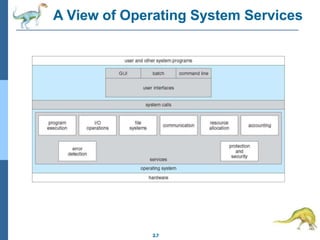
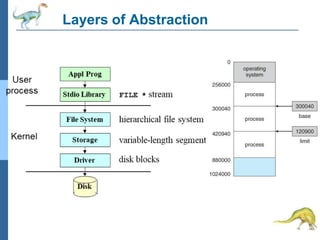
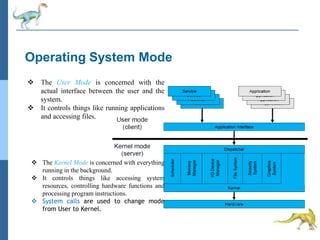
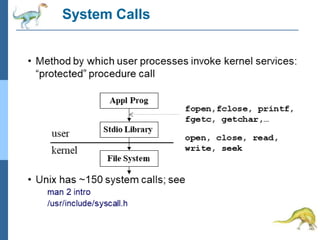
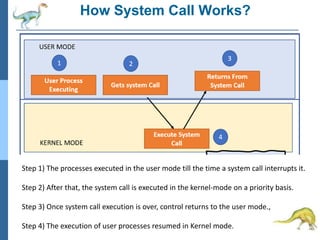
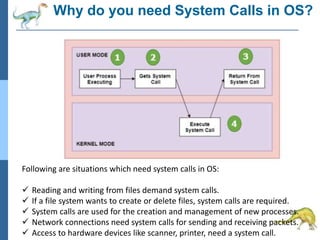
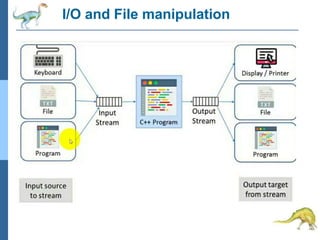
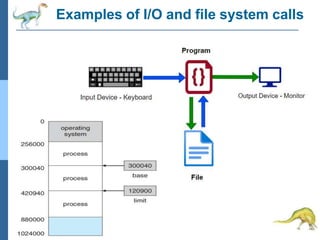
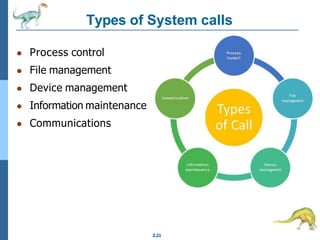
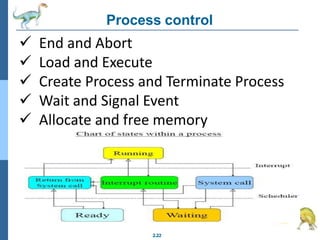
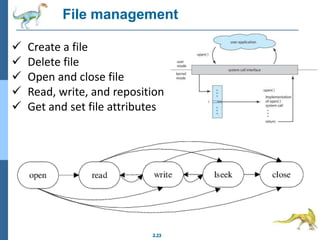
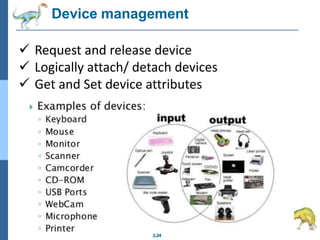
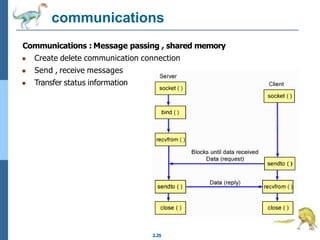
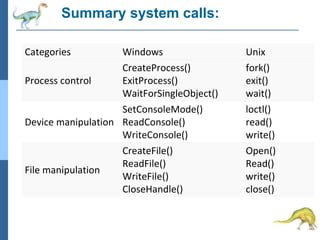
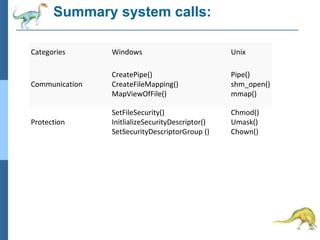
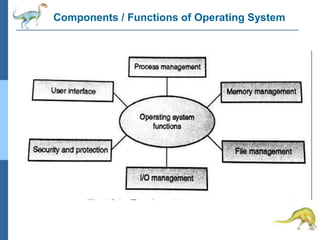
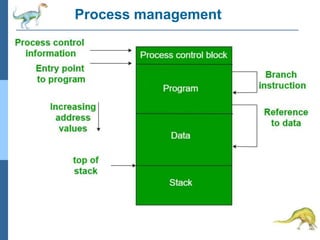
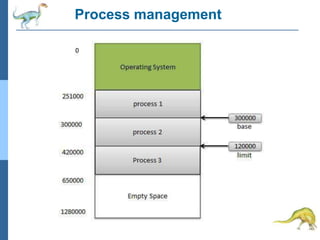
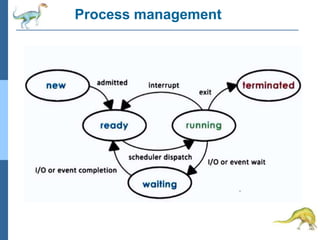
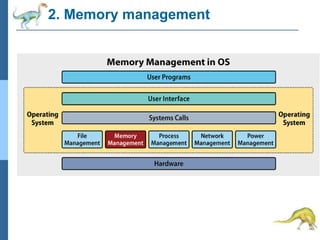
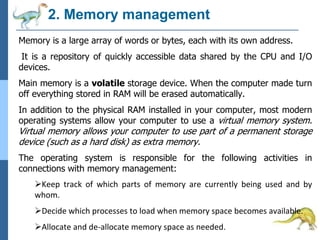
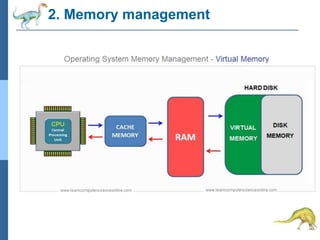
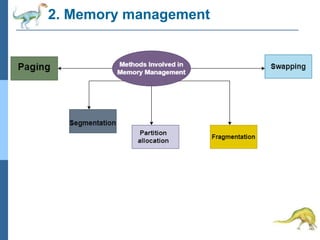
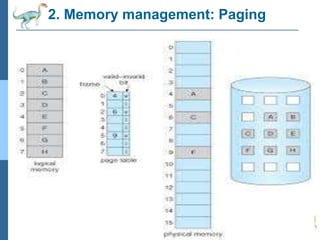
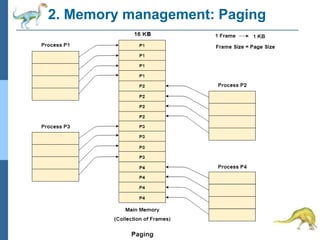
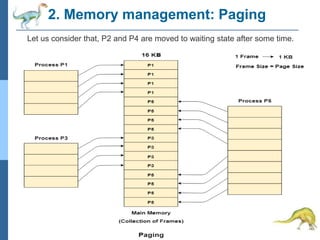
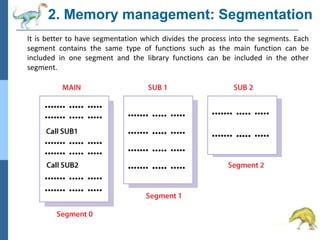
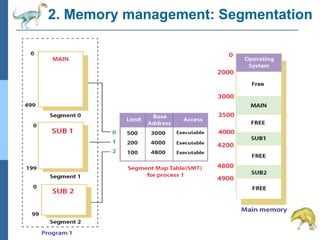
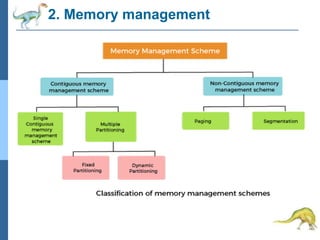
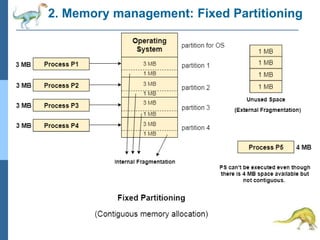
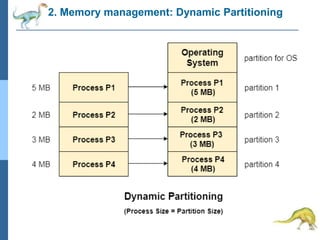
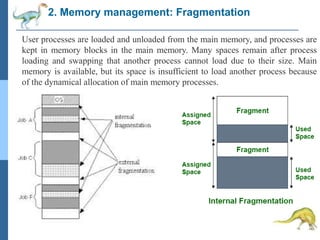
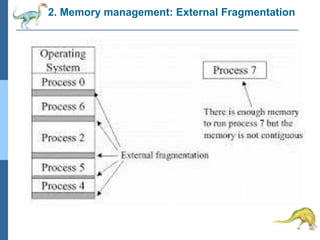
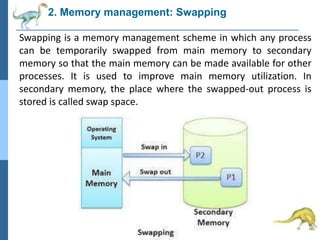
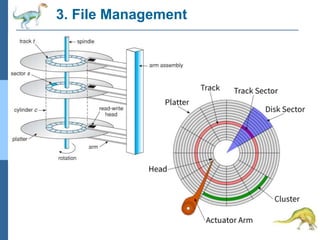
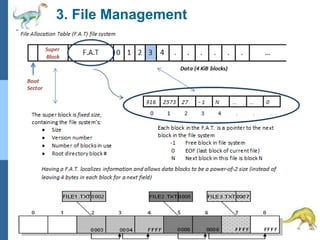
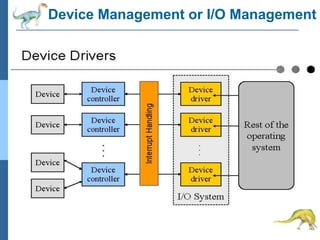
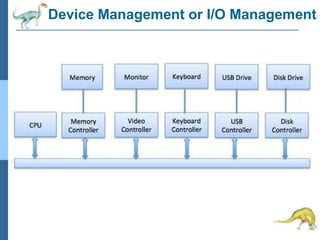
Chapter 2 discusses operating system structures and services, detailing user interfaces, system calls, and the roles of the operating system in resource management, communication, and process execution. It explains user modes versus kernel modes, the importance of system calls for resource access, and the functionalities required for process, memory, and device management. Different types of system calls and file management are also outlined, emphasizing their crucial functions in operating system design.