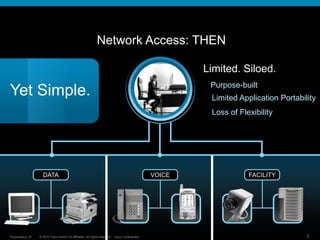
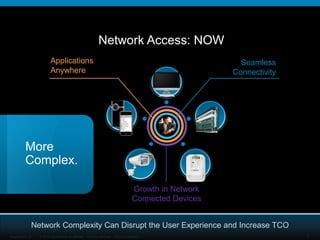
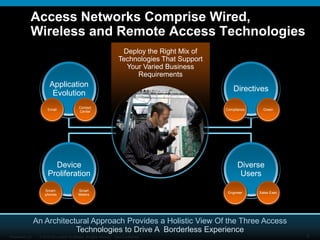
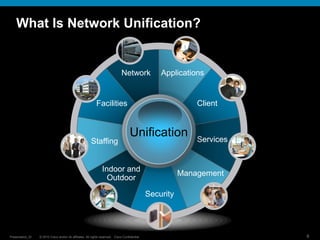
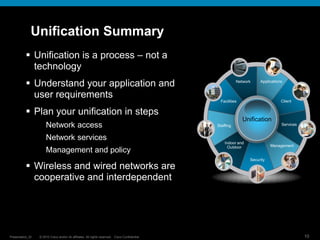
The document discusses network unification and the key to business agility. It describes how network access has become more complex over time as applications and devices have proliferated. A unified network allows users to seamlessly access applications from any device while maintaining security. The presentation outlines the benefits of a unified network such as simplified user management, interoperability between wired and wireless networks, and future-proofing the network to support growth. It provides a checklist for defining a network unification strategy that meets business needs in a cost-effective manner.