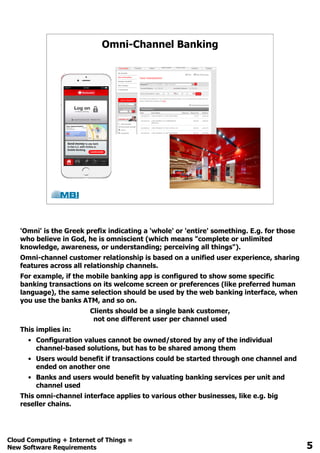
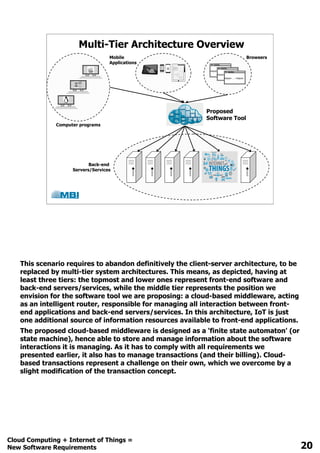
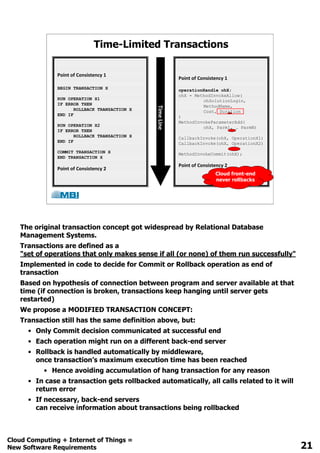
The document discusses the evolution of software requirements driven by advancements in cloud computing and IoT, highlighting the rapid growth of devices and innovative solutions in various industries. It emphasizes the need for global solutions, gradual version migration, and the API economy as businesses seek new profit and market opportunities. Additionally, it outlines software development challenges and introduces a cloud-based time-limited transaction manager, including a timeline for its development and patent application.