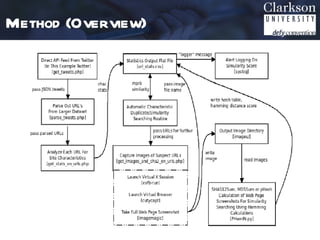
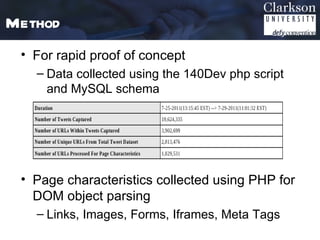
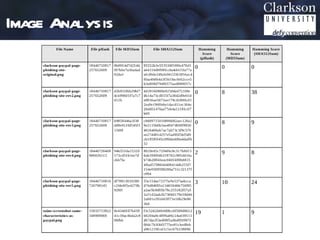
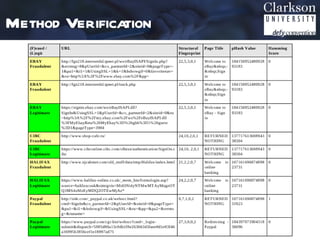
This document outlines a method for automated detection of phishing websites through analysis of both site characteristics and images. The method collects page characteristics like links, images, forms and meta tags using PHP. Images are collected using a headless browser, hashed using pHash which reduces the image to 8x8 pixels, and compared using Hamming distance. The method was verified and then used to analyze the top 5 most spoofed sites, finding some false characteristic matches. Future work includes integrating this detection technique into a social media analytics toolkit.