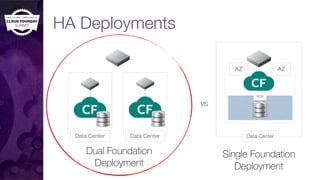
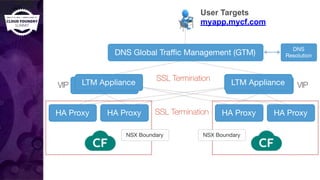
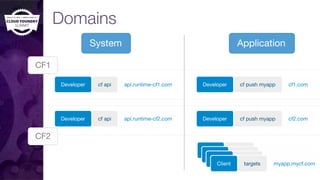
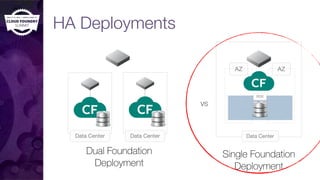
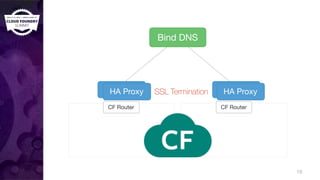
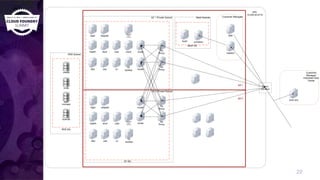
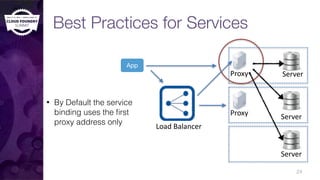
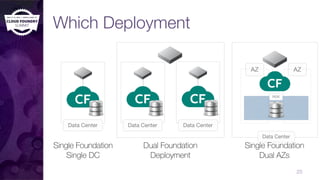
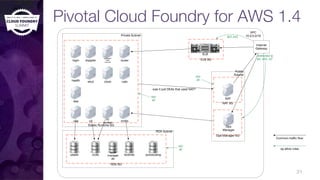
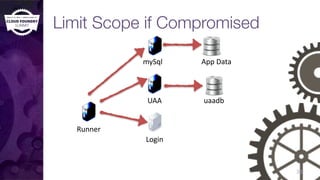
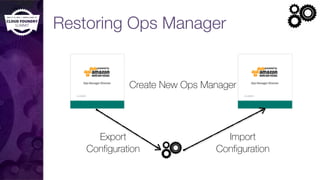
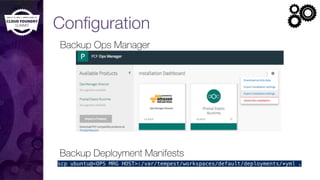
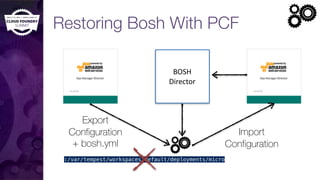
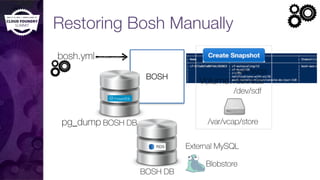
The document discusses building a robust high availability (HA) infrastructure for Cloud Foundry, emphasizing the importance of performance, reliability, and timely error detection. It covers various deployment scenarios, security measures, and disaster recovery strategies, highlighting the role of critical and less-critical jobs within the architecture. Key takeaways include the necessity of trade-offs in design and the importance of backing up configuration, databases, and blobstores.






















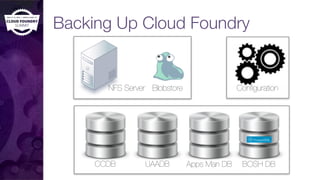




![NFS / Blobstore
✦ Managing Access with ACLs
✦ Create Group Bucket Policy for “Deny DeleteBucket”
✦ Turn on versioning
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Deny",
"Action": [
"s3:DeleteBucket",
"s3:DeleteObjectVersion"
],
"Resource": [
"*"
]
}
]
}](https://image.slidesharecdn.com/cfsummit15ryan2-150515195914-lva1-app6891/85/Cloud-Foundry-Summit-2015-Building-a-Robust-Cloud-Foundry-HA-Security-and-DR-46-320.jpg)


