Chapter 2 2 1 2
•
1 like•739 views
The document discusses the subset construction method for simulating nondeterministic finite automata (NFAs). It explains that the subset construction avoids constructing the entire deterministic finite automaton (DFA) and instead constructs states on-the-fly based on the next input character. As an example, it shows applying the subset construction to an NFA with the input string "a". The document also covers minimizing the number of states in a DFA by starting with sets of accepting and non-accepting states and iteratively splitting sets based on whether states can be distinguished by their transitions. It provides examples of applying this process to specific regular expressions.
Report
Share
Report
Share
Recommended
AI Lesson 14

This document discusses concepts from first-order logic including:
- The Herbrand Universe, which is the set of terms that can be formed from the constants and function symbols in a set of formulae.
- Reduction of formulae to clausal form through a series of truth-preserving transformations, allowing focus on such forms.
- Inference rules like Modus Ponens, properties like soundness, and the role of deductions in a logical system.
- Related concepts like soundness, completeness, consistency, and satisfiability of logics and theories.
Free Ebooks Download ! Edhole

This document provides information about various topics related to automata theory and formal languages, including:
1. It defines the Arden's Theorem and provides the proof that the unique solution to the equation R = Q + RP is R = QP*.
2. It defines the Pumping Lemma for regular expressions and languages, stating that for any regular language L, strings of sufficient length can be decomposed and pumped.
3. It discusses how the Pumping Lemma can be used to prove languages are non-regular by finding strings that cannot be pumped.
4. It provides the proof of the Pumping Lemma based on the states of a finite state automaton accepting the language.
C4 discontinuities

This document discusses three types of discontinuities in graphs: infinite discontinuities which occur at vertical asymptotes, jump discontinuities where the graph "jumps" between values, and removable discontinuities which appear as "holes" in the graph. Infinite discontinuities are found where functions yield division by zero errors. Jump discontinuities occur where the absolute value of a function changes signs. Removable discontinuities are located where both the numerator and denominator equal zero. Examples are provided to demonstrate identifying each discontinuity type algebraically.
Paper 1

This document summarizes a research paper on obtaining local estimates for minimizers of convex integral functionals involving the gradient.
The paper considers functionals whose lagrangians depend only on the gradient and satisfy a generalized symmetry assumption. It adapts a method to obtain local estimates for minimizers near points that are not local extrema. These estimates show that minimizers are bounded from below (above) by a linear function associated with the Minkowski functional. The estimates are then used to deduce versions of the strong maximum principle in the variational setting.
Chapter 13.1.2

The document discusses different types of operators in C programming language including arithmetic, unary, relational, logical, assignment, and conditional operators. It explains how each operator works and provides examples. The key points are:
1) Arithmetic operators include +, -, *, /, and % for addition, subtraction, multiplication, division, and modulus respectively.
2) Unary operators act on a single operand and include -, ++, --, sizeof, and type casts.
3) Relational operators test relationships and include >, <, !=, >=, and <=.
4) Logical operators && and || combine relational expressions and ! negates them.
5) Assignment operators assign values to variables
Data structure

Breadth First Search (BFS) and Depth First Search (DFS) are two graph traversal algorithms. BFS uses a queue to visit all neighbor nodes at the present depth prior to moving to the next depth level, while DFS uses a stack to explore as far as possible along each branch before backtracking. The document provides pseudocode for BFS and DFS algorithms and explains their process through examples of traversing graphs from a starting node.
Admissions in India 2015

This document discusses inverse Laplace transformations and their applications. It covers three cases of inverse Laplace transformations: 1) simple poles that are real and unequal, 2) simple complex conjugate poles, and 3) repeated roots. The document also discusses using the partial fractions expansion method and method of residues to determine inverse Laplace transforms. It provides examples of using the "finger method" to find inverse transforms of functions with simple poles. Additionally, it discusses the initial value theorem and final value theorem, and provides an example of using Laplace transforms to solve a differential equation with zero initial conditions.
1.7. eqivalence of nfa and dfa

The document discusses the conversion of non-deterministic finite automata (NFA) to deterministic finite automata (DFA). It states that an NFA with epsilon transitions can first be converted to an NFA without epsilon transitions, which can then be converted to an equivalent DFA. The conversion of NFA to DFA involves constructing a DFA with up to 2^n states for an n-state NFA, with the same input alphabet and transition and acceptance functions based on the NFA. Examples are provided of converting epsilon NFAs to NFAs without epsilon transitions and NFAs to equivalent DFAs.
Recommended
AI Lesson 14

This document discusses concepts from first-order logic including:
- The Herbrand Universe, which is the set of terms that can be formed from the constants and function symbols in a set of formulae.
- Reduction of formulae to clausal form through a series of truth-preserving transformations, allowing focus on such forms.
- Inference rules like Modus Ponens, properties like soundness, and the role of deductions in a logical system.
- Related concepts like soundness, completeness, consistency, and satisfiability of logics and theories.
Free Ebooks Download ! Edhole

This document provides information about various topics related to automata theory and formal languages, including:
1. It defines the Arden's Theorem and provides the proof that the unique solution to the equation R = Q + RP is R = QP*.
2. It defines the Pumping Lemma for regular expressions and languages, stating that for any regular language L, strings of sufficient length can be decomposed and pumped.
3. It discusses how the Pumping Lemma can be used to prove languages are non-regular by finding strings that cannot be pumped.
4. It provides the proof of the Pumping Lemma based on the states of a finite state automaton accepting the language.
C4 discontinuities

This document discusses three types of discontinuities in graphs: infinite discontinuities which occur at vertical asymptotes, jump discontinuities where the graph "jumps" between values, and removable discontinuities which appear as "holes" in the graph. Infinite discontinuities are found where functions yield division by zero errors. Jump discontinuities occur where the absolute value of a function changes signs. Removable discontinuities are located where both the numerator and denominator equal zero. Examples are provided to demonstrate identifying each discontinuity type algebraically.
Paper 1

This document summarizes a research paper on obtaining local estimates for minimizers of convex integral functionals involving the gradient.
The paper considers functionals whose lagrangians depend only on the gradient and satisfy a generalized symmetry assumption. It adapts a method to obtain local estimates for minimizers near points that are not local extrema. These estimates show that minimizers are bounded from below (above) by a linear function associated with the Minkowski functional. The estimates are then used to deduce versions of the strong maximum principle in the variational setting.
Chapter 13.1.2

The document discusses different types of operators in C programming language including arithmetic, unary, relational, logical, assignment, and conditional operators. It explains how each operator works and provides examples. The key points are:
1) Arithmetic operators include +, -, *, /, and % for addition, subtraction, multiplication, division, and modulus respectively.
2) Unary operators act on a single operand and include -, ++, --, sizeof, and type casts.
3) Relational operators test relationships and include >, <, !=, >=, and <=.
4) Logical operators && and || combine relational expressions and ! negates them.
5) Assignment operators assign values to variables
Data structure

Breadth First Search (BFS) and Depth First Search (DFS) are two graph traversal algorithms. BFS uses a queue to visit all neighbor nodes at the present depth prior to moving to the next depth level, while DFS uses a stack to explore as far as possible along each branch before backtracking. The document provides pseudocode for BFS and DFS algorithms and explains their process through examples of traversing graphs from a starting node.
Admissions in India 2015

This document discusses inverse Laplace transformations and their applications. It covers three cases of inverse Laplace transformations: 1) simple poles that are real and unequal, 2) simple complex conjugate poles, and 3) repeated roots. The document also discusses using the partial fractions expansion method and method of residues to determine inverse Laplace transforms. It provides examples of using the "finger method" to find inverse transforms of functions with simple poles. Additionally, it discusses the initial value theorem and final value theorem, and provides an example of using Laplace transforms to solve a differential equation with zero initial conditions.
1.7. eqivalence of nfa and dfa

The document discusses the conversion of non-deterministic finite automata (NFA) to deterministic finite automata (DFA). It states that an NFA with epsilon transitions can first be converted to an NFA without epsilon transitions, which can then be converted to an equivalent DFA. The conversion of NFA to DFA involves constructing a DFA with up to 2^n states for an n-state NFA, with the same input alphabet and transition and acceptance functions based on the NFA. Examples are provided of converting epsilon NFAs to NFAs without epsilon transitions and NFAs to equivalent DFAs.
HOMOGENEOUS LINEAR PDE

This document discusses techniques for solving homogeneous linear partial differential equations of second and higher order with constant coefficients. It covers finding the roots of the auxiliary equation, determining the complementary function based on the roots, and using exponential shifting and general types for equations not covered by the first four types. Specific methods are outlined for solving equations of different forms.
Functional dependency

The document discusses relational databases and functional dependencies. It begins by defining a relational database as a set of tables containing data organized in columns. Each table represents a relation between attributes. The document then provides examples of relations and attributes. It introduces the concept of functional dependencies, where a dependency a->b means that the value of b is determined by a. It provides examples and rules for determining if a functional dependency holds. The document also discusses closure of functional dependencies and canonical forms.
14 pro resolution

This document provides an overview of resolution in propositional logic. It introduces resolution as a new rule of inference that allows inferring a resolvent clause from two clauses. It describes how to convert arbitrary well-formed formulas into conjunctions of clauses to use with resolution. Resolution refutations are discussed as a way to decide logical entailments by attempting to derive the empty clause. Various strategies for conducting resolution refutation searches more efficiently are also covered, including ordering strategies and refinement strategies. Finally, the document defines Horn clauses and their special properties that allow for linear-time deduction algorithms.
1.9. minimization of dfa

The document describes the process of minimizing a deterministic finite automaton (DFA) using the Myhill-Nerode theorem. It involves 4 steps: 1) creating a table of all state pairs, 2) marking pairs where one state is final and the other is not, 3) transitively marking additional pairs, 4) combining any remaining unmarked pairs into single states. An example is provided where the given 6-state DFA is minimized to a 3-state DFA using this process. Terminology used in DFA minimization is also defined.
05 dataflow

This document provides lecture notes on dataflow analysis techniques. It introduces liveness analysis, neededness analysis, and reaching definitions analysis. Liveness analysis is extended to handle memory references. Neededness analysis is introduced to identify dead code by determining which variables are needed, rather than just live. Reaching definitions analysis is a forward dataflow analysis used for optimizations like constant propagation. Examples are provided and the analysis rules for each technique are specified.
IJCER (www.ijceronline.com) International Journal of computational Engineerin...

The document discusses dynamical behaviors in the Lorenz model, a system of nonlinear differential equations. It begins with introductions to concepts like limit cycles, Hopf bifurcations, and how periodic solutions can emerge from equilibria. The main investigation analyzes the Lorenz model, which exhibits chaotic behavior. Parameters are fixed, and three equilibrium points are identified. The focus is on one equilibrium point that is suitable for investigating the system's dynamic behaviors near a Hopf bifurcation.
Design of a Pseudo-Random Binary Code Generator via a Developed Simulation Model

This paper presents a developed tool for Pseudo-
Random Binary Code generator (PRBCG). Based on extensive
study of LFSR theory we developed the simulation model of
PRBCG. The developed model is faster and simulates the
process for very high length of Linear Feedback Shift Registers
(LFSRs). We tested our model for the value n = 300 where n is
the length of the LFSR. The developed software model is also
capable of providing the transition states of different bits of
LFSRs. Further, the model has capability of switching to any
possible characteristic polynomial (feedback connections) of
n-bit LFSR. Also, the model is designed such that it can
accommodate all the possible initial conditions (2n) of LFSR
Chapter 2.1

This document defines and provides examples of key concepts in probability and statistics, including:
- Random experiments, sample spaces, events, and tree diagrams are introduced and examples are given.
- Counting techniques like multiplication rules, permutations, and combinations are defined and applied to examples involving selecting components, locations, and objects.
- Key terms are defined, such as mutually exclusive, complement, union, and intersection of events. Venn diagrams are also introduced.
- Examples involve calculating the number of possible outcomes for experiments selecting parts, locations, designs, and samples. Formulas for permutations and combinations are applied.
NFA DFA Equivalence theorem 

These slides were submitted by Muskan Bathla, Nivedit Jain and Sanskar Mani (all sophomore undergrad in Computer Science and Engineering) as a part of lecture scribing for Theory of Computation Course at Indian Institute of Technology Jodhpur, under the guidance of Dr. Anand Mishra, IIT Jodhpur
[ITP - Lecture 04] Variables and Constants in C/C++![[ITP - Lecture 04] Variables and Constants in C/C++](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[ITP - Lecture 04] Variables and Constants in C/C++](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Variables and Constants in C/C++, Types of Constant, Types of Variables, Rules for Variable Creation, Rules for Constants
Lec39

This lecture discusses flow through channel transitions such as obstructions and bridge piers. It reviews the continuity and energy equations for analyzing flow through obstructions. A parameter σ representing the ratio of widths upstream and downstream of the obstruction is introduced. Equations are developed relating σ, the Froude numbers upstream and downstream, and the fraction of upstream energy available downstream. A limiting downstream Froude number that allows critical flow at the obstruction is defined. Flow conditions upstream and downstream of bridge piers are also briefly discussed.
Introduction to c programming

The document discusses the C programming language. It provides the definition of a program and source code for a simple "Hello World" program in C. It describes how C was developed by Dennis Ritchie in 1972 and some key features of C like it being a structured, portable, middle-level language. The document also provides information on program structure in C, writing, compiling and running a C program, identifiers, constants, data types and more.
Ch8a

The document discusses intermediate code generation in compiler construction. It covers several intermediate representations including postfix notation, three-address code, and quadruples. It also discusses generating three-address code through syntax-directed translation and the use of symbol tables to handle name resolution and scoping.
Ch8b

The document discusses several advanced intermediate code generation techniques used in compilers, including:
1) Reusing temporary variable names to avoid using new temps whenever possible.
2) Addressing elements in one-dimensional and multi-dimensional arrays using base addresses and calculating offsets.
3) Translating logical, relational, and Boolean expressions using three-address code with temporary variables to store intermediate values.
Chapter Eight(2)

The document discusses code generation techniques in compiler construction. It covers generating code for control structures like if-statements and while-loops, as well as addressing techniques for data structures like arrays. Intermediate representations like three-address code and P-code are used. Label generation and back-patching allow jumps to not-yet defined code locations.
Chapter Eight(1)

The document discusses code generation techniques in compiler construction. It describes generating executable code from source code by using intermediate representations like three-address code and P-code. It covers generating code from syntax trees, implementing intermediate codes using data structures, and translating between different intermediate representations and target machine code.
Intermediate code generation1

The document describes intermediate code generation during compilation.
1) An intermediate language is used to translate source programs into a form that is CPU independent yet close to machine language. This facilitates code optimization and retargeting of compilers.
2) Common intermediate languages include syntax trees, postfix notation, and three-address code using quadruples. Three-address code breaks down expressions into single assignment statements to simplify optimization.
3) Semantic rules for syntax-directed translation are described to generate three-address code for expressions, assignments, procedures, and other language constructs. Attributes track temporary variables and generated code.
Interm codegen

The document discusses intermediate code generation in compilers. It describes how compilers generate intermediate code representations after parsing source code. Intermediate representations allow separating the front-end and back-end of compilers, facilitating code optimization and retargeting compilers to different architectures. Common intermediate representations discussed include abstract syntax trees, postfix notation, static single assignment form, and three-address instructions. The document also provides examples of generating three-address code using syntax-directed translation.
Three address code In Compiler Design

Three Address code Is an intermediate code used by optimizing compilers to aid in the implementation of code-improving transformations
Code generation

The document discusses code generation in compilers. It describes the main tasks of the code generator as instruction selection, register allocation and assignment, and instruction ordering. It then discusses various issues in designing a code generator such as the input and output formats, memory management, different instruction selection and register allocation approaches, and choice of evaluation order. The target machine used is a hypothetical machine with general purpose registers, different addressing modes, and fixed instruction costs. Examples of instruction selection and utilization of addressing modes are provided.
Hwsoln03 toc

This document contains the solutions to homework 3 for the course CS 341: Foundations of Computer Science II. It includes solutions to problems involving constructing NFAs and DFAs for various languages, proving properties of NFAs and regular expressions, and constructing regular expressions and DFAs.
CS 162 Fall 2015 Homework 1 Problems September 29, 2015 Timothy Johnson 1. Ex...

CS 162 Fall 2015
Homework 1 Problems
September 29, 2015 Timothy Johnson
1. Exercise 2.2.4 on page 53 of Hopcroft et al. Give DFA’s accepting the following languages over the alphabet {0,1}. (a) The set of all strings ending in 0
More Related Content
What's hot
HOMOGENEOUS LINEAR PDE

This document discusses techniques for solving homogeneous linear partial differential equations of second and higher order with constant coefficients. It covers finding the roots of the auxiliary equation, determining the complementary function based on the roots, and using exponential shifting and general types for equations not covered by the first four types. Specific methods are outlined for solving equations of different forms.
Functional dependency

The document discusses relational databases and functional dependencies. It begins by defining a relational database as a set of tables containing data organized in columns. Each table represents a relation between attributes. The document then provides examples of relations and attributes. It introduces the concept of functional dependencies, where a dependency a->b means that the value of b is determined by a. It provides examples and rules for determining if a functional dependency holds. The document also discusses closure of functional dependencies and canonical forms.
14 pro resolution

This document provides an overview of resolution in propositional logic. It introduces resolution as a new rule of inference that allows inferring a resolvent clause from two clauses. It describes how to convert arbitrary well-formed formulas into conjunctions of clauses to use with resolution. Resolution refutations are discussed as a way to decide logical entailments by attempting to derive the empty clause. Various strategies for conducting resolution refutation searches more efficiently are also covered, including ordering strategies and refinement strategies. Finally, the document defines Horn clauses and their special properties that allow for linear-time deduction algorithms.
1.9. minimization of dfa

The document describes the process of minimizing a deterministic finite automaton (DFA) using the Myhill-Nerode theorem. It involves 4 steps: 1) creating a table of all state pairs, 2) marking pairs where one state is final and the other is not, 3) transitively marking additional pairs, 4) combining any remaining unmarked pairs into single states. An example is provided where the given 6-state DFA is minimized to a 3-state DFA using this process. Terminology used in DFA minimization is also defined.
05 dataflow

This document provides lecture notes on dataflow analysis techniques. It introduces liveness analysis, neededness analysis, and reaching definitions analysis. Liveness analysis is extended to handle memory references. Neededness analysis is introduced to identify dead code by determining which variables are needed, rather than just live. Reaching definitions analysis is a forward dataflow analysis used for optimizations like constant propagation. Examples are provided and the analysis rules for each technique are specified.
IJCER (www.ijceronline.com) International Journal of computational Engineerin...

The document discusses dynamical behaviors in the Lorenz model, a system of nonlinear differential equations. It begins with introductions to concepts like limit cycles, Hopf bifurcations, and how periodic solutions can emerge from equilibria. The main investigation analyzes the Lorenz model, which exhibits chaotic behavior. Parameters are fixed, and three equilibrium points are identified. The focus is on one equilibrium point that is suitable for investigating the system's dynamic behaviors near a Hopf bifurcation.
Design of a Pseudo-Random Binary Code Generator via a Developed Simulation Model

This paper presents a developed tool for Pseudo-
Random Binary Code generator (PRBCG). Based on extensive
study of LFSR theory we developed the simulation model of
PRBCG. The developed model is faster and simulates the
process for very high length of Linear Feedback Shift Registers
(LFSRs). We tested our model for the value n = 300 where n is
the length of the LFSR. The developed software model is also
capable of providing the transition states of different bits of
LFSRs. Further, the model has capability of switching to any
possible characteristic polynomial (feedback connections) of
n-bit LFSR. Also, the model is designed such that it can
accommodate all the possible initial conditions (2n) of LFSR
Chapter 2.1

This document defines and provides examples of key concepts in probability and statistics, including:
- Random experiments, sample spaces, events, and tree diagrams are introduced and examples are given.
- Counting techniques like multiplication rules, permutations, and combinations are defined and applied to examples involving selecting components, locations, and objects.
- Key terms are defined, such as mutually exclusive, complement, union, and intersection of events. Venn diagrams are also introduced.
- Examples involve calculating the number of possible outcomes for experiments selecting parts, locations, designs, and samples. Formulas for permutations and combinations are applied.
NFA DFA Equivalence theorem 

These slides were submitted by Muskan Bathla, Nivedit Jain and Sanskar Mani (all sophomore undergrad in Computer Science and Engineering) as a part of lecture scribing for Theory of Computation Course at Indian Institute of Technology Jodhpur, under the guidance of Dr. Anand Mishra, IIT Jodhpur
[ITP - Lecture 04] Variables and Constants in C/C++![[ITP - Lecture 04] Variables and Constants in C/C++](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[ITP - Lecture 04] Variables and Constants in C/C++](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Variables and Constants in C/C++, Types of Constant, Types of Variables, Rules for Variable Creation, Rules for Constants
Lec39

This lecture discusses flow through channel transitions such as obstructions and bridge piers. It reviews the continuity and energy equations for analyzing flow through obstructions. A parameter σ representing the ratio of widths upstream and downstream of the obstruction is introduced. Equations are developed relating σ, the Froude numbers upstream and downstream, and the fraction of upstream energy available downstream. A limiting downstream Froude number that allows critical flow at the obstruction is defined. Flow conditions upstream and downstream of bridge piers are also briefly discussed.
Introduction to c programming

The document discusses the C programming language. It provides the definition of a program and source code for a simple "Hello World" program in C. It describes how C was developed by Dennis Ritchie in 1972 and some key features of C like it being a structured, portable, middle-level language. The document also provides information on program structure in C, writing, compiling and running a C program, identifiers, constants, data types and more.
What's hot (12)
IJCER (www.ijceronline.com) International Journal of computational Engineerin...

IJCER (www.ijceronline.com) International Journal of computational Engineerin...
Design of a Pseudo-Random Binary Code Generator via a Developed Simulation Model

Design of a Pseudo-Random Binary Code Generator via a Developed Simulation Model
[ITP - Lecture 04] Variables and Constants in C/C++![[ITP - Lecture 04] Variables and Constants in C/C++](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[ITP - Lecture 04] Variables and Constants in C/C++](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[ITP - Lecture 04] Variables and Constants in C/C++
Viewers also liked
Ch8a

The document discusses intermediate code generation in compiler construction. It covers several intermediate representations including postfix notation, three-address code, and quadruples. It also discusses generating three-address code through syntax-directed translation and the use of symbol tables to handle name resolution and scoping.
Ch8b

The document discusses several advanced intermediate code generation techniques used in compilers, including:
1) Reusing temporary variable names to avoid using new temps whenever possible.
2) Addressing elements in one-dimensional and multi-dimensional arrays using base addresses and calculating offsets.
3) Translating logical, relational, and Boolean expressions using three-address code with temporary variables to store intermediate values.
Chapter Eight(2)

The document discusses code generation techniques in compiler construction. It covers generating code for control structures like if-statements and while-loops, as well as addressing techniques for data structures like arrays. Intermediate representations like three-address code and P-code are used. Label generation and back-patching allow jumps to not-yet defined code locations.
Chapter Eight(1)

The document discusses code generation techniques in compiler construction. It describes generating executable code from source code by using intermediate representations like three-address code and P-code. It covers generating code from syntax trees, implementing intermediate codes using data structures, and translating between different intermediate representations and target machine code.
Intermediate code generation1

The document describes intermediate code generation during compilation.
1) An intermediate language is used to translate source programs into a form that is CPU independent yet close to machine language. This facilitates code optimization and retargeting of compilers.
2) Common intermediate languages include syntax trees, postfix notation, and three-address code using quadruples. Three-address code breaks down expressions into single assignment statements to simplify optimization.
3) Semantic rules for syntax-directed translation are described to generate three-address code for expressions, assignments, procedures, and other language constructs. Attributes track temporary variables and generated code.
Interm codegen

The document discusses intermediate code generation in compilers. It describes how compilers generate intermediate code representations after parsing source code. Intermediate representations allow separating the front-end and back-end of compilers, facilitating code optimization and retargeting compilers to different architectures. Common intermediate representations discussed include abstract syntax trees, postfix notation, static single assignment form, and three-address instructions. The document also provides examples of generating three-address code using syntax-directed translation.
Three address code In Compiler Design

Three Address code Is an intermediate code used by optimizing compilers to aid in the implementation of code-improving transformations
Code generation

The document discusses code generation in compilers. It describes the main tasks of the code generator as instruction selection, register allocation and assignment, and instruction ordering. It then discusses various issues in designing a code generator such as the input and output formats, memory management, different instruction selection and register allocation approaches, and choice of evaluation order. The target machine used is a hypothetical machine with general purpose registers, different addressing modes, and fixed instruction costs. Examples of instruction selection and utilization of addressing modes are provided.
Viewers also liked (8)
Similar to Chapter 2 2 1 2
Hwsoln03 toc

This document contains the solutions to homework 3 for the course CS 341: Foundations of Computer Science II. It includes solutions to problems involving constructing NFAs and DFAs for various languages, proving properties of NFAs and regular expressions, and constructing regular expressions and DFAs.
CS 162 Fall 2015 Homework 1 Problems September 29, 2015 Timothy Johnson 1. Ex...

CS 162 Fall 2015
Homework 1 Problems
September 29, 2015 Timothy Johnson
1. Exercise 2.2.4 on page 53 of Hopcroft et al. Give DFA’s accepting the following languages over the alphabet {0,1}. (a) The set of all strings ending in 0
Chapter 2 2 1 1

This document summarizes the process of converting a regular expression to a deterministic finite automaton (DFA) via a nondeterministic finite automaton (NFA). It first explains Thompson's construction for building an NFA from a regular expression using epsilon transitions. It then describes the subset construction algorithm for eliminating epsilon transitions and nondeterminism to produce an equivalent DFA. The algorithm works by considering sets of NFA states as DFA states and computing the epsilon closures and resulting state sets after each input symbol.
Nfa vs dfa

The document discusses techniques for converting non-deterministic finite automata (NFAs) to deterministic finite automata (DFAs) in three steps:
1) Using subset construction to determinize an NFA by considering sets of reachable states from each transition as single states in the DFA.
2) Minimizing the number of states in the resulting DFA using an algorithm that merges equivalent states that have identical transitions for all inputs.
3) Computing equivalent state sets using partition refinement, which iteratively partitions states based on their transitions for each input symbol.
Lecture 17- F19.pdf

This document describes the process of converting a non-deterministic finite automaton (NFA) to a deterministic finite automaton (DFA) using subset construction. It provides examples to demonstrate how to determine the states and transitions of the equivalent DFA by tracking all possible states the NFA could be in after reading each input symbol. The key steps involve using e-closure and move operations on state sets to iteratively build up the DFA states and transition table until all states are determined.
Compiler Design File

The document discusses compiler theory and provides code examples. It covers:
1. Lex theory - how regular expressions are used to specify patterns for tokenization and how these are implemented as finite state automata.
2. Yacc theory - how context-free grammars are specified in BNF and parsed using shift-reduce parsing. Issues like shift-reduce conflicts and reduce-reduce conflicts are explained.
3. Code examples of stack implementations using arrays and linked lists, and a program to check if a string is a keyword.
4-Regular expression to Deterministic Finite Automata (Direct method)-05-05-2...

4-Regular expression to Deterministic Finite Automata (Direct method)-05-05-2...venkatapranaykumarGa
The document describes the subset construction algorithm for converting a non-deterministic finite automaton (NFA) to a deterministic finite automaton (DFA). The algorithm constructs the transition table for the DFA by iteratively taking the epsilon-closure of states reached on transitions and adding them as new DFA states until no new states are generated. An example conversion of an NFA to a DFA is shown step-by-step to demonstrate the algorithm.optimization of DFA

The document discusses methods for minimizing deterministic finite automata (DFAs). It explains that states can be eliminated if they are unreachable, dead, or non-distinguishable from other states. The partitioning algorithm is described as a method for finding equivalent states that go to the same partitions under all inputs. The algorithm is demonstrated on a sample DFA, merging equivalent states into single states until no further merges are possible, resulting in a minimized DFA. The Myhill-Nerode theorem provides another approach using a state pair marking technique to identify indistinguishable states that can be combined.
A class of boundary value methods for the complex delay differential equation

In this paper, a class of boundary value methods (BVMs) for delay differential equations (DDEs) is considered. The delay dependent stable regions of the extended trapezoidal rules of second kind (ETR2s), which are a class of BVMs, are displayed for the test equation of DDEs. Furthermore, it is showed ETR2s cannot preserve the delay-dependent stability of the complex coefficient test equation considered. Some numerical experiments are given to confirm the theoretical results.
AMS 2000 Mathematics Subject Classification: 65L20, 65M12
Lecture 03 lexical analysis

Thompson's construction algorithm converts regular expressions to nondeterministic finite automata (NFAs) by recursively building the NFA for each subexpression. The subset construction algorithm converts NFAs to deterministic finite automata (DFAs) by constructing states that correspond to sets of NFA states, and transitions correspond to the reachable states on each input symbol. Converting regular expressions to NFAs to DFAs shows that regular expressions, NFAs, and DFAs all have equivalent expressive power for describing regular languages.
Let us c (by yashvant kanetkar) chapter 1 solution

This document contains solutions to various questions related to C programming language concepts. It discusses valid and invalid variable names in C, identifies errors in sample C code statements, evaluates expressions and shows the hierarchy of operations, and provides answers to multiple choice questions about C fundamentals. Sample C code is also provided to demonstrate calculating areas and perimeters of shapes, employee salaries, percentages and conversions between measurement units.
aho corasick paper study note

This document discusses the use of finite state machines for efficient string matching. It describes how a non-deterministic finite automaton (NFA) can be used to match patterns against a payload by transitioning between states based on character inputs. The document notes that NFAs can have redundant matches and proposes converting the NFA to a deterministic finite automaton (DFA) by eliminating failure functions and copying transition information to remove redundancies. This improves performance by avoiding unnecessary state transitions during matching.
Laplace

This document provides an introduction to Laplace transforms for engineers. It begins with definitions of Laplace transforms and motivates their use by explaining how they can help solve differential equations involving discontinuous functions. It then discusses three methods for finding Laplace transforms: directly from the definition, using properties of transforms, and looking transforms up in lists. The document explains how to use partial fractions to find inverse Laplace transforms and solve ordinary differential equations (ODEs) and systems of ODEs using Laplace transform methods. It concludes with an example of using Laplace transforms to handle an impulse problem involving differential equations.
finite_automata.ppt

This document discusses deterministic finite automata (DFAs) and how they are used to recognize regular expressions and generate lexical analysis tables. It provides examples of DFAs for specific regular expressions. It also discusses how to construct a nondeterministic finite automaton (NFA) from a regular expression using basic building blocks. The document then gives an example of constructing an NFA for an identifier regular expression using the described mechanical method.
1406

This document discusses improving two algorithms in the Spot model checking library that create automata with more transitions than necessary. It proposes using a feedback arc set (FAS) to minimize the number of transitions.
It describes an existing heuristic called GR that approximates a minimal FAS in linear time by ordering states. It adapts this heuristic to work on automata rather than graphs by generalizing concepts like in/out degree.
The document evaluates applying the improved FAS computation to the complementation of deterministic Büchi automata and conversion of Rabin automata to Büchi automata. It finds this reduces the size of resulting automata by up to 31% in experiments.
02. chapter 3 lexical analysis

The document discusses lexical analysis in compiler design. It covers the role of the lexical analyzer, tokenization, and representation of tokens using finite automata. Regular expressions are used to formally specify patterns for tokens. A lexical analyzer generator converts these specifications into a finite state machine (FSM) implementation to recognize tokens in the input stream. The FSM is typically a deterministic finite automaton (DFA) for efficiency, even though a nondeterministic finite automaton (NFA) may require fewer states.
Comparative Report Ed098

This page is intentionally left blank. The following document discusses algorithms for finding minimum spanning trees (MSTs) in graphs, including:
1) Methods for constructing graphs containing the MST generalize to higher dimensions, though some results are less informative in higher dimensions.
2) Yao's algorithm finds MSTs in higher dimensions in time proportional to the number of points raised to a power that depends on the dimension.
3) Agarwal et al. presented a more efficient method using bichromatic nearest neighbors, showing that finding MST edges is no harder than computing bichromatic nearest neighbors.
Similar to Chapter 2 2 1 2 (18)
CS 162 Fall 2015 Homework 1 Problems September 29, 2015 Timothy Johnson 1. Ex...

CS 162 Fall 2015 Homework 1 Problems September 29, 2015 Timothy Johnson 1. Ex...
4-Regular expression to Deterministic Finite Automata (Direct method)-05-05-2...

4-Regular expression to Deterministic Finite Automata (Direct method)-05-05-2...
A class of boundary value methods for the complex delay differential equation

A class of boundary value methods for the complex delay differential equation
Let us c (by yashvant kanetkar) chapter 1 solution

Let us c (by yashvant kanetkar) chapter 1 solution
More from bolovv
Chapter Three(2)

The document summarizes key concepts about context-free grammars and parsing from the book "Compiler Construction: Principles and Practice" by Kenneth C. Louden. It covers notations like EBNF and syntax diagrams for representing grammars, properties of context-free languages, and provides grammar rules and diagrams for a sample TINY language as an example.
Chapter Three(1)

This document discusses context-free grammars and parsing. It defines context-free grammars and how they are used to specify the syntactic structure of programming languages. Key points include:
- Context-free grammars use recursive rules and regular expressions to define a language's syntax.
- Parsing involves using a context-free grammar to derive a syntax tree from a sequence of tokens.
- Derivations show how strings of tokens are generated from a grammar's start symbol through replacements.
- The language defined by a grammar consists of all strings that can be derived from the start symbol.
Chapter Seven(2)

The document discusses runtime environments and memory management techniques for programming languages. It covers stack-based vs dynamic environments, parameter passing mechanisms like pass by value and reference, and garbage collection algorithms. Dynamic memory allocation uses a heap structure with malloc and free functions. Object-oriented languages require special runtime support for objects, inheritance etc. Fully dynamic environments are needed for functional languages that allow nested functions.
Chapter Eight(3)

The document describes code generation for two commercial compilers:
1) The Borland C 3.0 compiler for the 80X86 generates assembly code using static simulation and frame pointers for function calls and local variable access.
2) The Sun 2.0 compiler for SPARCstations uses register-based calling conventions and generates efficient SPARC assembly code.
Both compilers handle code generation for arithmetic expressions, arrays, structures, pointers, control flow, and function calls.
Chapter Five(2)

The document discusses bottom-up parsing techniques, including LR(0), SLR(1), and LR(1) parsing. It describes the construction of finite automata from grammar rules to represent the states and transitions of these parsing approaches. The key aspects covered are:
1) The definitions and algorithms for SLR(1) and LR(1) parsing, which extend LR(0) parsing by using lookahead tokens to resolve parsing conflicts.
2) Sources of parsing conflicts like shift-reduce conflicts and reduce-reduce conflicts that can occur for some grammars with these techniques.
3) The limits of SLR(1) parsing power and how some grammars require the more general LR(
Chapter One

This document provides an overview of compiler construction principles and practices. It introduces the basic components of a compiler, including scanning, parsing, semantic analysis, code generation, and optimization phases. It also discusses related tools like assemblers, linkers, and debuggers. The document outlines the translation process from source code to target code and describes major data structures used in compilers like symbol tables and syntax trees.
Chapter Seven(1)

The document discusses different runtime environments for programming languages:
(1) Fully static environments where all data remains fixed in memory like FORTRAN77. No dynamic allocation.
(2) Stack-based environments used by languages allowing recursion and dynamic allocation like C/C++. Activation records are allocated on a runtime stack.
(3) Dynamic environments like LISP where data is allocated on a heap.
It covers key aspects of runtime environments like memory organization, calling conventions, parameter passing, and handling local variables and procedures. Different languages require different solutions for variable-length data, nested declarations, non-local references, and procedure parameters.
Chapter Two(1)

The document discusses scanning (lexical analysis) in compiler construction. It covers the scanning process, regular expressions, and finite automata. The scanning process identifies tokens from source code by categorizing characters as reserved words, special symbols, or other tokens. Regular expressions are used to represent patterns of character strings and define the language of tokens. Finite automata are mathematical models for describing scanning algorithms using states, transitions, and acceptance.
Chapter 1 1

The document describes the structure and process of a compiler. It discusses the major phases of a compiler including scanning, parsing, semantic analysis, code generation and optimization. It also summarizes the key data structures used in a compiler like the symbol table and syntax tree. The document uses the TINY programming language and its compiler for the TM machine as an example to illustrate the compiler construction process.
More from bolovv (9)
Recently uploaded
Fueling AI with Great Data with Airbyte Webinar

This talk will focus on how to collect data from a variety of sources, leveraging this data for RAG and other GenAI use cases, and finally charting your course to productionalization.
How to Interpret Trends in the Kalyan Rajdhani Mix Chart.pdf

A Mix Chart displays historical data of numbers in a graphical or tabular form. The Kalyan Rajdhani Mix Chart specifically shows the results of a sequence of numbers over different periods.
Taking AI to the Next Level in Manufacturing.pdf

Read Taking AI to the Next Level in Manufacturing to gain insights on AI adoption in the manufacturing industry, such as:
1. How quickly AI is being implemented in manufacturing.
2. Which barriers stand in the way of AI adoption.
3. How data quality and governance form the backbone of AI.
4. Organizational processes and structures that may inhibit effective AI adoption.
6. Ideas and approaches to help build your organization's AI strategy.
Energy Efficient Video Encoding for Cloud and Edge Computing Instances

Energy Efficient Video Encoding for Cloud and Edge Computing Instances
Choosing The Best AWS Service For Your Website + API.pptx

Have you ever been confused by the myriad of choices offered by AWS for hosting a website or an API?
Lambda, Elastic Beanstalk, Lightsail, Amplify, S3 (and more!) can each host websites + APIs. But which one should we choose?
Which one is cheapest? Which one is fastest? Which one will scale to meet our needs?
Join me in this session as we dive into each AWS hosting service to determine which one is best for your scenario and explain why!
OpenID AuthZEN Interop Read Out - Authorization

During Identiverse 2024 and EIC 2024, members of the OpenID AuthZEN WG got together and demoed their authorization endpoints conforming to the AuthZEN API
Your One-Stop Shop for Python Success: Top 10 US Python Development Providers

Simplify your search for a reliable Python development partner! This list presents the top 10 trusted US providers offering comprehensive Python development services, ensuring your project's success from conception to completion.
Main news related to the CCS TSI 2023 (2023/1695)

An English 🇬🇧 translation of a presentation to the speech I gave about the main changes brought by CCS TSI 2023 at the biggest Czech conference on Communications and signalling systems on Railways, which was held in Clarion Hotel Olomouc from 7th to 9th November 2023 (konferenceszt.cz). Attended by around 500 participants and 200 on-line followers.
The original Czech 🇨🇿 version of the presentation can be found here: https://www.slideshare.net/slideshow/hlavni-novinky-souvisejici-s-ccs-tsi-2023-2023-1695/269688092 .
The videorecording (in Czech) from the presentation is available here: https://youtu.be/WzjJWm4IyPk?si=SImb06tuXGb30BEH .
Introduction of Cybersecurity with OSS at Code Europe 2024

I develop the Ruby programming language, RubyGems, and Bundler, which are package managers for Ruby. Today, I will introduce how to enhance the security of your application using open-source software (OSS) examples from Ruby and RubyGems.
The first topic is CVE (Common Vulnerabilities and Exposures). I have published CVEs many times. But what exactly is a CVE? I'll provide a basic understanding of CVEs and explain how to detect and handle vulnerabilities in OSS.
Next, let's discuss package managers. Package managers play a critical role in the OSS ecosystem. I'll explain how to manage library dependencies in your application.
I'll share insights into how the Ruby and RubyGems core team works to keep our ecosystem safe. By the end of this talk, you'll have a better understanding of how to safeguard your code.
Driving Business Innovation: Latest Generative AI Advancements & Success Story

Are you ready to revolutionize how you handle data? Join us for a webinar where we’ll bring you up to speed with the latest advancements in Generative AI technology and discover how leveraging FME with tools from giants like Google Gemini, Amazon, and Microsoft OpenAI can supercharge your workflow efficiency.
During the hour, we’ll take you through:
Guest Speaker Segment with Hannah Barrington: Dive into the world of dynamic real estate marketing with Hannah, the Marketing Manager at Workspace Group. Hear firsthand how their team generates engaging descriptions for thousands of office units by integrating diverse data sources—from PDF floorplans to web pages—using FME transformers, like OpenAIVisionConnector and AnthropicVisionConnector. This use case will show you how GenAI can streamline content creation for marketing across the board.
Ollama Use Case: Learn how Scenario Specialist Dmitri Bagh has utilized Ollama within FME to input data, create custom models, and enhance security protocols. This segment will include demos to illustrate the full capabilities of FME in AI-driven processes.
Custom AI Models: Discover how to leverage FME to build personalized AI models using your data. Whether it’s populating a model with local data for added security or integrating public AI tools, find out how FME facilitates a versatile and secure approach to AI.
We’ll wrap up with a live Q&A session where you can engage with our experts on your specific use cases, and learn more about optimizing your data workflows with AI.
This webinar is ideal for professionals seeking to harness the power of AI within their data management systems while ensuring high levels of customization and security. Whether you're a novice or an expert, gain actionable insights and strategies to elevate your data processes. Join us to see how FME and AI can revolutionize how you work with data!
How to Get CNIC Information System with Paksim Ga.pptx

Pakdata Cf is a groundbreaking system designed to streamline and facilitate access to CNIC information. This innovative platform leverages advanced technology to provide users with efficient and secure access to their CNIC details.
HCL Notes und Domino Lizenzkostenreduzierung in der Welt von DLAU

Webinar Recording: https://www.panagenda.com/webinars/hcl-notes-und-domino-lizenzkostenreduzierung-in-der-welt-von-dlau/
DLAU und die Lizenzen nach dem CCB- und CCX-Modell sind für viele in der HCL-Community seit letztem Jahr ein heißes Thema. Als Notes- oder Domino-Kunde haben Sie vielleicht mit unerwartet hohen Benutzerzahlen und Lizenzgebühren zu kämpfen. Sie fragen sich vielleicht, wie diese neue Art der Lizenzierung funktioniert und welchen Nutzen sie Ihnen bringt. Vor allem wollen Sie sicherlich Ihr Budget einhalten und Kosten sparen, wo immer möglich. Das verstehen wir und wir möchten Ihnen dabei helfen!
Wir erklären Ihnen, wie Sie häufige Konfigurationsprobleme lösen können, die dazu führen können, dass mehr Benutzer gezählt werden als nötig, und wie Sie überflüssige oder ungenutzte Konten identifizieren und entfernen können, um Geld zu sparen. Es gibt auch einige Ansätze, die zu unnötigen Ausgaben führen können, z. B. wenn ein Personendokument anstelle eines Mail-Ins für geteilte Mailboxen verwendet wird. Wir zeigen Ihnen solche Fälle und deren Lösungen. Und natürlich erklären wir Ihnen das neue Lizenzmodell.
Nehmen Sie an diesem Webinar teil, bei dem HCL-Ambassador Marc Thomas und Gastredner Franz Walder Ihnen diese neue Welt näherbringen. Es vermittelt Ihnen die Tools und das Know-how, um den Überblick zu bewahren. Sie werden in der Lage sein, Ihre Kosten durch eine optimierte Domino-Konfiguration zu reduzieren und auch in Zukunft gering zu halten.
Diese Themen werden behandelt
- Reduzierung der Lizenzkosten durch Auffinden und Beheben von Fehlkonfigurationen und überflüssigen Konten
- Wie funktionieren CCB- und CCX-Lizenzen wirklich?
- Verstehen des DLAU-Tools und wie man es am besten nutzt
- Tipps für häufige Problembereiche, wie z. B. Team-Postfächer, Funktions-/Testbenutzer usw.
- Praxisbeispiele und Best Practices zum sofortigen Umsetzen
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Discover how MongoDB Atlas and vector search technology can revolutionize your application's search capabilities. This comprehensive presentation covers:
* What is Vector Search?
* Importance and benefits of vector search
* Practical use cases across various industries
* Step-by-step implementation guide
* Live demos with code snippets
* Enhancing LLM capabilities with vector search
* Best practices and optimization strategies
Perfect for developers, AI enthusiasts, and tech leaders. Learn how to leverage MongoDB Atlas to deliver highly relevant, context-aware search results, transforming your data retrieval process. Stay ahead in tech innovation and maximize the potential of your applications.
#MongoDB #VectorSearch #AI #SemanticSearch #TechInnovation #DataScience #LLM #MachineLearning #SearchTechnology
Project Management Semester Long Project - Acuity

Acuity is an innovative learning app designed to transform the way you engage with knowledge. Powered by AI technology, Acuity takes complex topics and distills them into concise, interactive summaries that are easy to read & understand. Whether you're exploring the depths of quantum mechanics or seeking insight into historical events, Acuity provides the key information you need without the burden of lengthy texts.
Building Production Ready Search Pipelines with Spark and Milvus

Spark is the widely used ETL tool for processing, indexing and ingesting data to serving stack for search. Milvus is the production-ready open-source vector database. In this talk we will show how to use Spark to process unstructured data to extract vector representations, and push the vectors to Milvus vector database for search serving.
Recently uploaded (20)
How to Interpret Trends in the Kalyan Rajdhani Mix Chart.pdf

How to Interpret Trends in the Kalyan Rajdhani Mix Chart.pdf
Nordic Marketo Engage User Group_June 13_ 2024.pptx

Nordic Marketo Engage User Group_June 13_ 2024.pptx
Energy Efficient Video Encoding for Cloud and Edge Computing Instances

Energy Efficient Video Encoding for Cloud and Edge Computing Instances
Choosing The Best AWS Service For Your Website + API.pptx

Choosing The Best AWS Service For Your Website + API.pptx
Your One-Stop Shop for Python Success: Top 10 US Python Development Providers

Your One-Stop Shop for Python Success: Top 10 US Python Development Providers
Introduction of Cybersecurity with OSS at Code Europe 2024

Introduction of Cybersecurity with OSS at Code Europe 2024
Driving Business Innovation: Latest Generative AI Advancements & Success Story

Driving Business Innovation: Latest Generative AI Advancements & Success Story
How to Get CNIC Information System with Paksim Ga.pptx

How to Get CNIC Information System with Paksim Ga.pptx
HCL Notes und Domino Lizenzkostenreduzierung in der Welt von DLAU

HCL Notes und Domino Lizenzkostenreduzierung in der Welt von DLAU
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf
WeTestAthens: Postman's AI & Automation Techniques

WeTestAthens: Postman's AI & Automation Techniques
Building Production Ready Search Pipelines with Spark and Milvus

Building Production Ready Search Pipelines with Spark and Milvus
Chapter 2 2 1 2
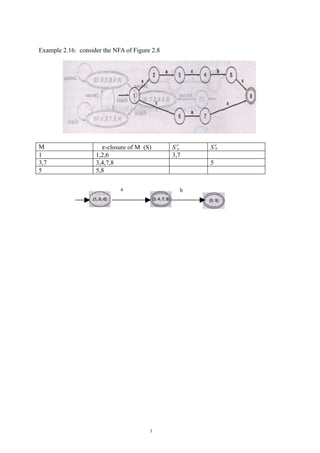
- 1. Example 2.16: consider the NFA of Figure 2.8 M ε-closure of M (S) S′a S′b 1 1,2,6 3,7 3,7 3,4,7,8 5 5 5,8 a b 1
- 2. Example 2.17: consider the NFA of Figure 2.9 (regular expression letter(letter|digit)*) M ε-closure of M (S) S′letter S′digit 1 1 2 2 2,3,4,5,7,10 6 8 6 4,5,6,7,9,10 6 8 8 4,5,7,8,9,10 6 8 le tte r 2
- 3. 2.4.3 Simulating an NFA using the subset construction As mentioned at section 2.3. NFAs can be implemented in similar ways to DFAs, except that since NFAs are nondeterministic, there are potentially many different sequences of transitions that must be tried. A program that simulates an NFA must store up transitions that have not yet been tried and backtrack to them on failure. An other way of simulating an NFA is to use the subset construction, but instead of constructing all the states of the associated DFA, we construct only the state at each point that is indicated by the next input character. The advantage: we may not need to construct the entire DFA. In example 2.16, the input string consisting of the single character a. a b The disadvantage: a state may be constructed many times, if the path contains loops. In example 2.17, given the input string r2d3 2.4.4 Minimizing the number of states in a DFA The process we have described of deriving a DFA algorithmically from a regular expression has the unfortunate property that the resulting DFA may be more complex than necessary. For example 2.15 we derived the DFA for the regular expression a*: whereas the DFA will do as well. a 3
- 4. An important result from automata theory states that, given any DFA, there is an equivalent DFA containing a minimum number of states, and, that this minimum-state DFA is unique (except for renaming of states). It is also possible to directly obtain this minimum-state DFA from any given DFA. Given the algorithm as follow: (1) It begins with the most optimistic assumption possible. It creates two sets, one consisting of all the accepting states and the other consisting of all the non-accepting states. (2) Given this partition of the states of the original DFA, consider the transitions on each character a of the alphabet. If all accepting states have transitions on a to accepting states, then this defines an a-transition from the new accepting state (the set of all the old accepting states) to itself. If all accepting states have transitions on a to non-accepting states, then this defines an a-transition from the new accepting state to the new non- accepting state (the set of all the old non-accepting stales). On the other hand, if there are two accepting states s and t that have transitions on a that land in different sets, then no a-transition can be defined for this grouping of the states. We say that a distinguishes the states s and t We must also consider error transitions to an error state that is non- accepting. If there are accepting states s and t such that s has an a-transition to another accepting state, while t has no a-transition at all (i.e., an error transition), then a distinguishes s and t. (3) If any further sets are split, we must return and repeat the process from the beginning. This process continues until either all sets contain only one element (in which case, we have shown the original DFA to be minimal) or until no further splitting of sets occurs. 4
- 5. le tte r Example 2.18: The regular expression letter(letter|digit)* The accepting sets {2,3,4,5,7,10},{4,5,6,7,9,10},{4,5,7,8,9,10} The nonaccepting sets {1} The following minimum-state DFA : letter digit Example 2.19: the regular expression (a| ε)b* The accepting sets {1,2,3} The non-accepting sets state 1 has an a-transition to an accepting state, while states 2 .and 3 have no a-transition (or, rather, an error transition on a to the error nonaccepting state). Thus, a distinguishes state 1 from states 2 and 3, and we must repartition the states into the sets {1} and {2,3}. Now we begin over. The set {1} cannot be split further, so we no longer consider it. Now the states 2 and 3 cannot be distinguished by either a or b. 5