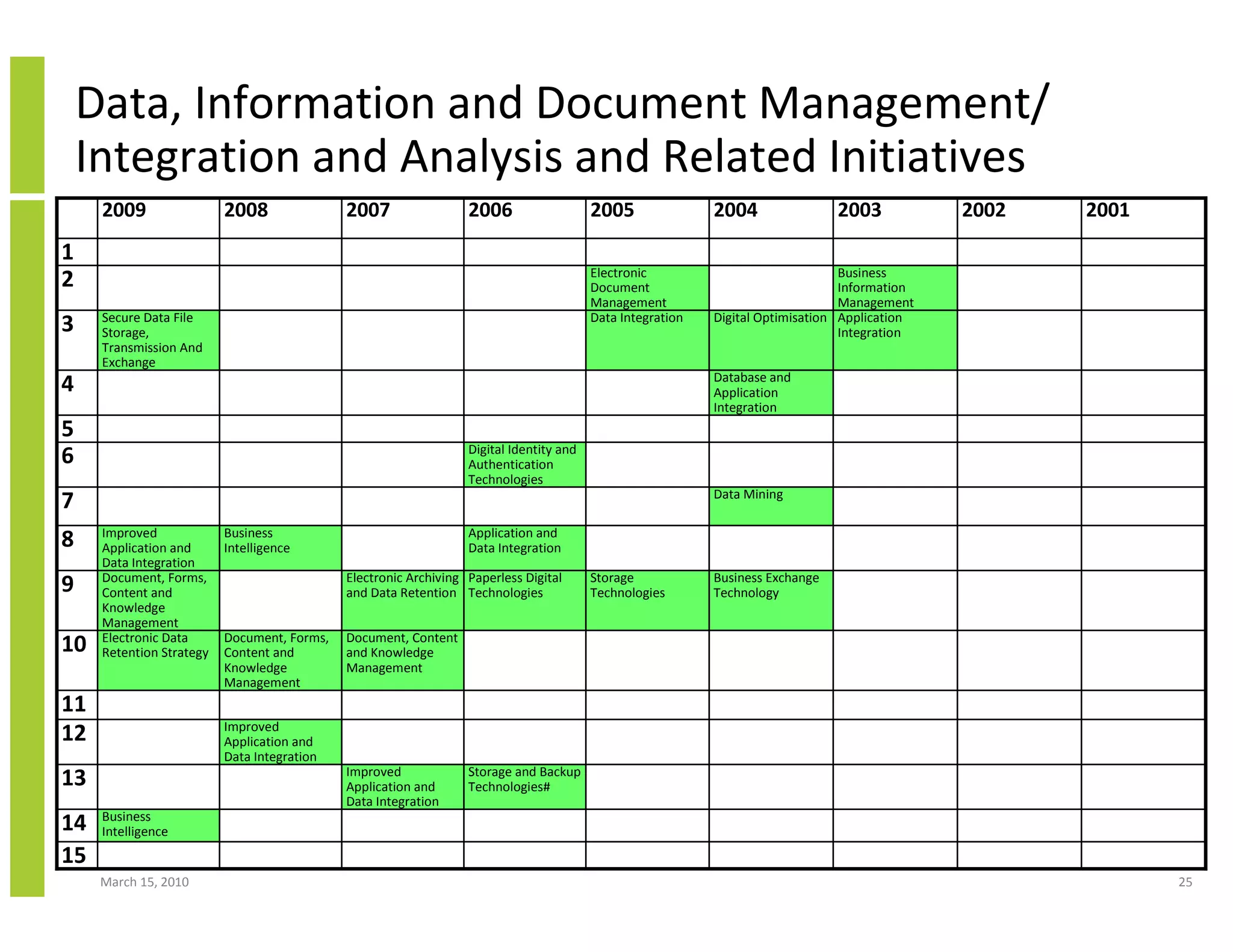
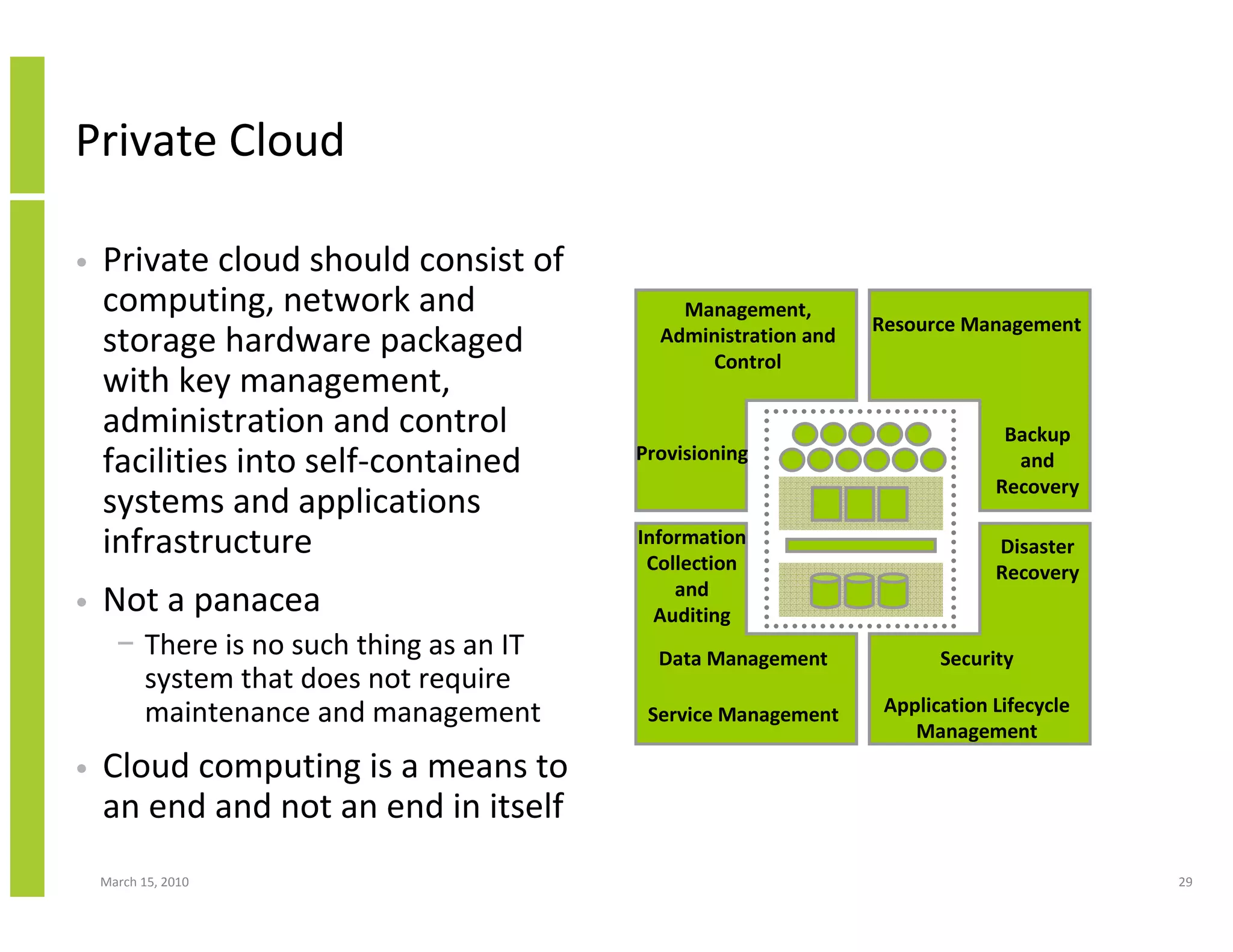
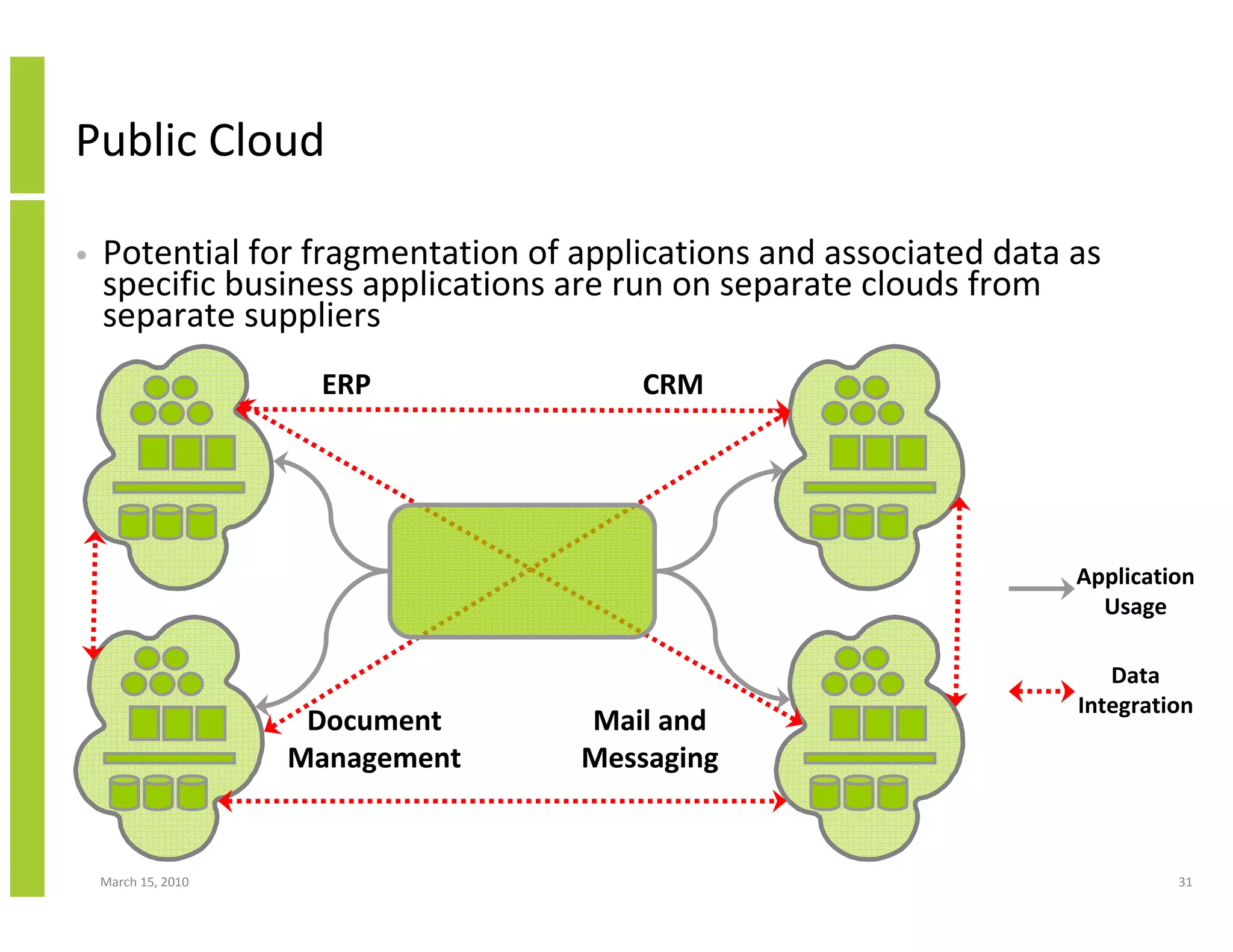
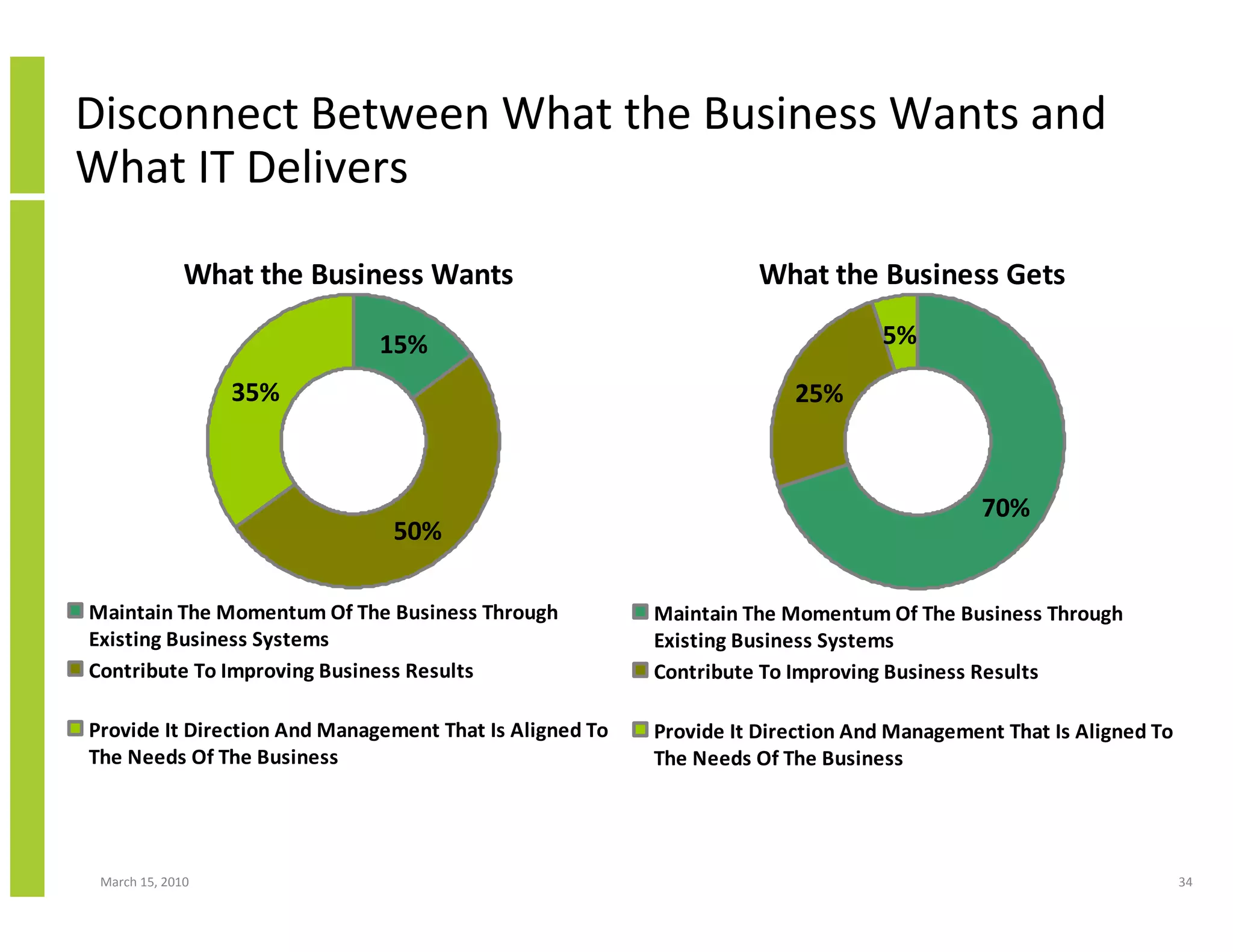
The document discusses trends in cloud computing and information technology. It begins with an overview of cloud computing definitions and manifestations like IaaS, PaaS, SaaS. It then analyzes surveys of IT trends from organizations like AICPA and Gartner. A key difference is that AICPA trends had a more business-oriented focus on issues like security, governance and data management, while Gartner trends were more technical in nature and focused on specific technologies. The document examines how relevant trends are to businesses and how much adoption is driven by various factors like cost savings or keeping up with competitors.