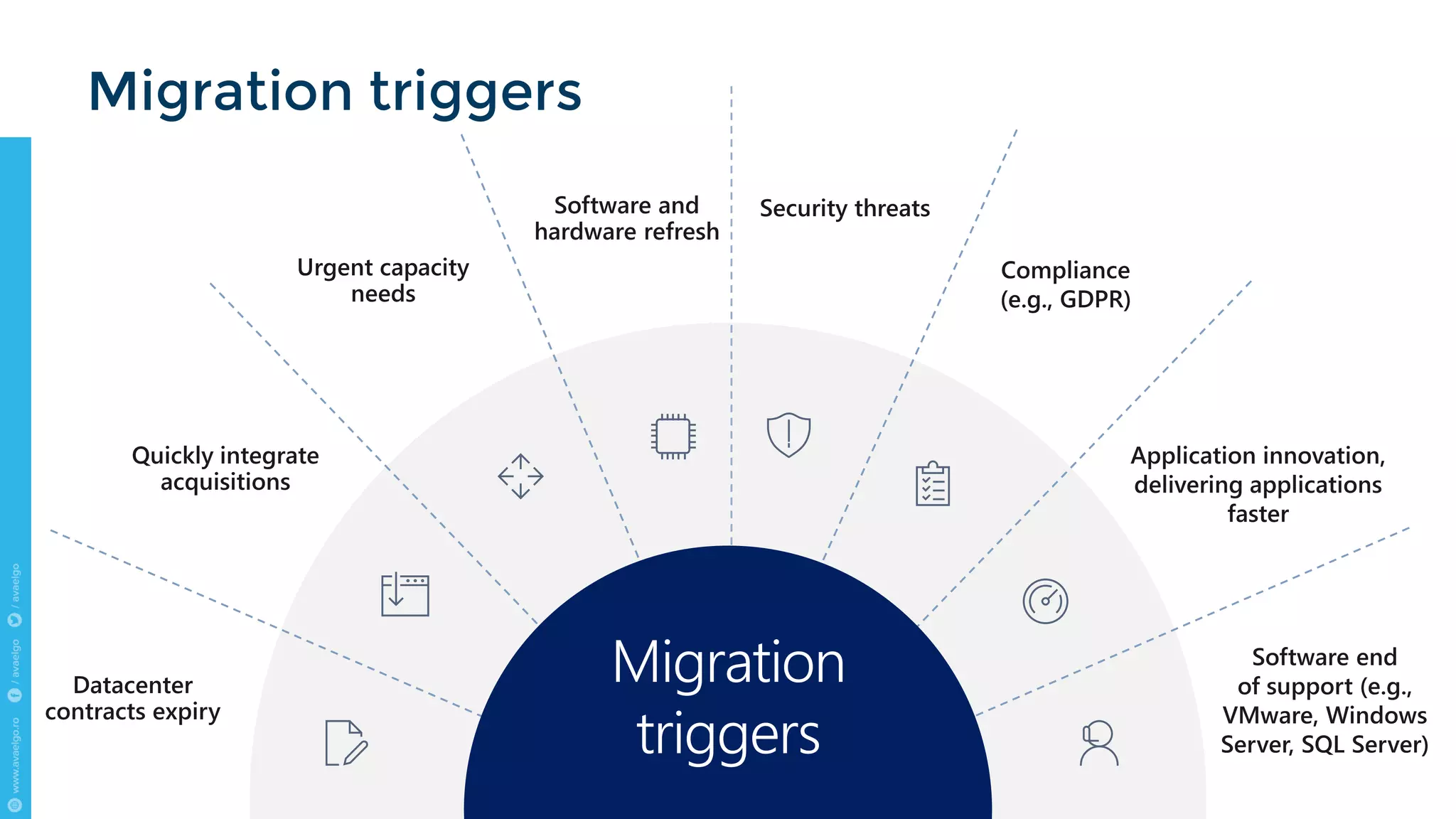
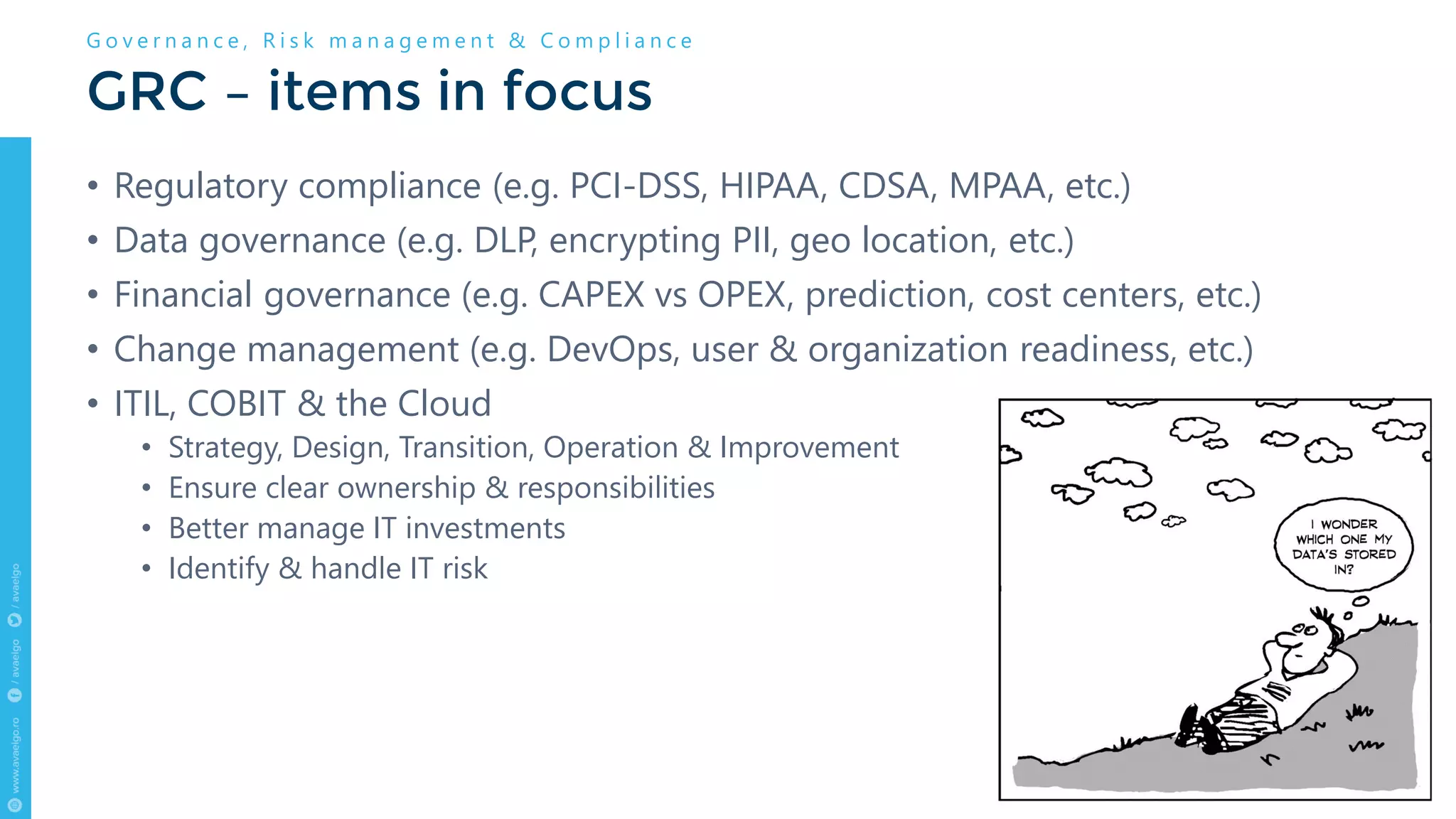
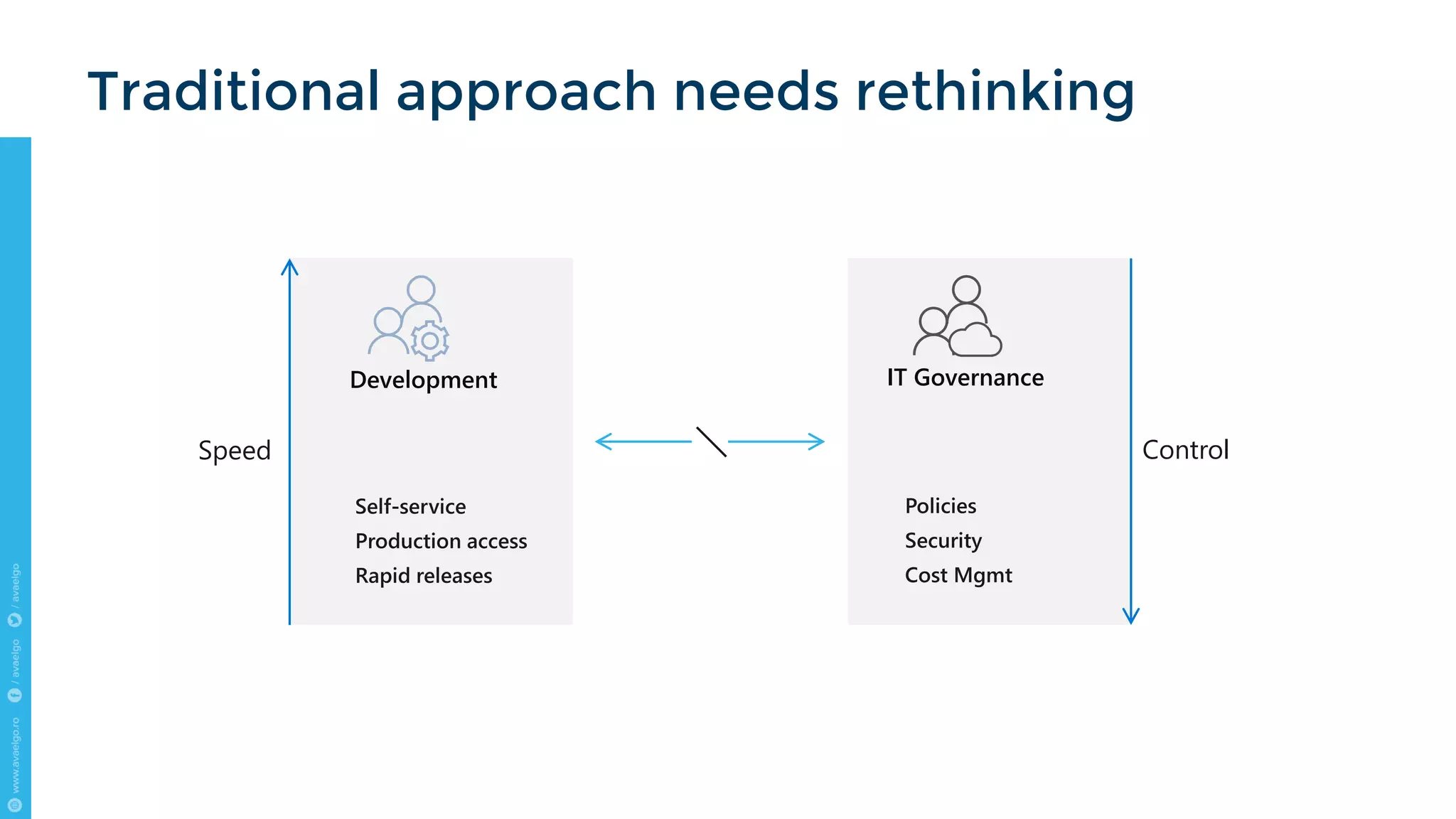
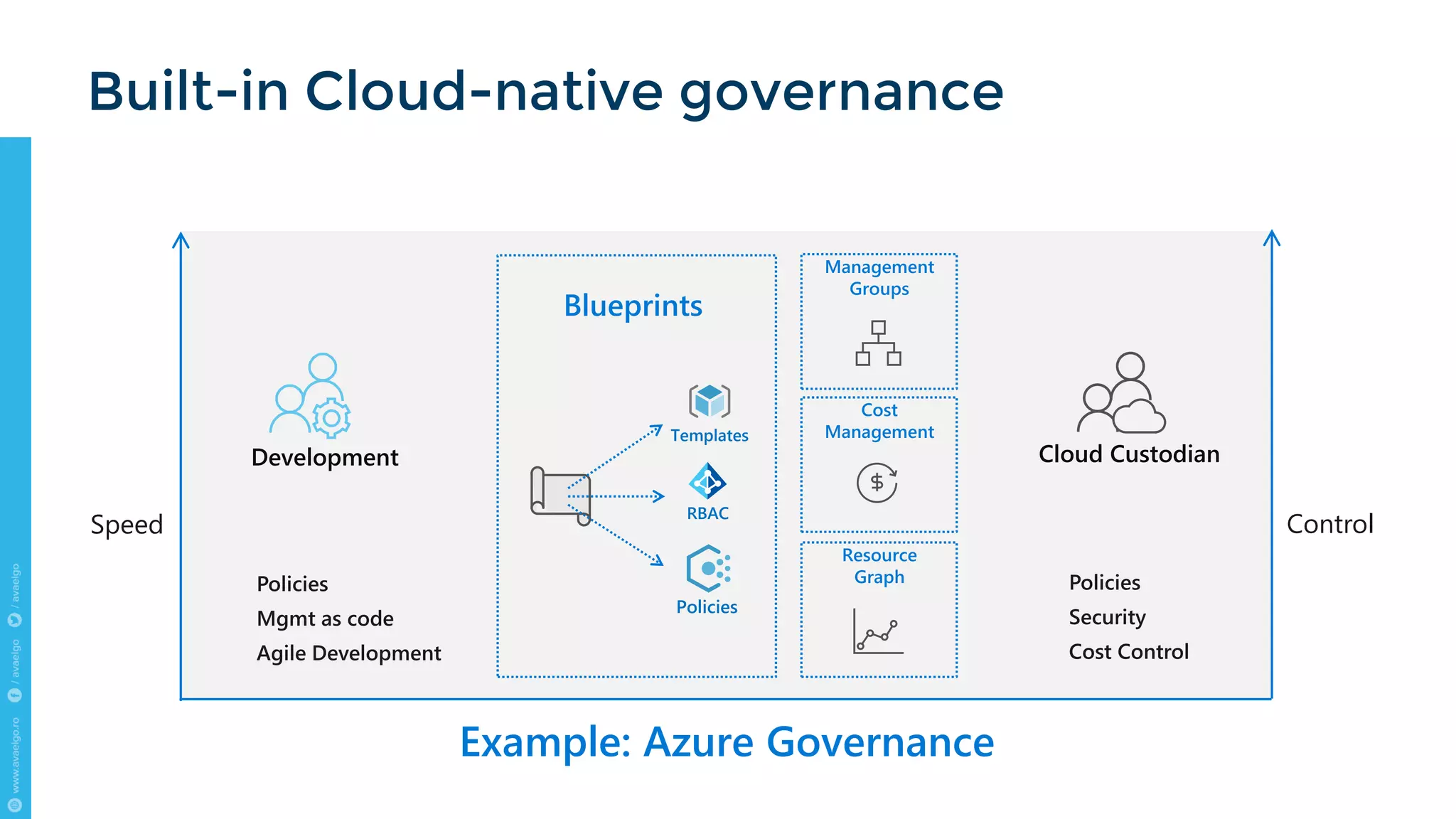
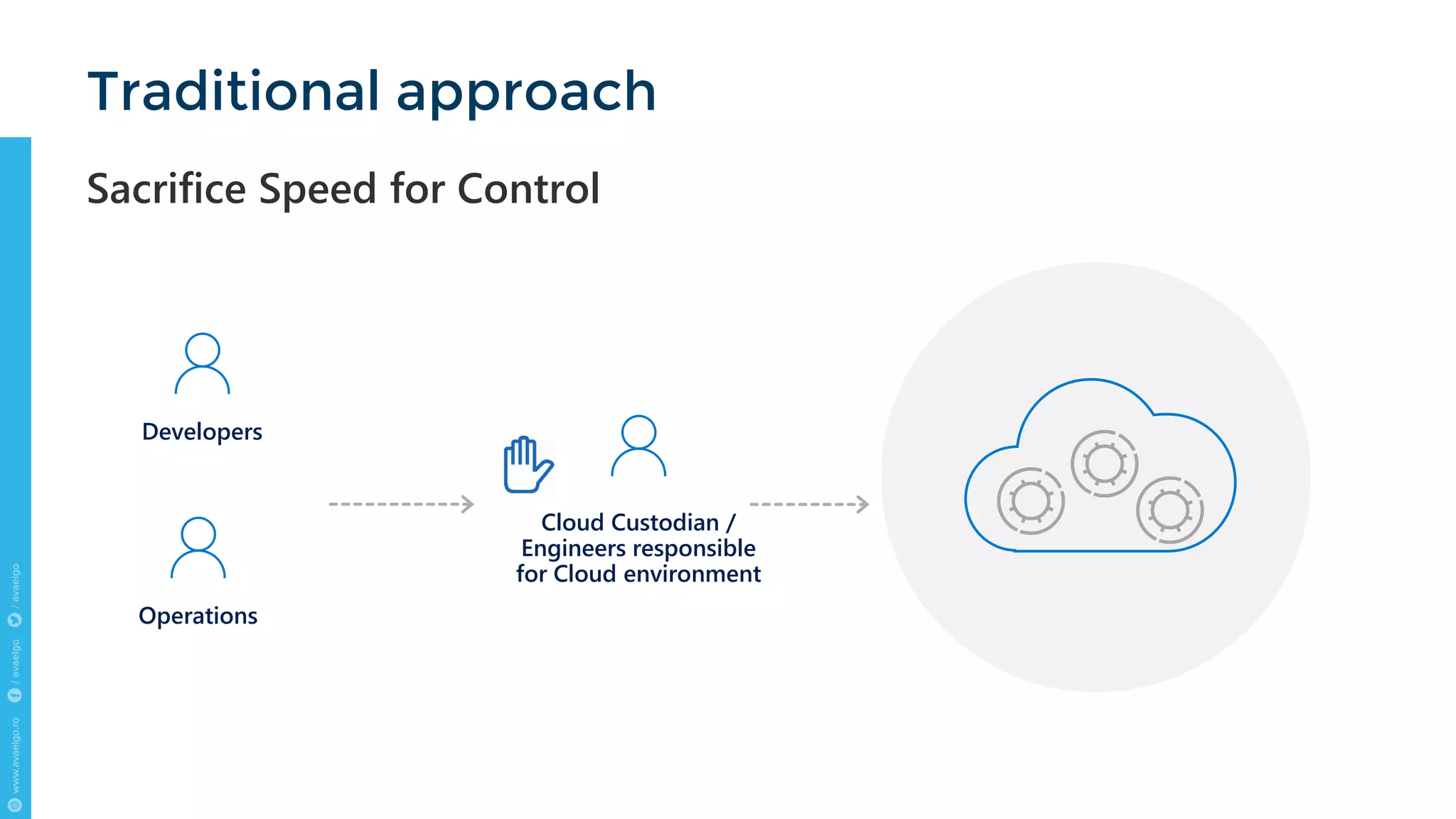
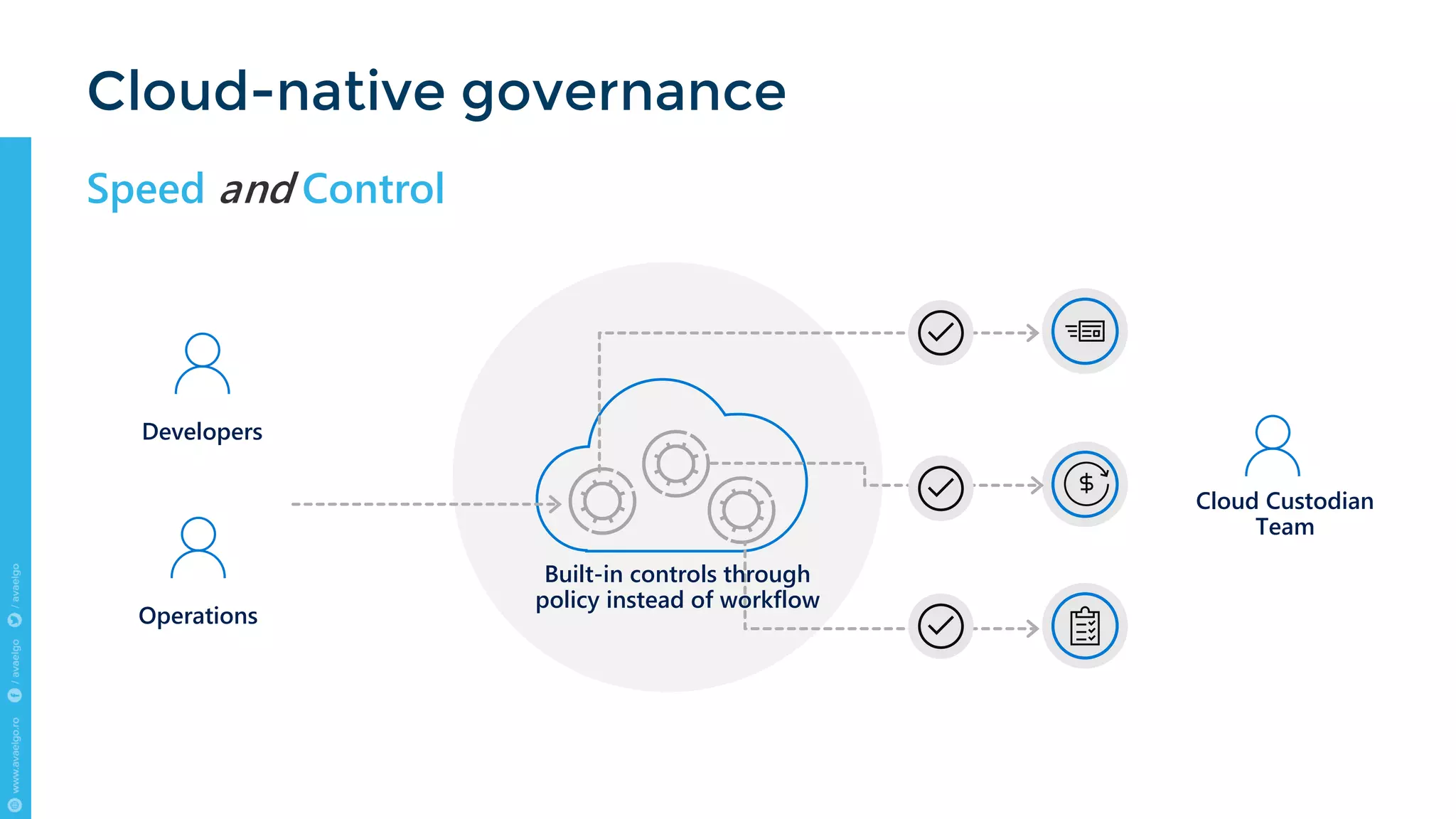
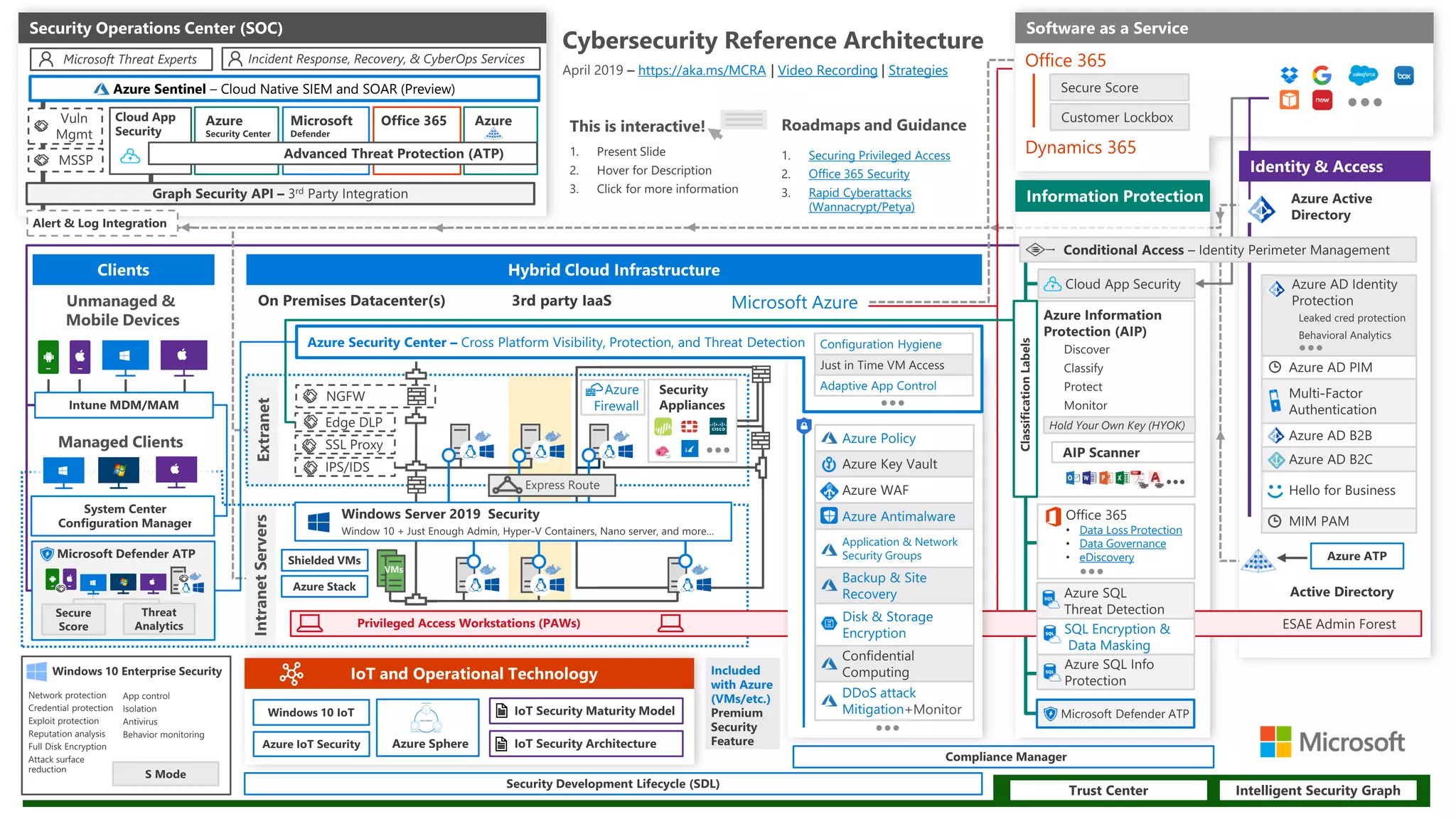
The document outlines key trends and strategies for cloud security and compliance, emphasizing the importance of a solid transition strategy for digital transformation. It highlights challenges companies face during cloud migration and provides insights into governance, risk management, and compliance (GRC) as critical components for success in the cloud environment. Additionally, the document features a case study of Avaelgo and illustrates the role of tools like Microsoft Azure in achieving effective cloud management.