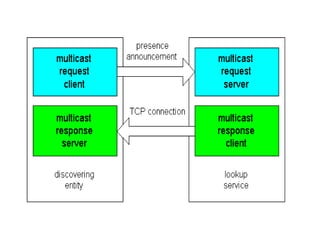
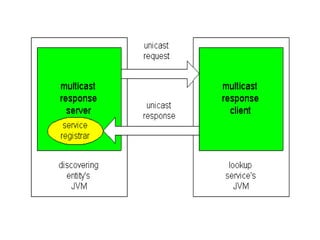
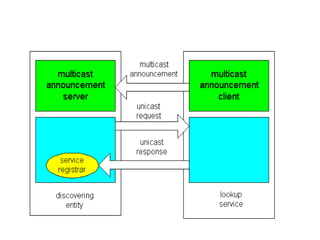
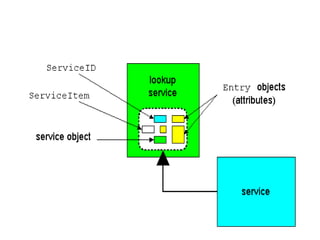
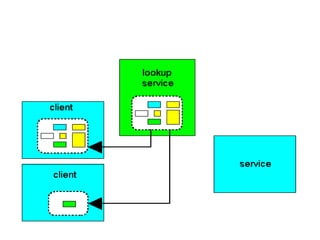
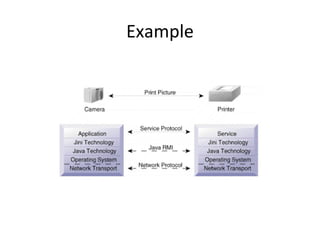
Jini is a technology that enables flexible and adaptive distributed computing by allowing devices and services to dynamically join and leave a network. It provides interfaces for discovery, communication and leasing of services. Jini uses Java and object serialization to enable services to be represented as mobile objects that can move across the network. Services register with a lookup service, which clients can then query to locate and utilize services. This allows for plug-and-play functionality without a centralized administrator.