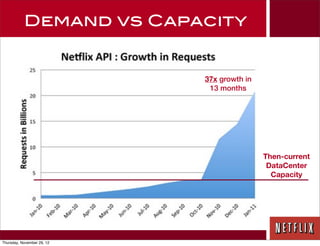
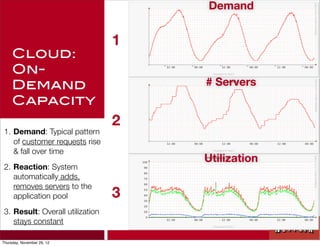
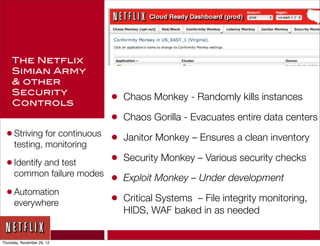
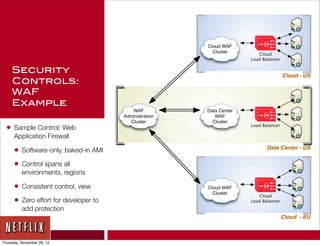
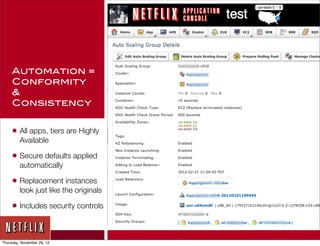
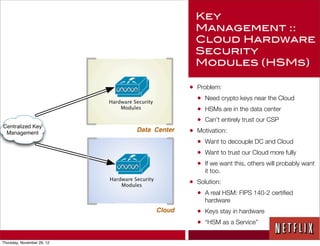
The document discusses Netflix's transition to cloud infrastructure, highlighting their culture of high performance and agility while addressing information security challenges. Key topics include the importance of automation in managing security controls, ensuring integrity, and maintaining availability in a hybrid datacenter/IaaS cloud environment. Netflix's approach leverages a range of tools, including the 'Simian Army' for chaos testing and security monitoring to adapt to rapid changes in business demand.