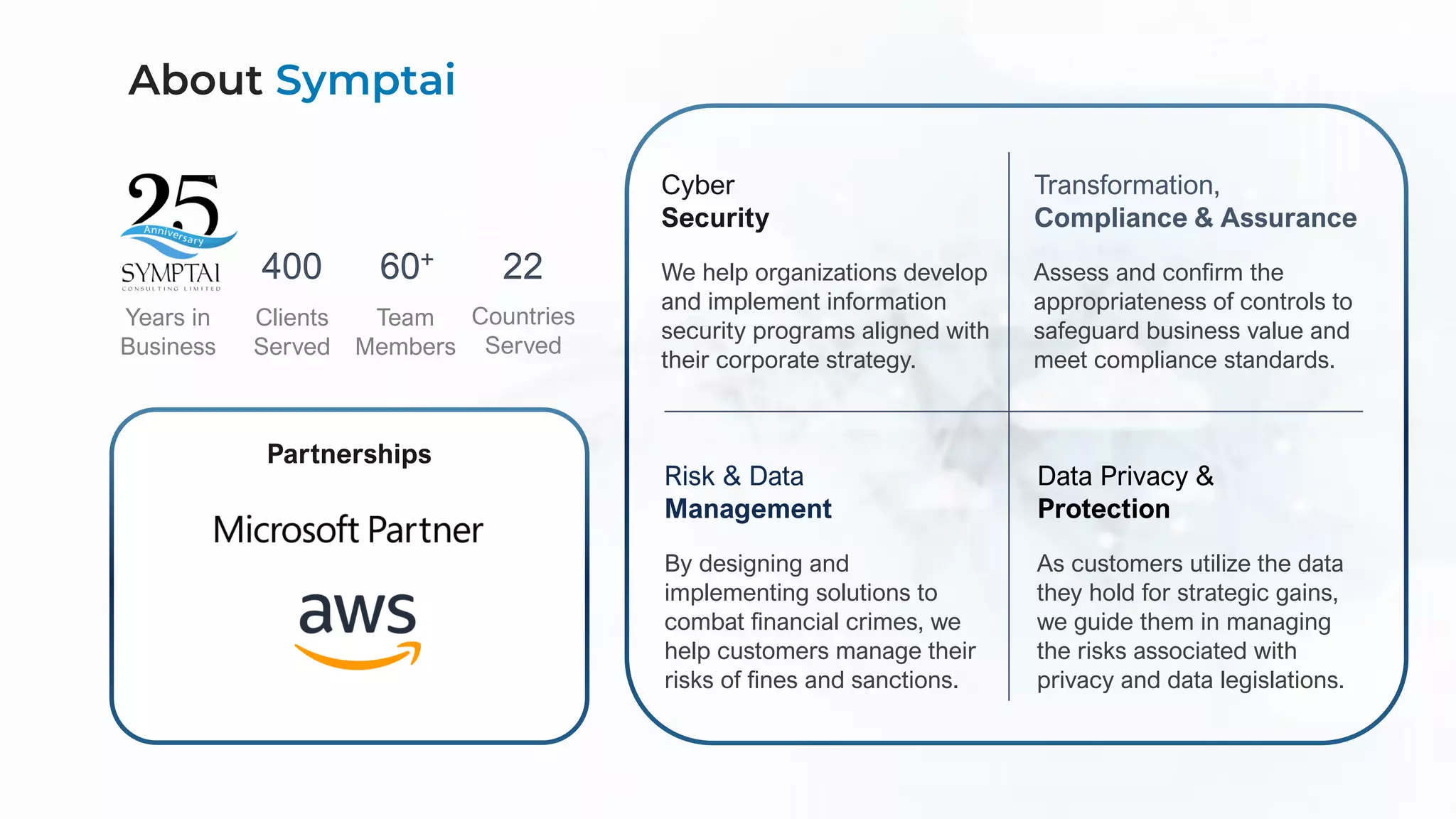
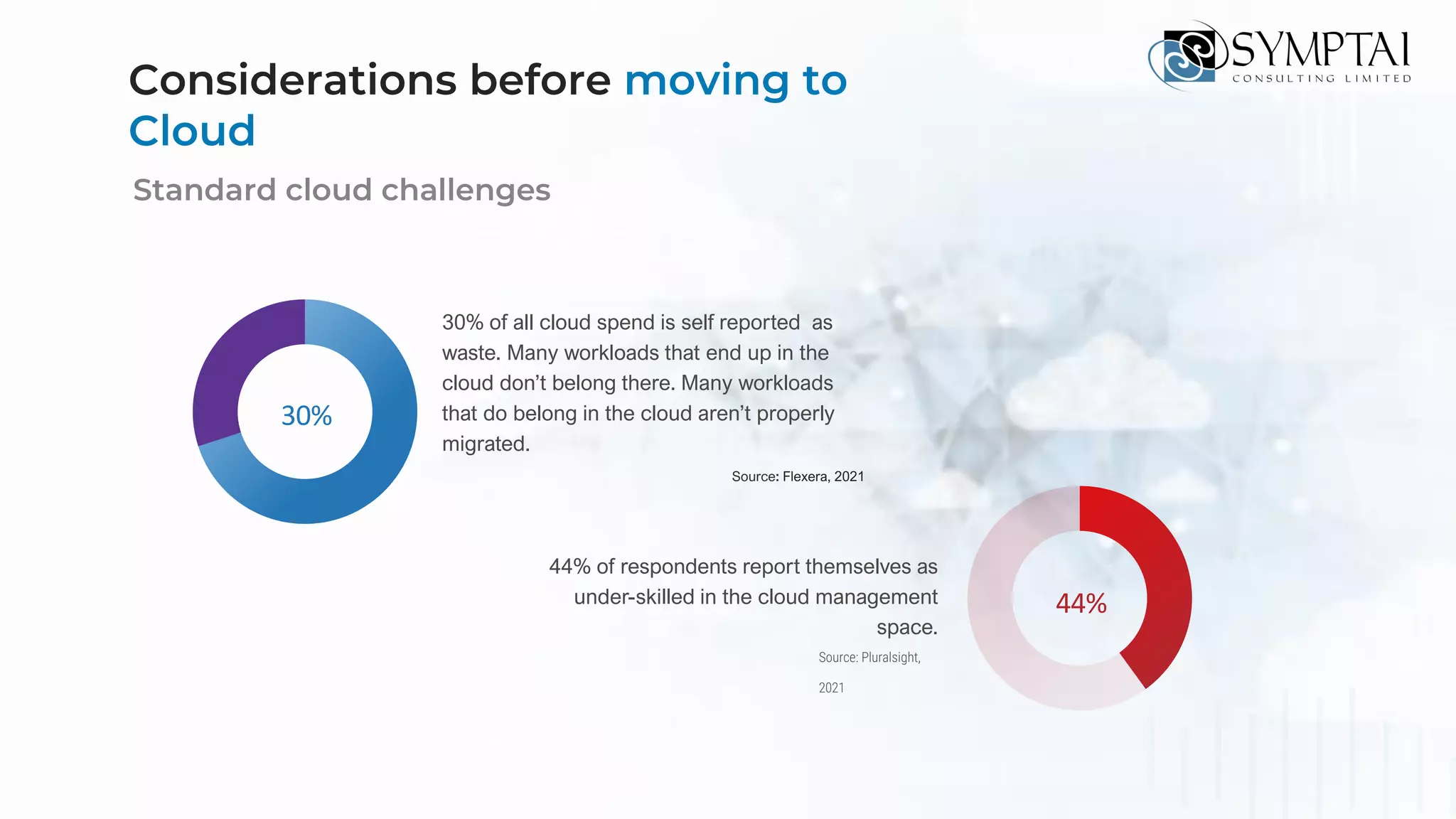
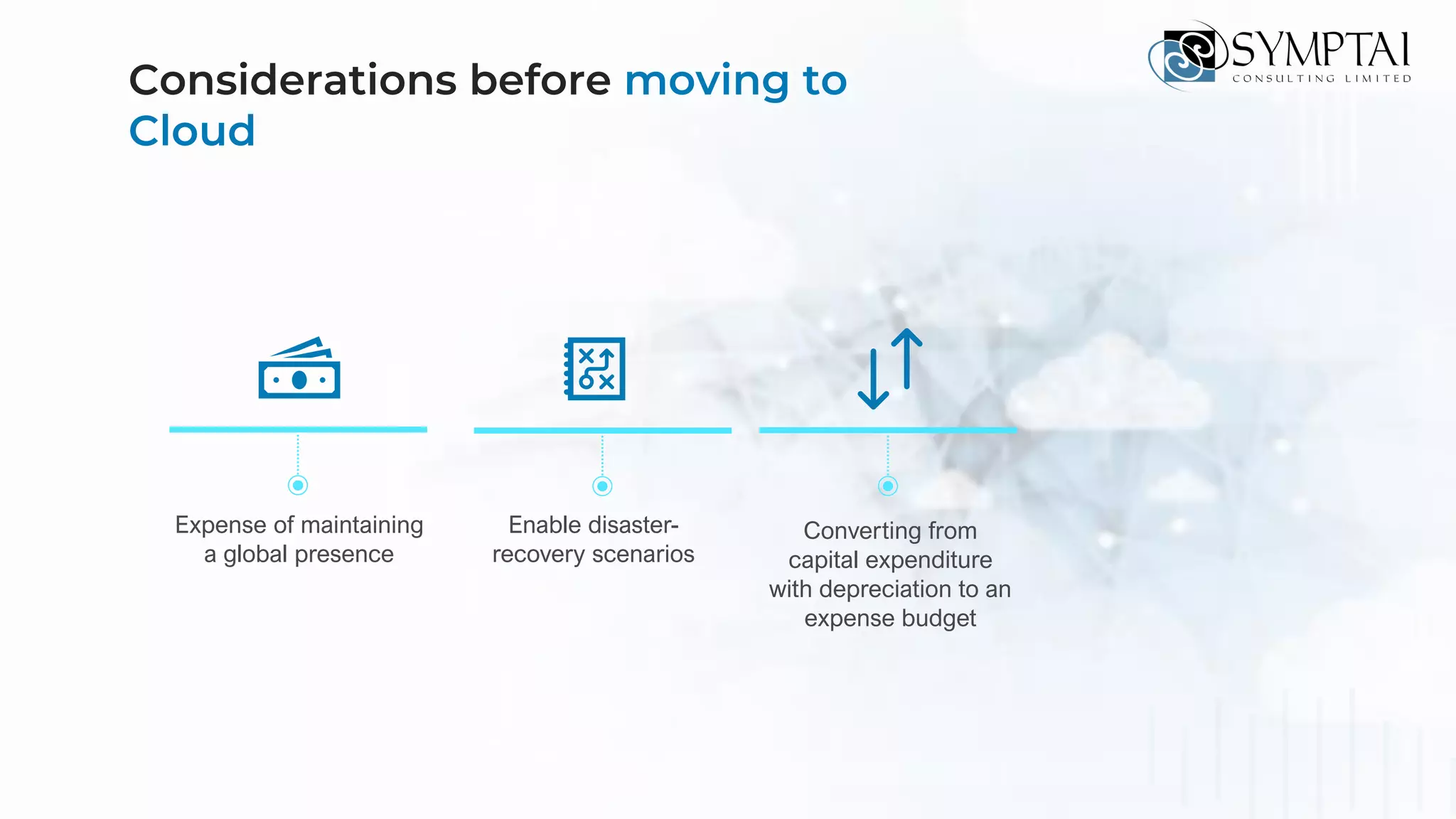
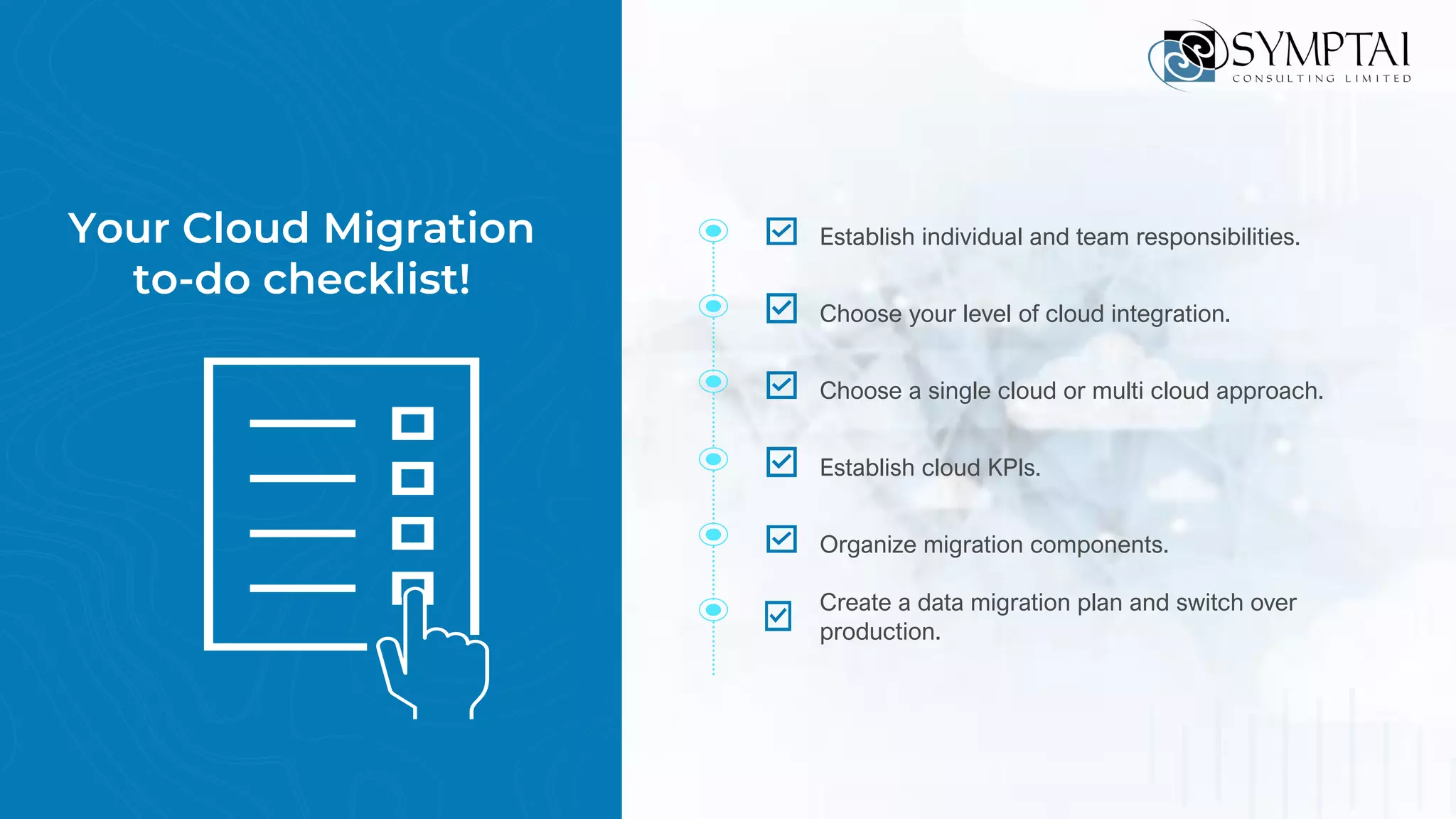
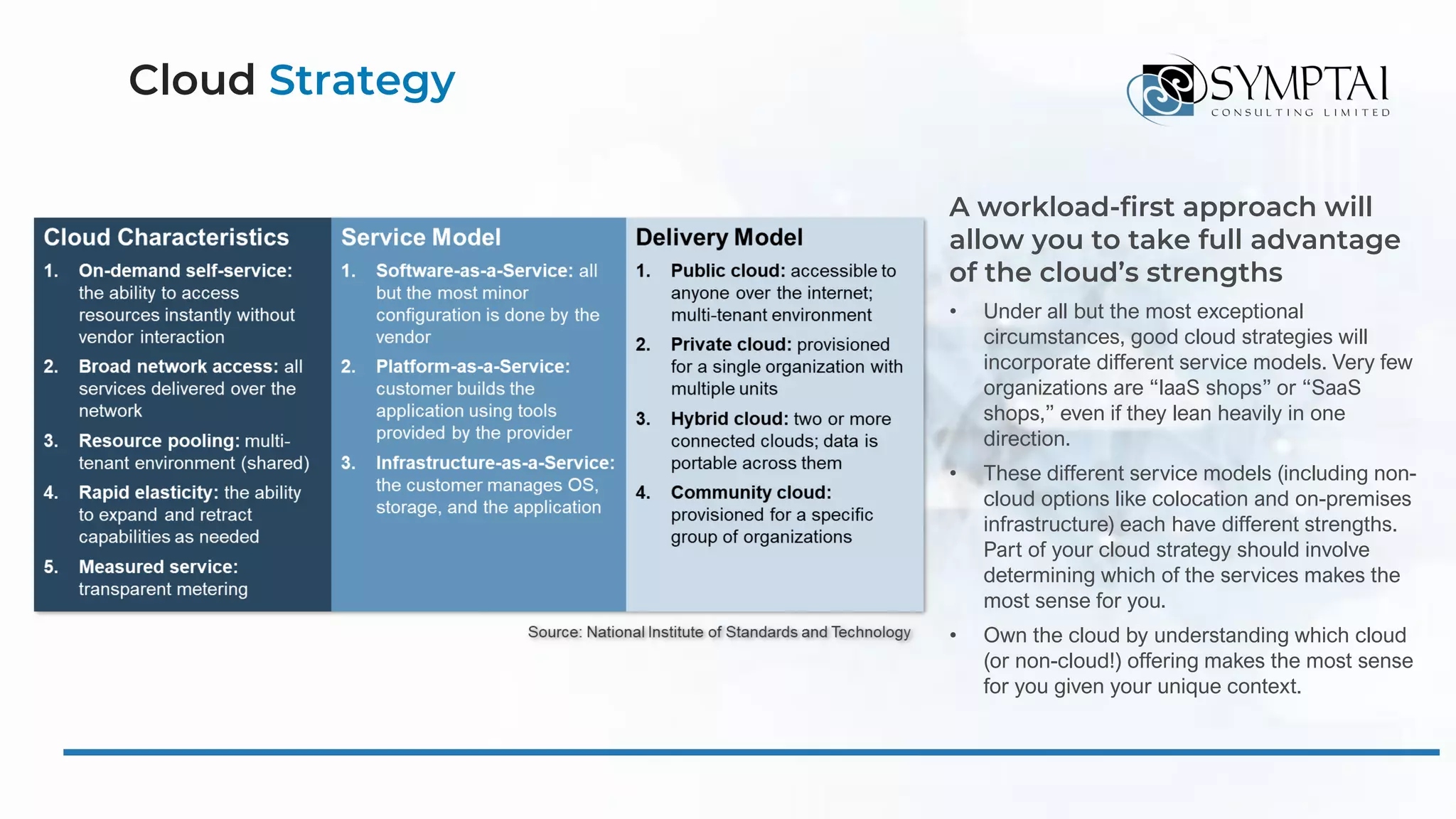
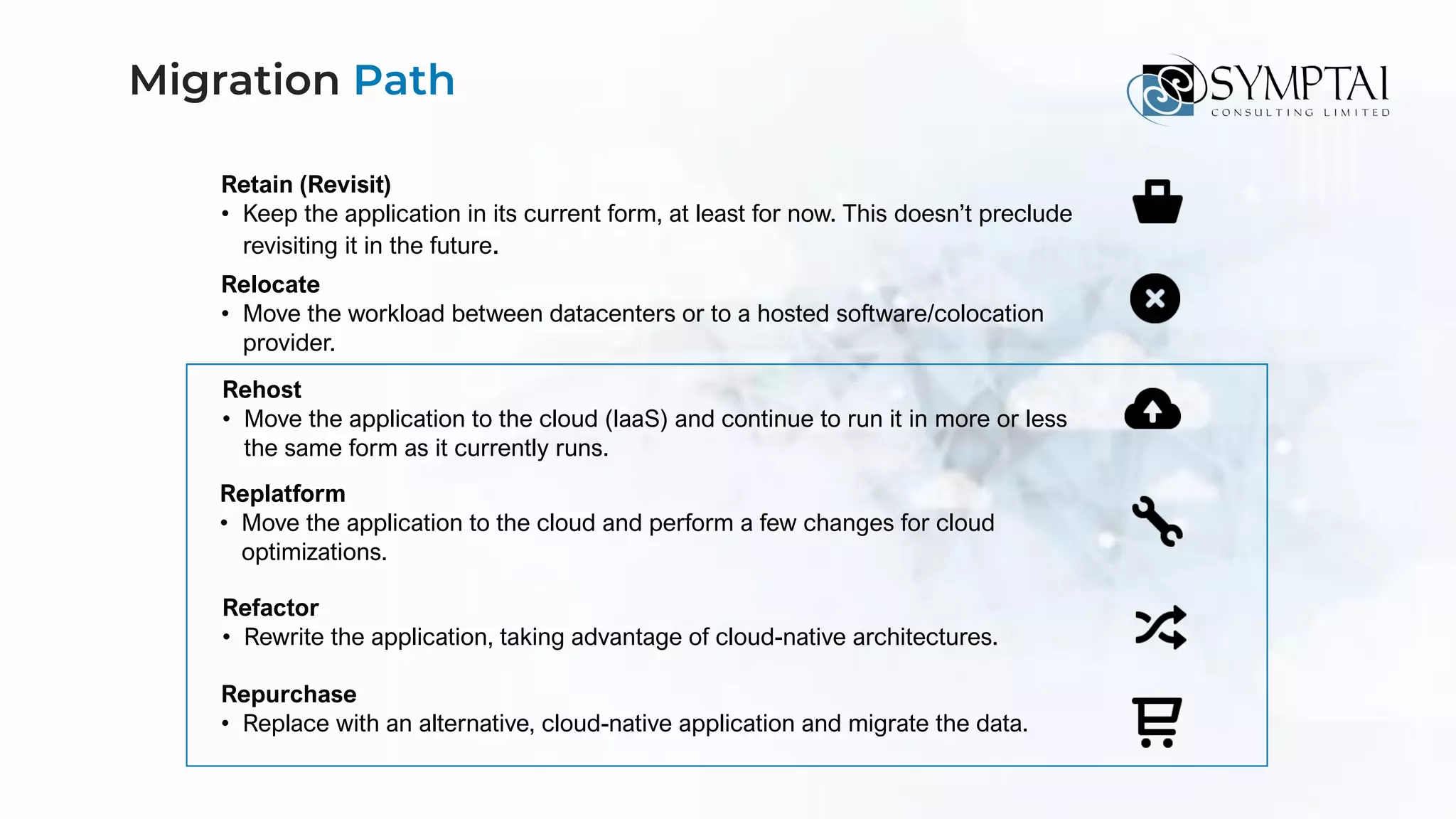
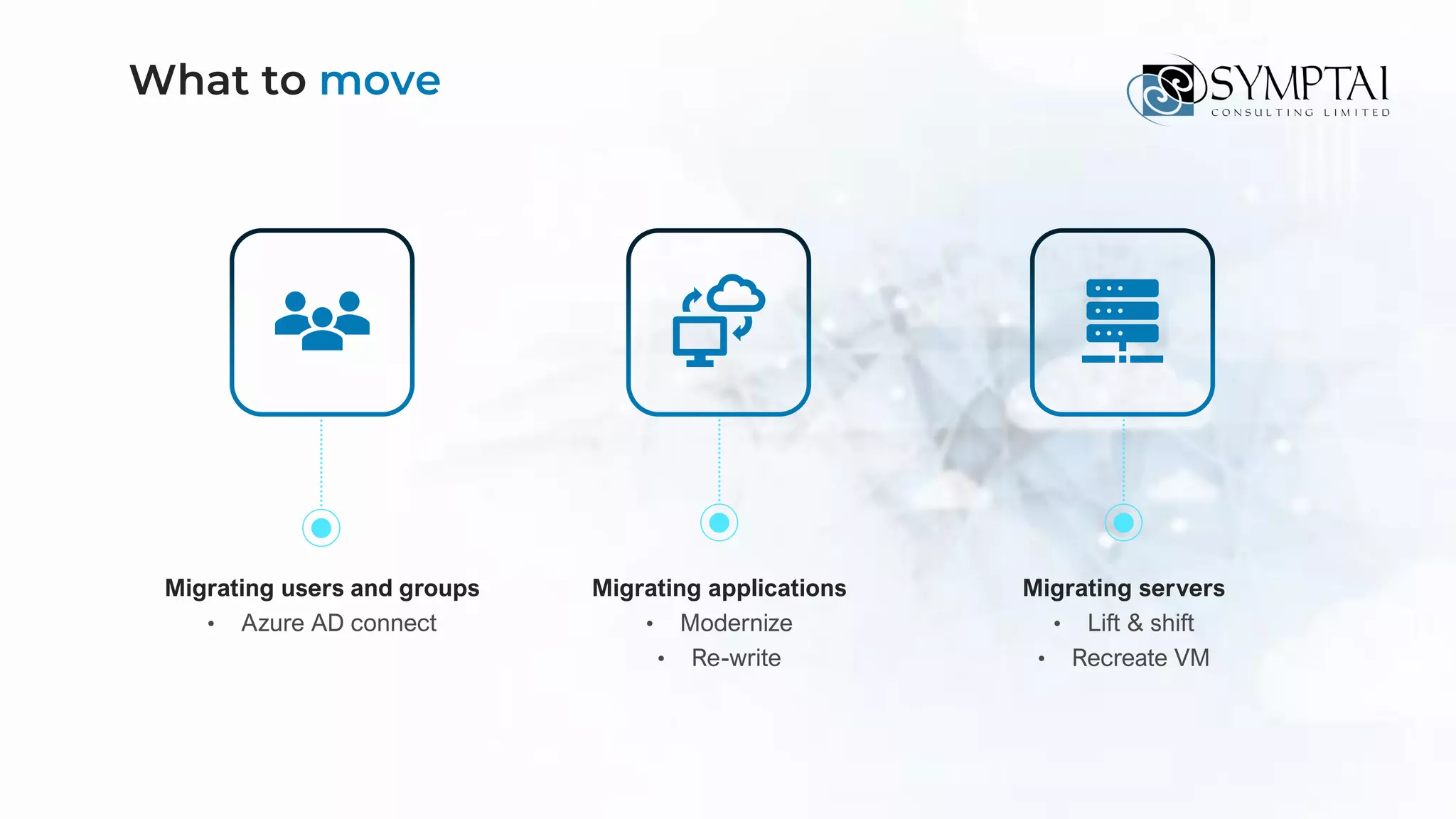
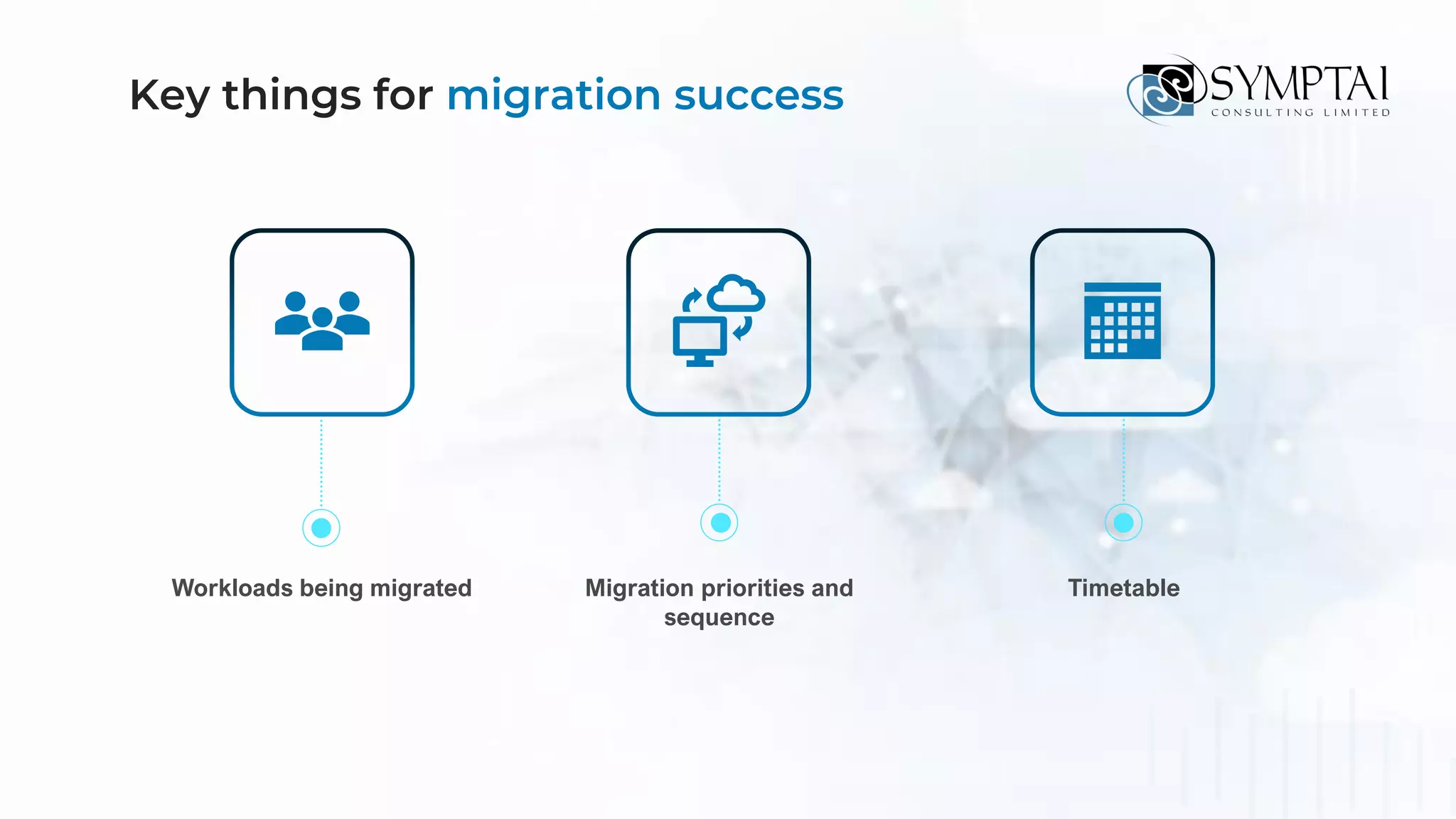
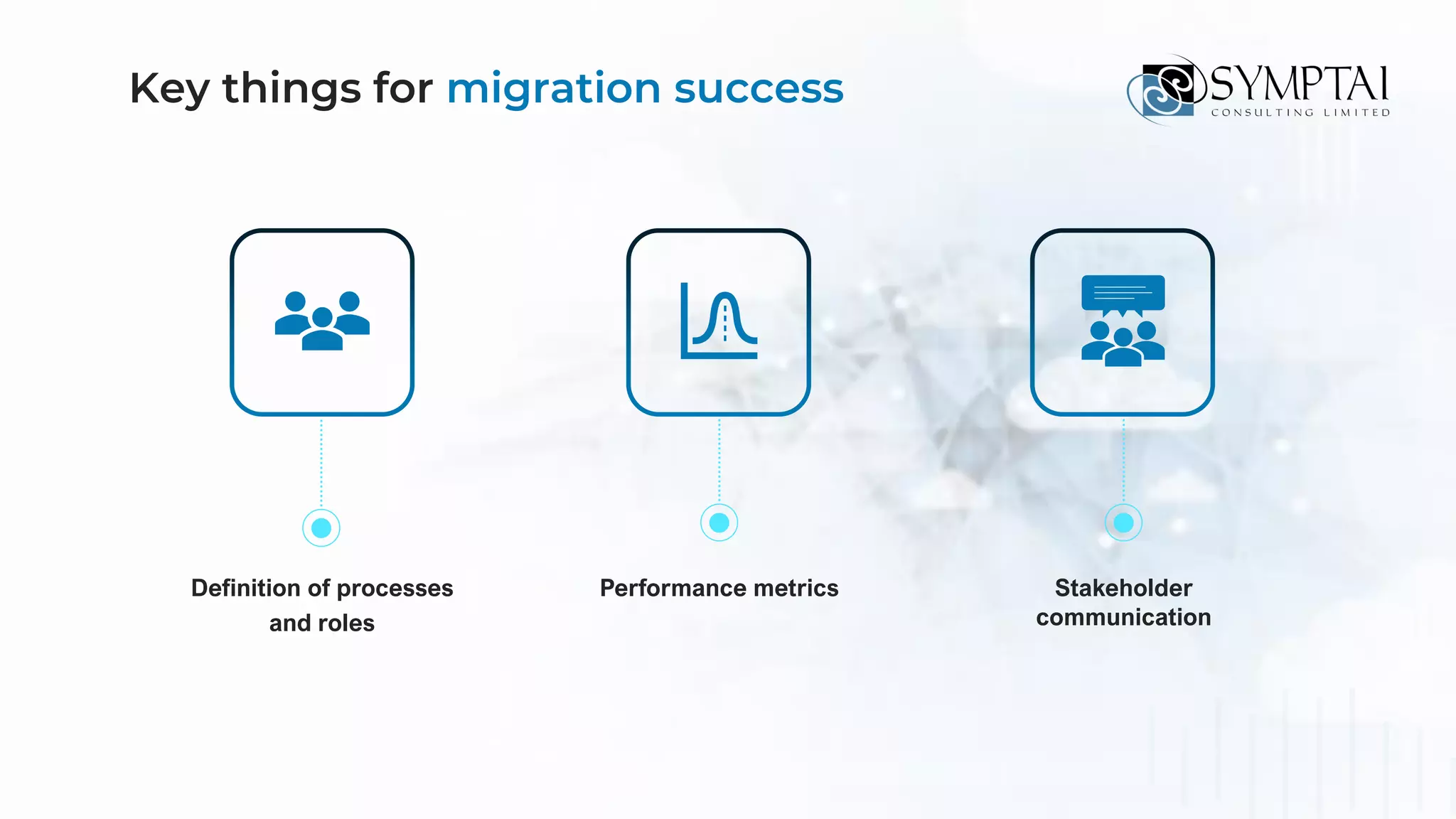
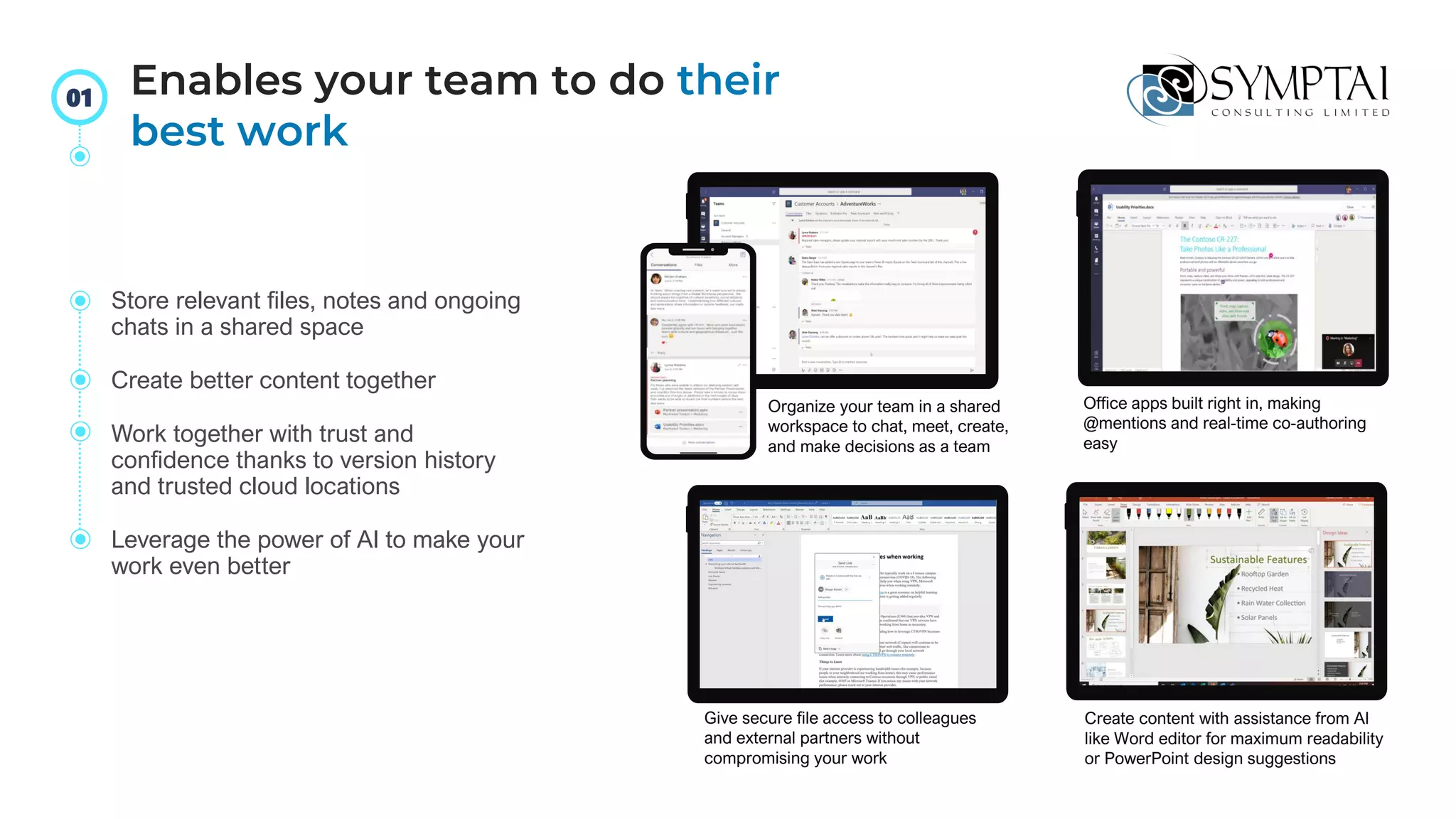
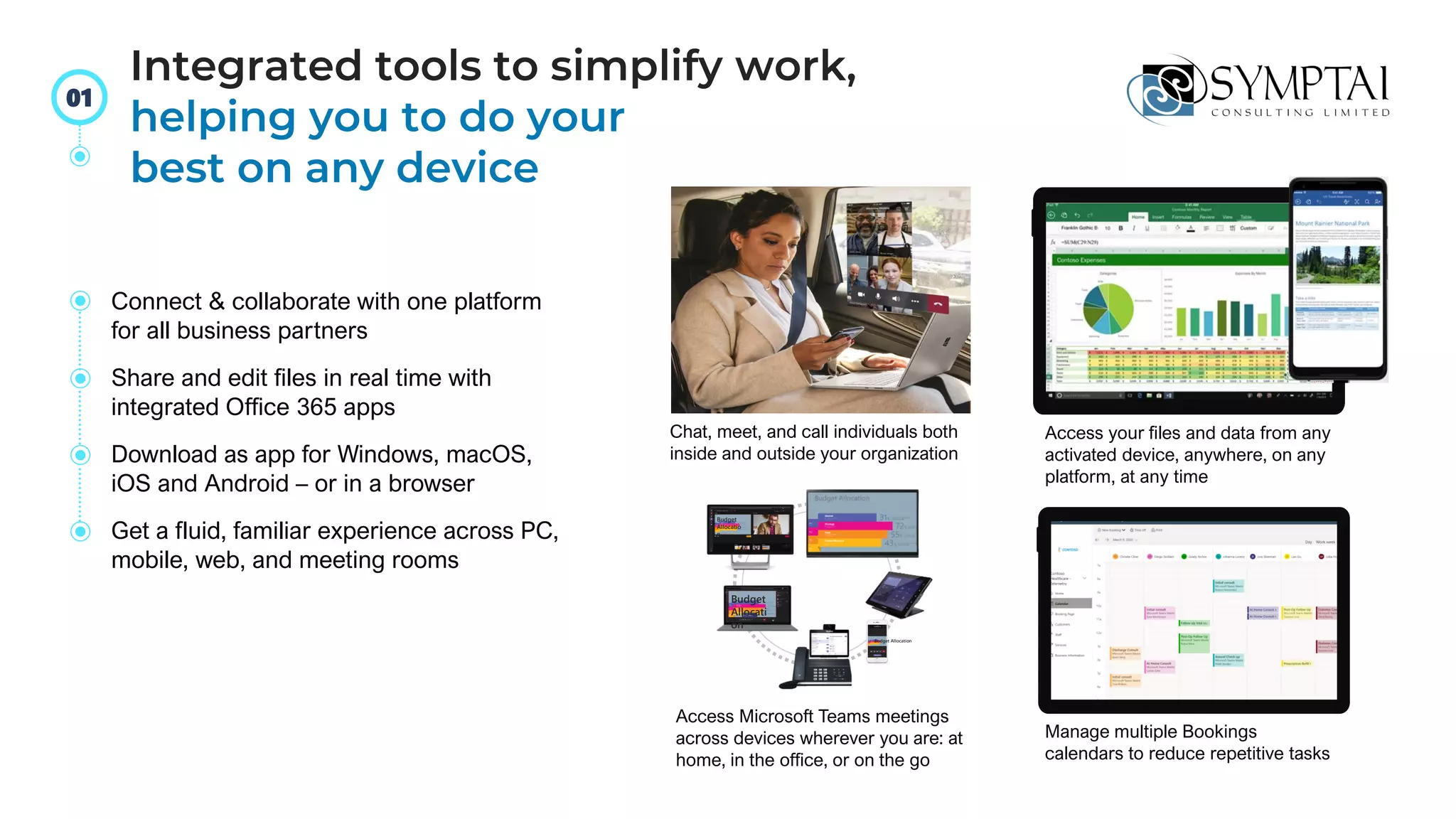
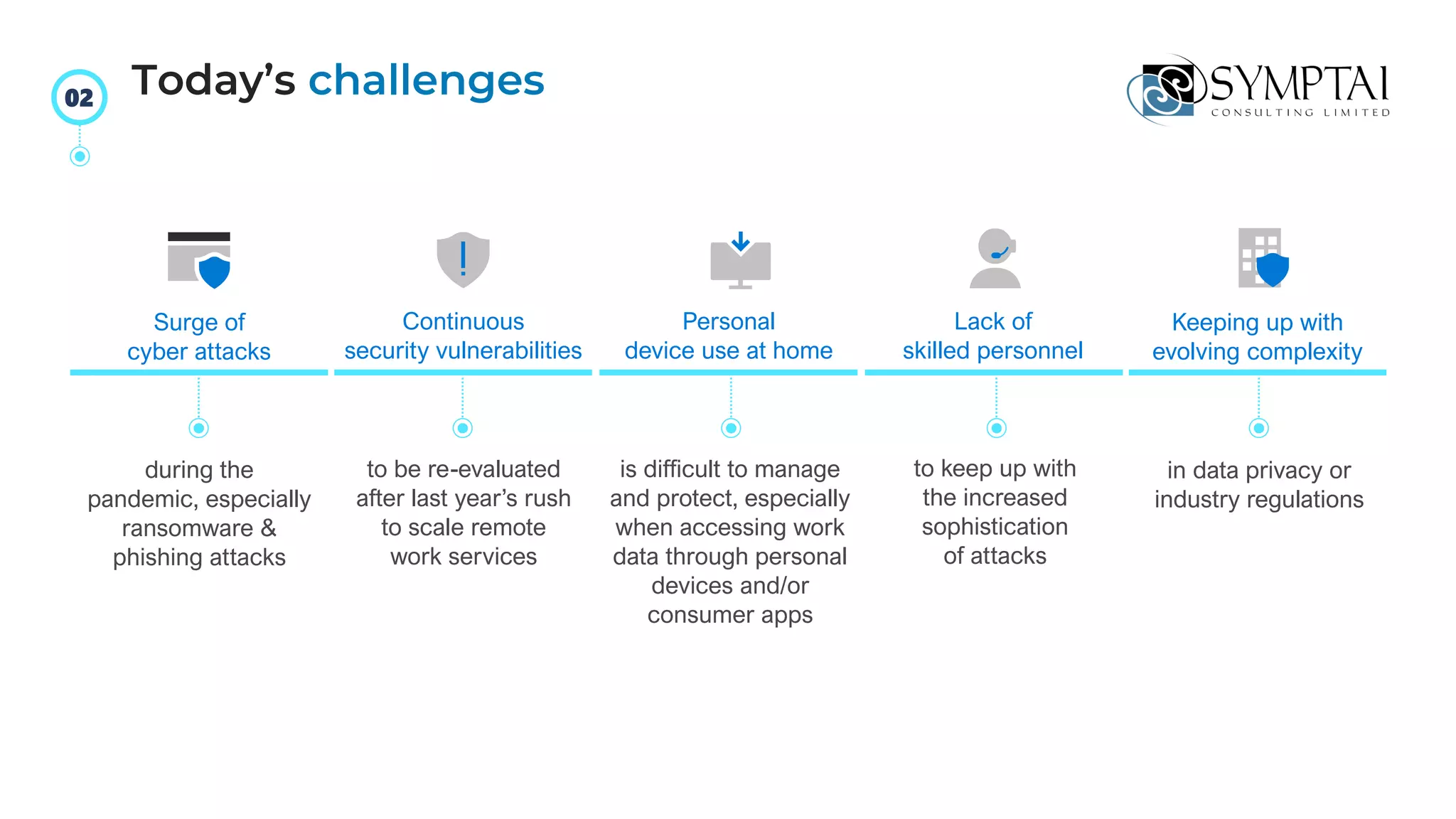
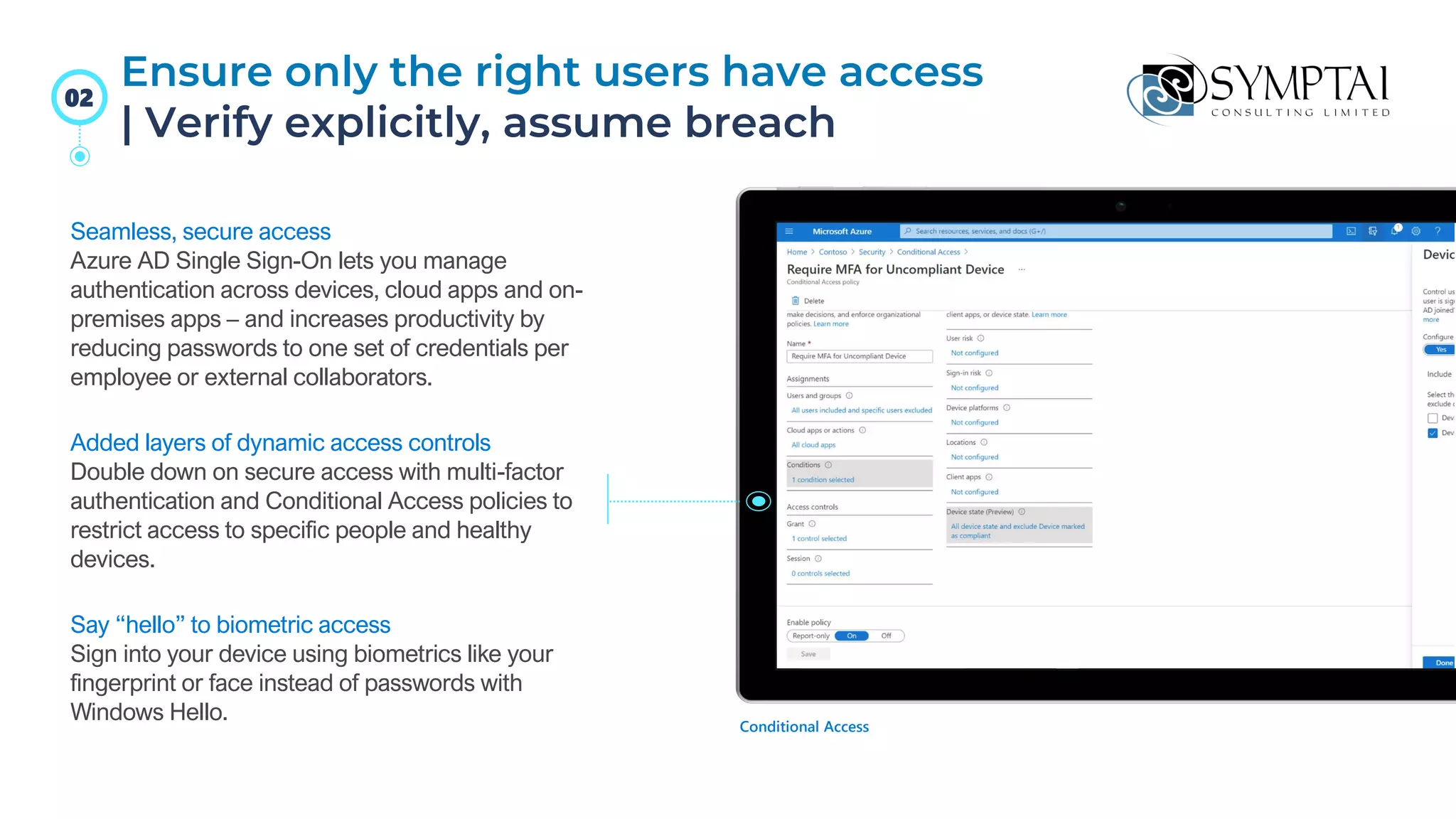
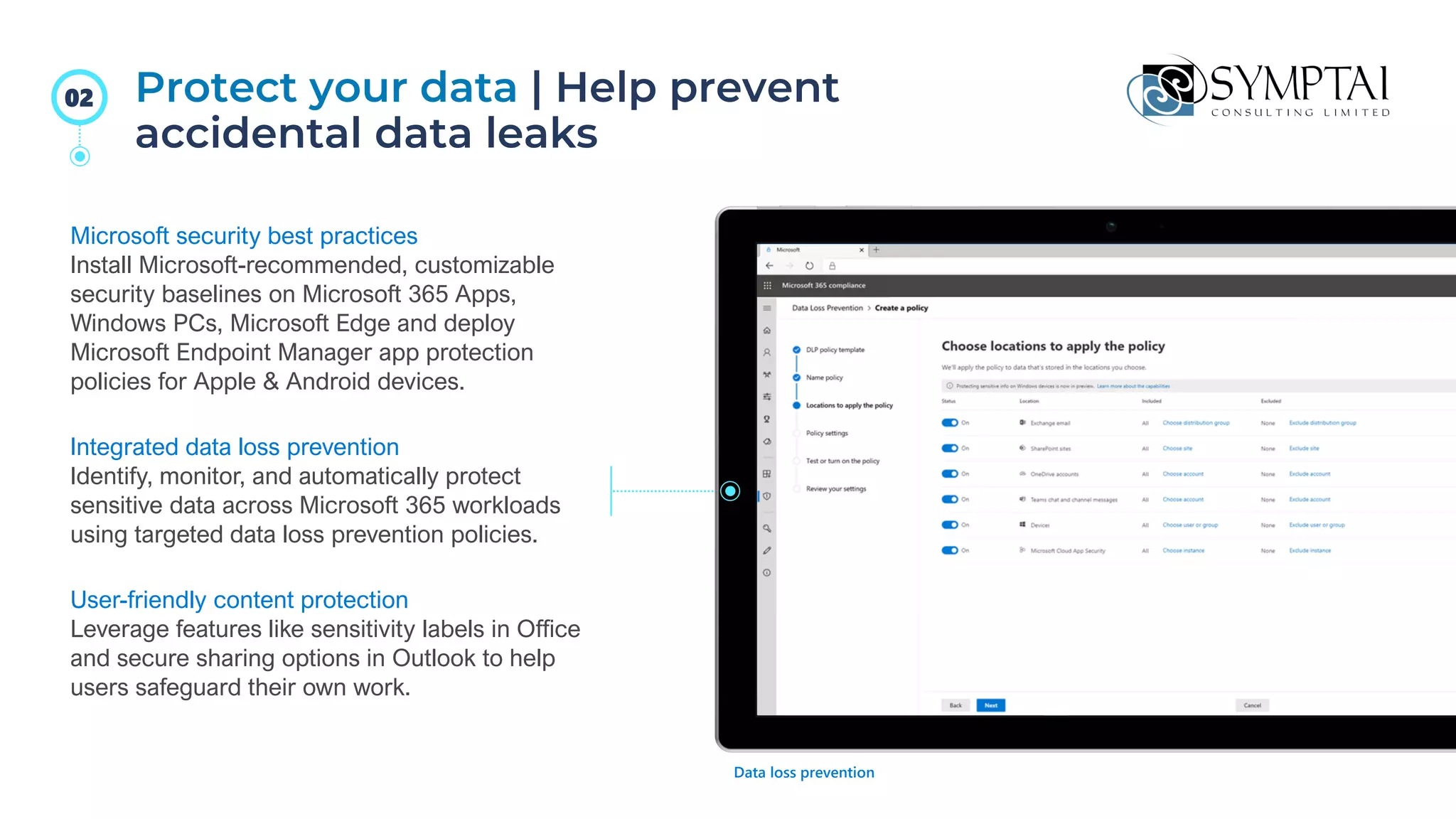
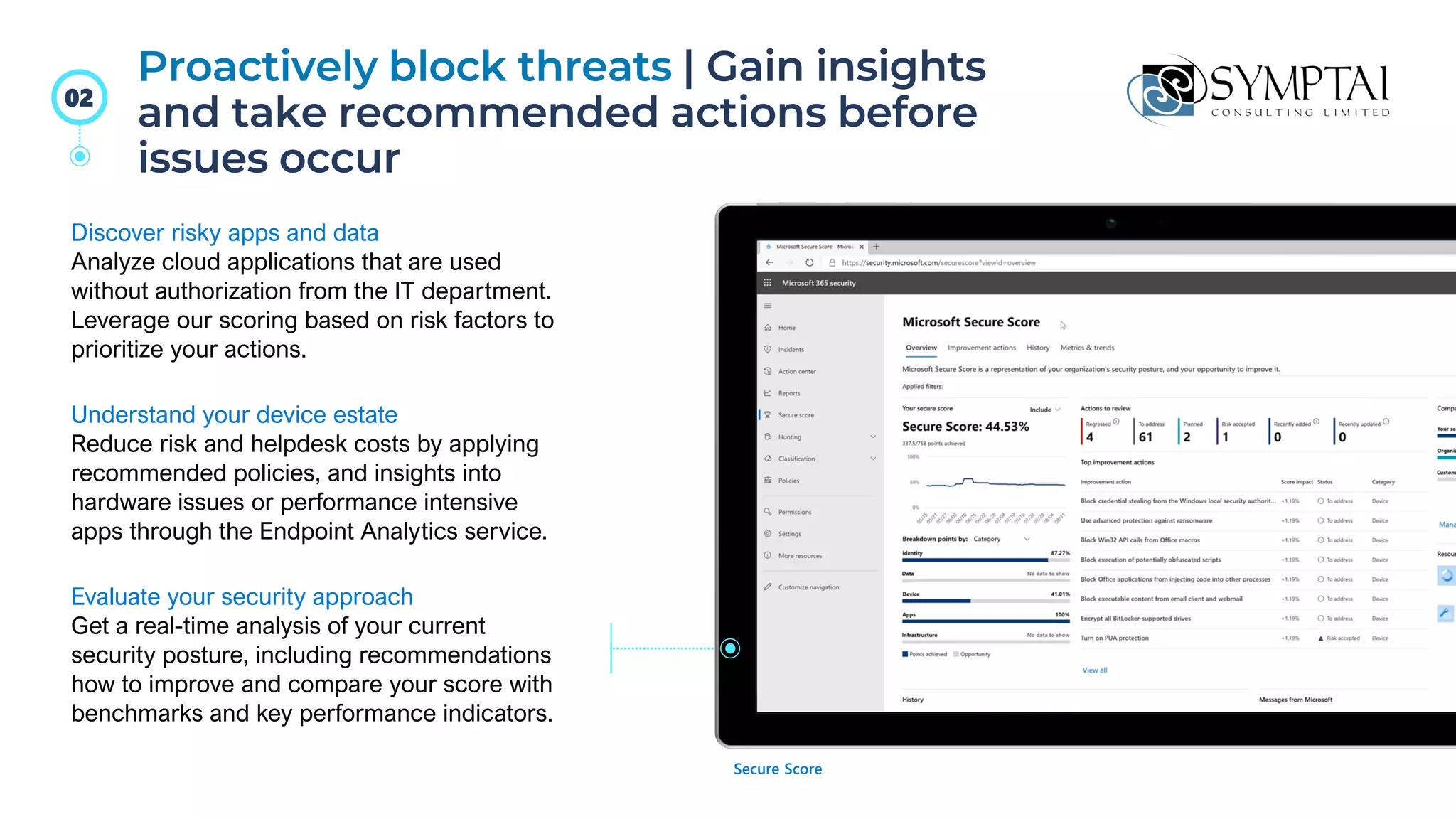
The document discusses cloud migration strategies, emphasizing the need for a clear cloud vision and a systematic approach to assess workloads' suitability for the cloud. It outlines various migration paths, potential challenges, and best practices for managing data privacy and security, while highlighting Microsoft's tools to facilitate collaboration and secure access. Additionally, it offers a promotional discount for cybersecurity services provided by Symptai.