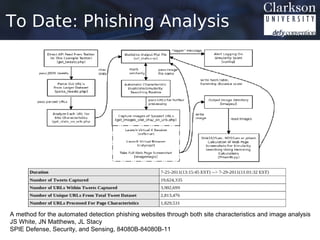
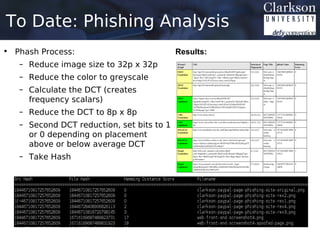
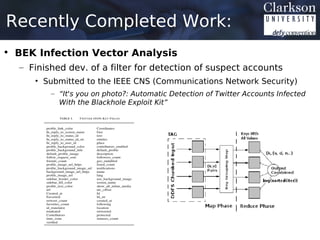
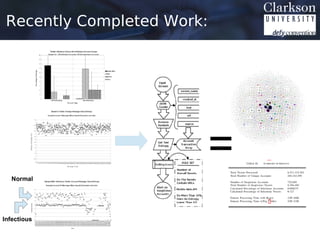
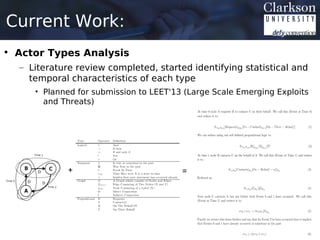
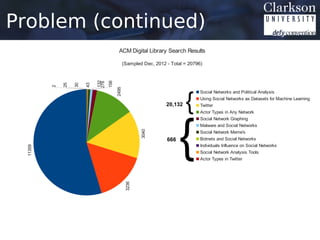
This document provides an outline for a thesis proposal on analyzing the spread of information in social networks. The proposal discusses previous work analyzing social media data and developing analysis tools. It also outlines current and planned research projects applying these tools to study specific events and actor types. The overall goal is to better understand how information spreads in social networks and identify influential users.



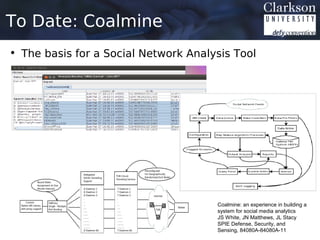
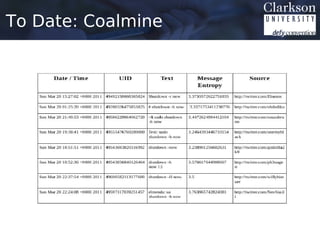

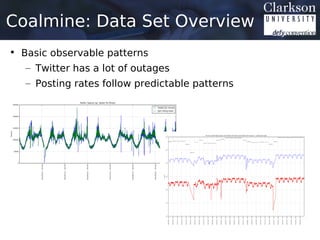
![Coalmine: Data Set Overview
• Over the course of 2012 we collected 165 TB of
Twitter Data (Uncompressed)
– 147 “Full Days”, 100 “Partial Days”
• Estimated 65 Billion Tweets
1
– Twitter traffic at est. 175 million tweets per day in 2012
– Collection rates between 50% and 80% for “Full Days”.
– Data in JSON format using Twitters REST API.
1. Shea Bennett. "Just How Big Is twitter In 2012
[INFOGRAPHIC]," All Twitter - The Unofficial Twitter
Resource, February 2013](https://image.slidesharecdn.com/cpjswfinal-130311231905-phpapp01/85/Clarkson-Joshua-White-Research-Proposal-Presentation-8-320.jpg)