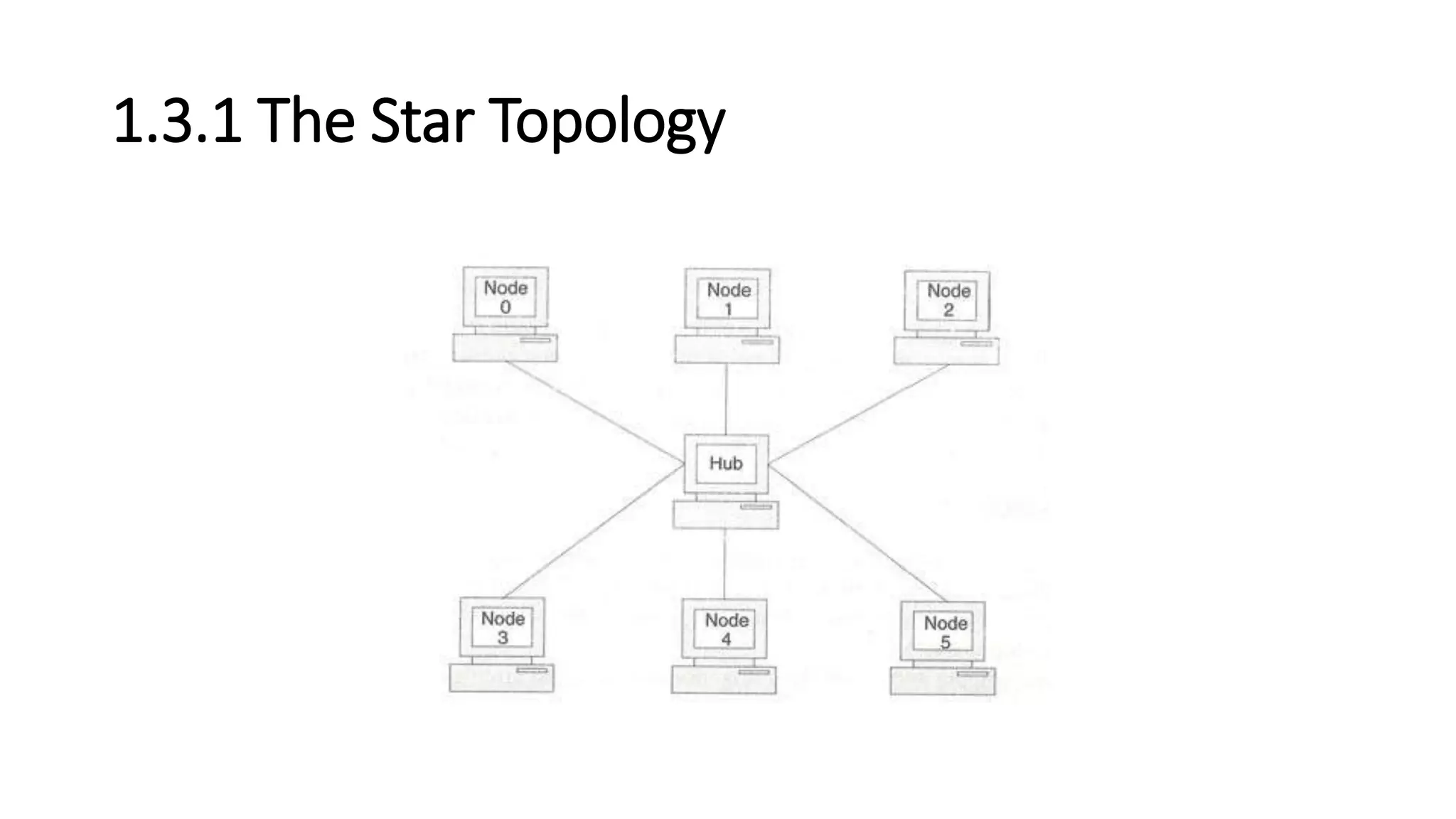
The document introduces computer networks and discusses their history and development. It describes different network topologies like star, bus, ring and hybrid along with their advantages and disadvantages. The document also explains the OSI reference model and describes the functions of the physical and data link layers.