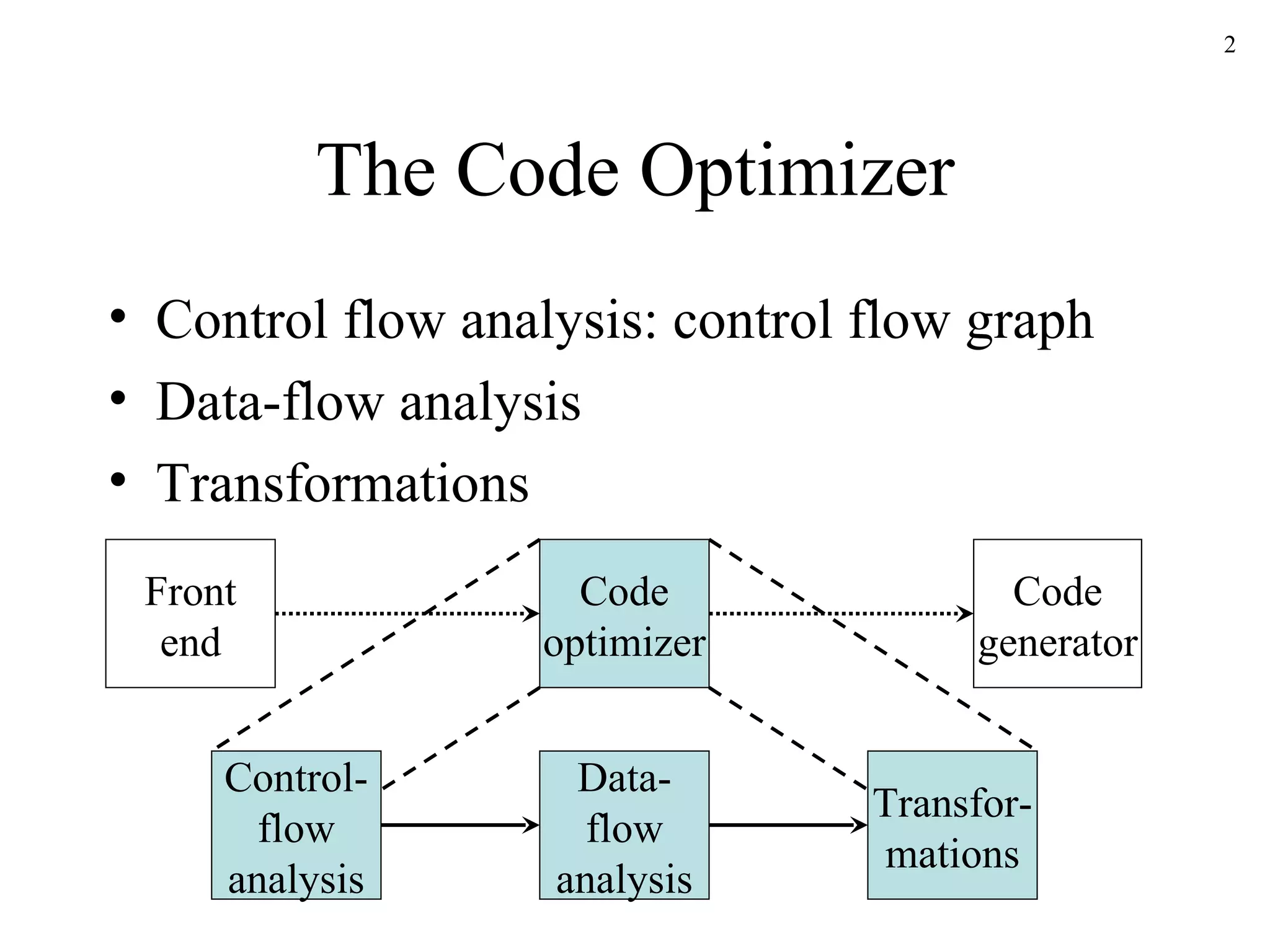
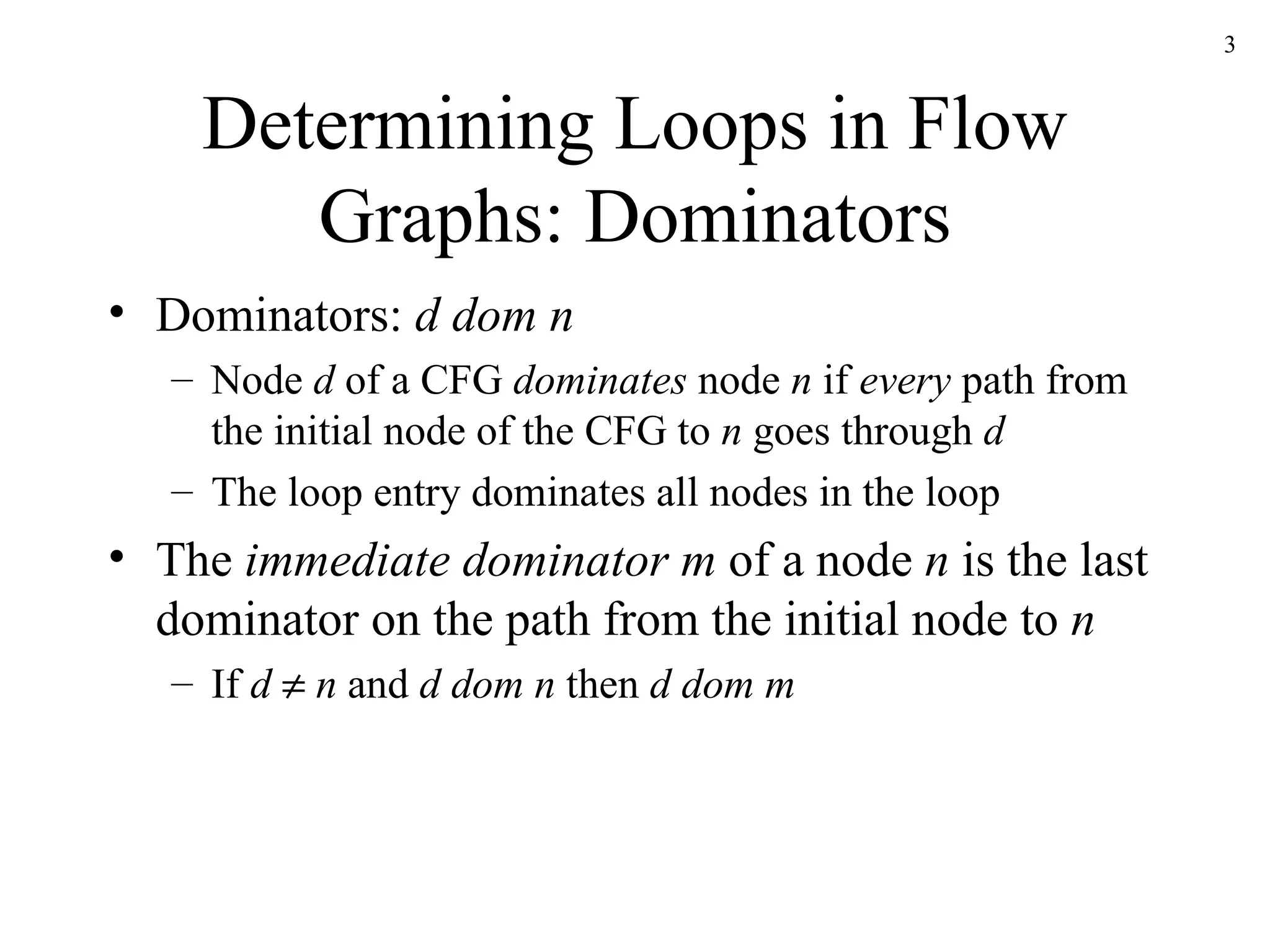
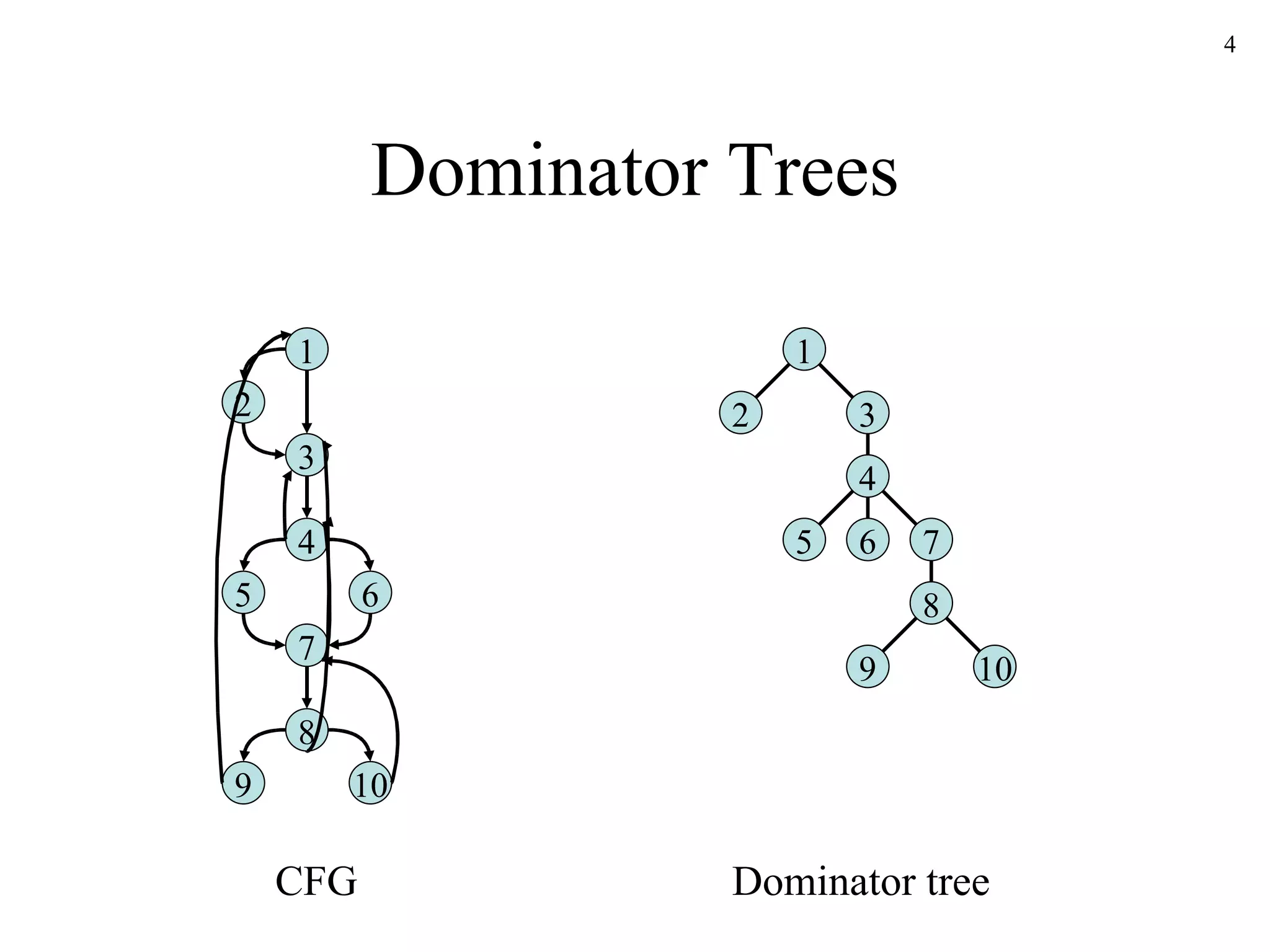
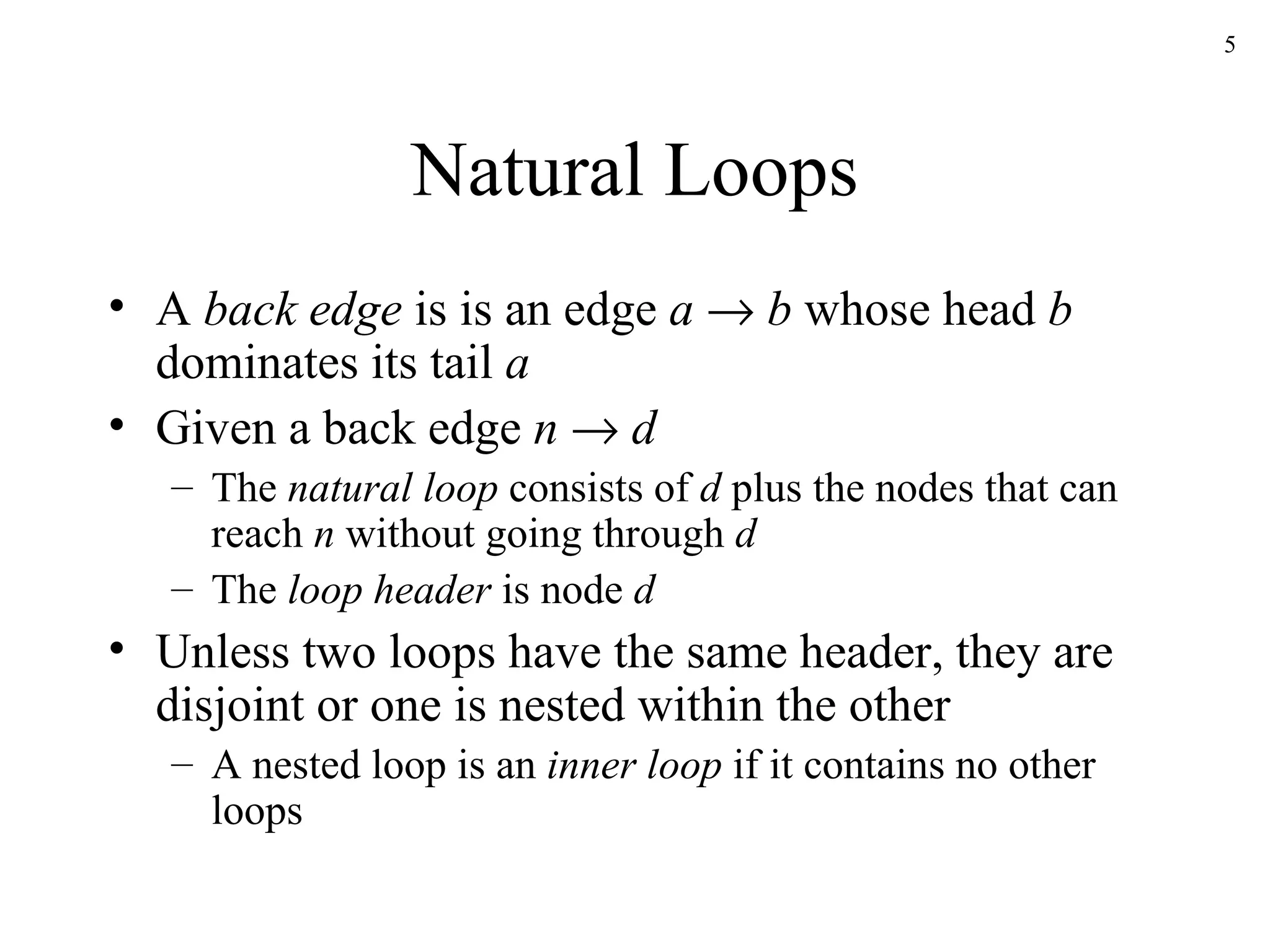
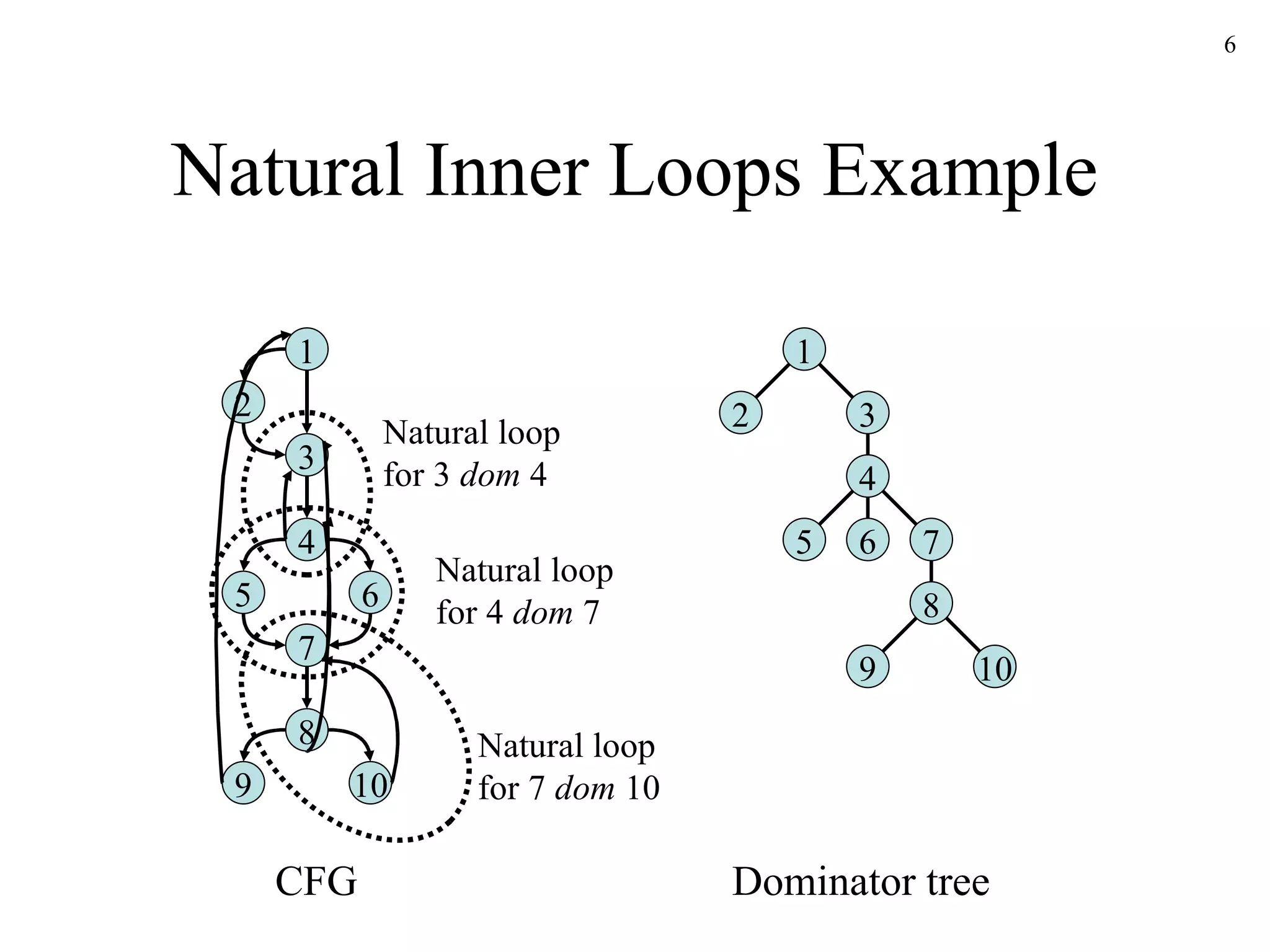
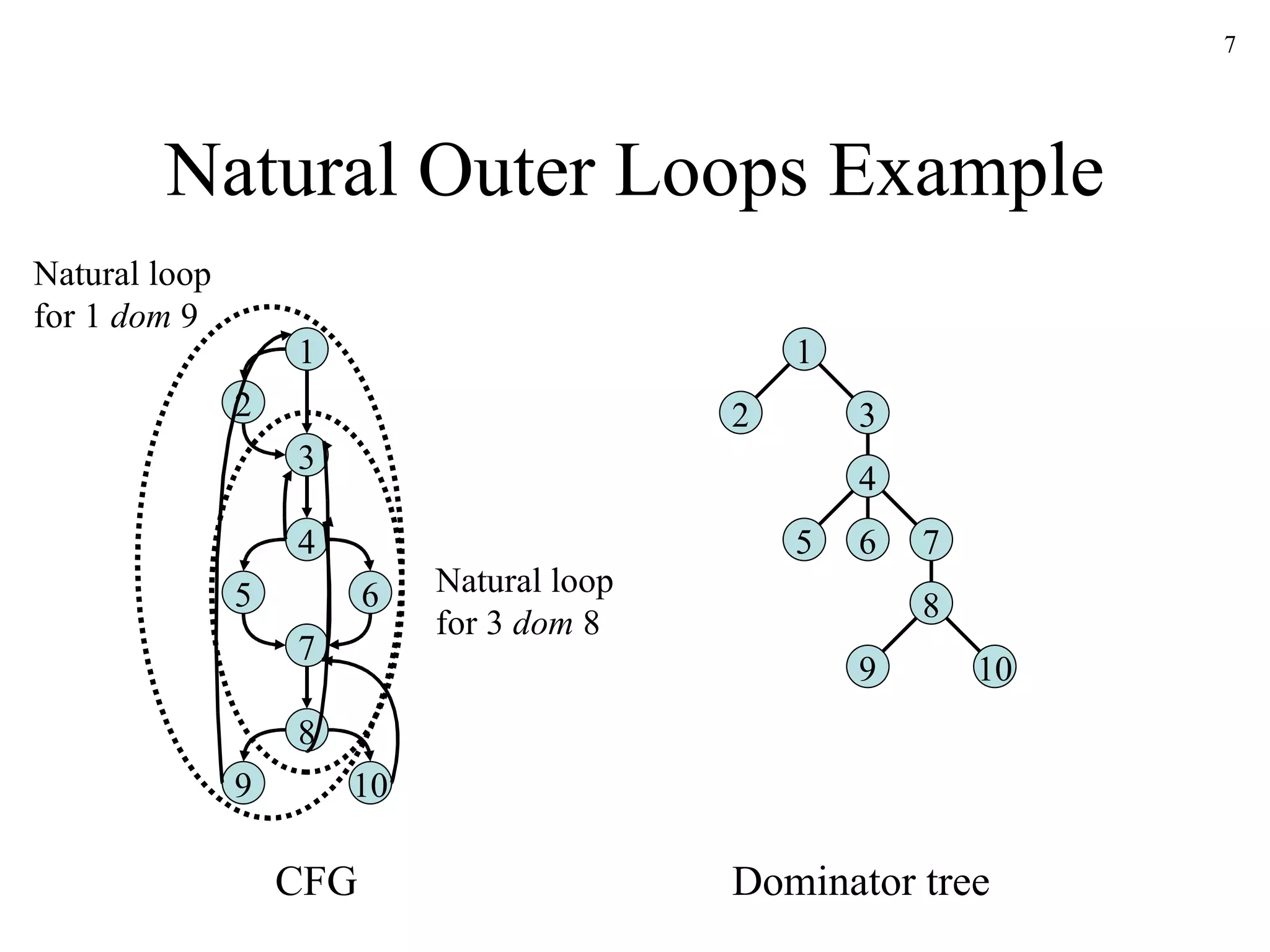
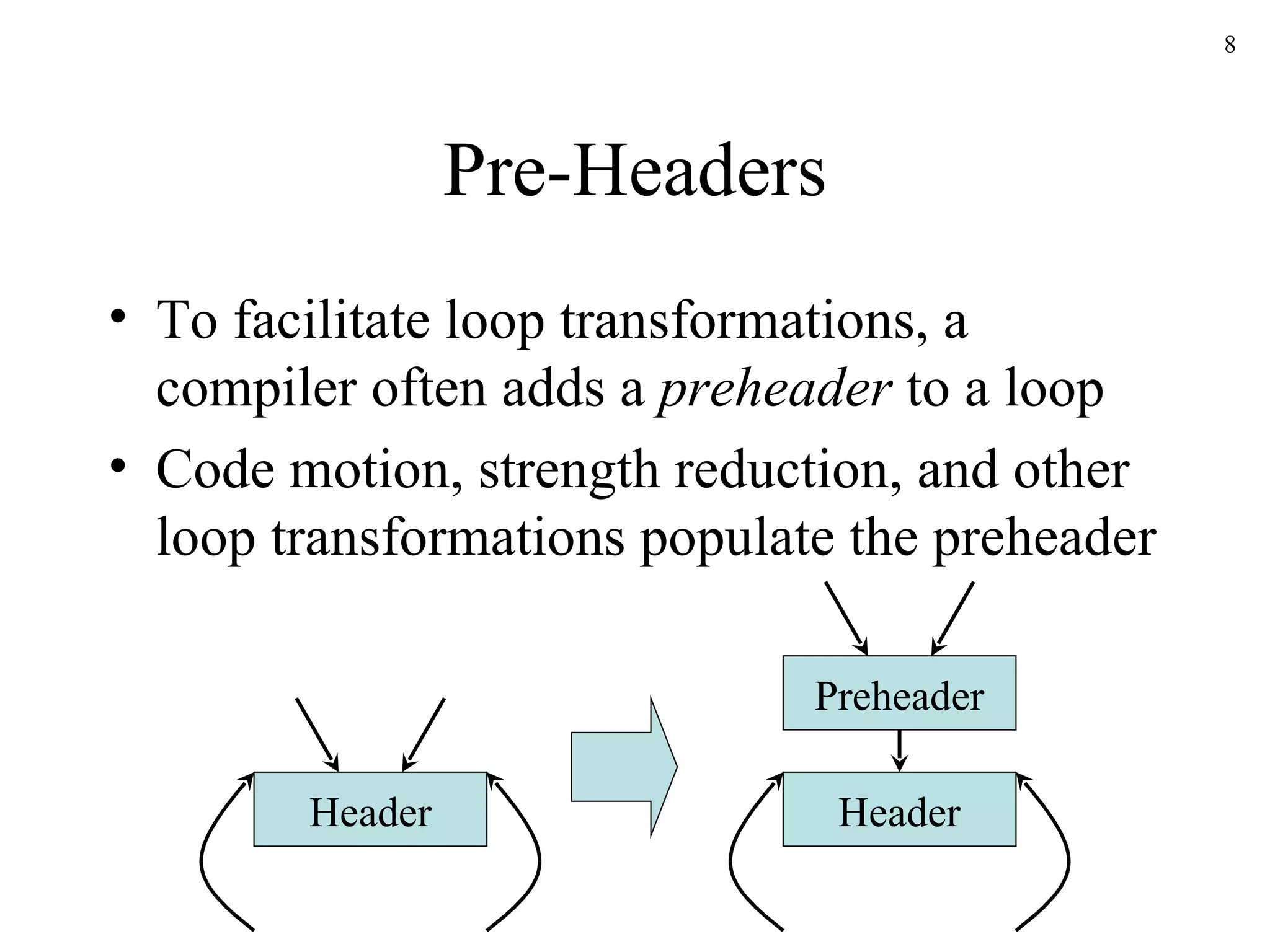
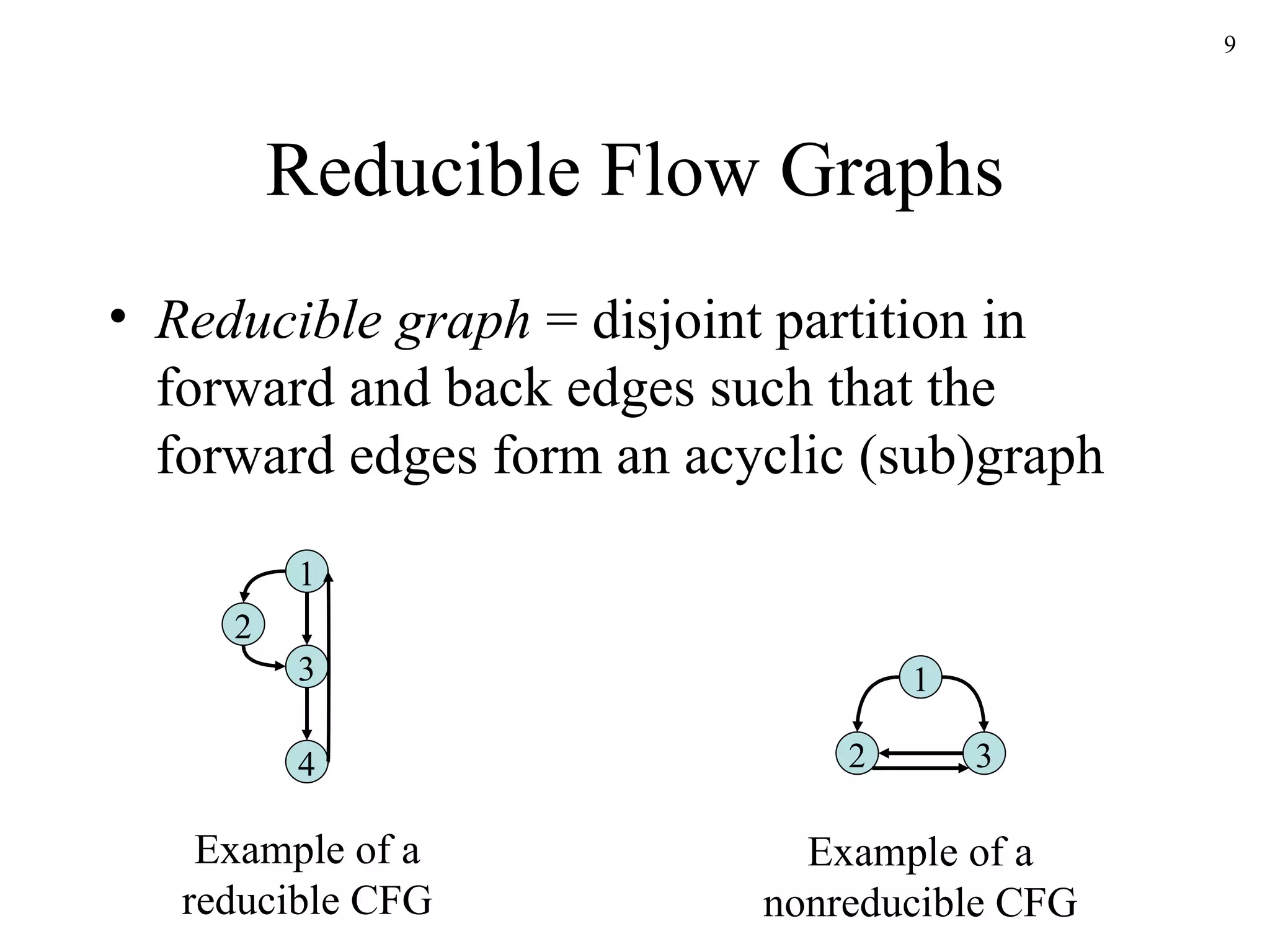
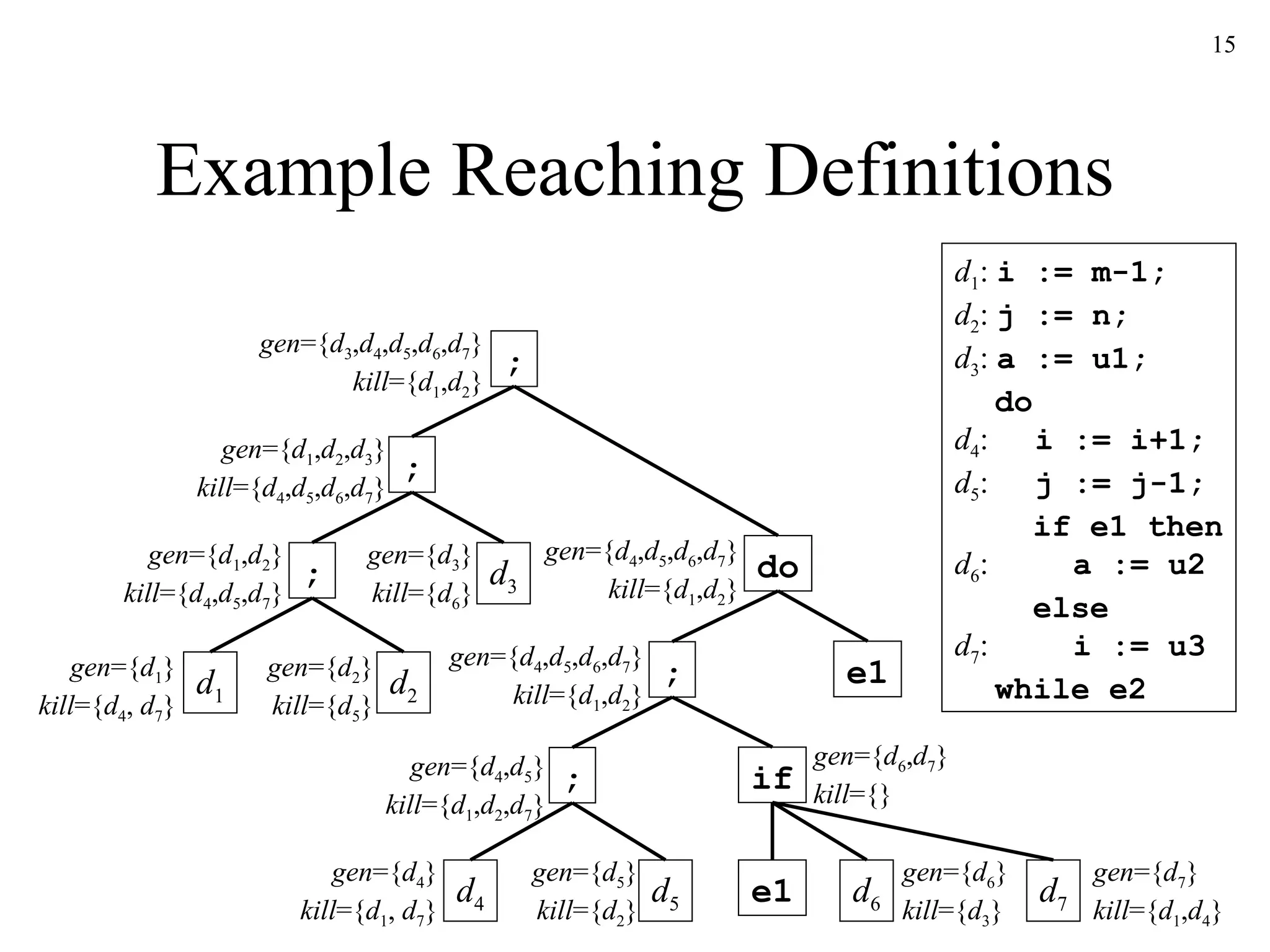
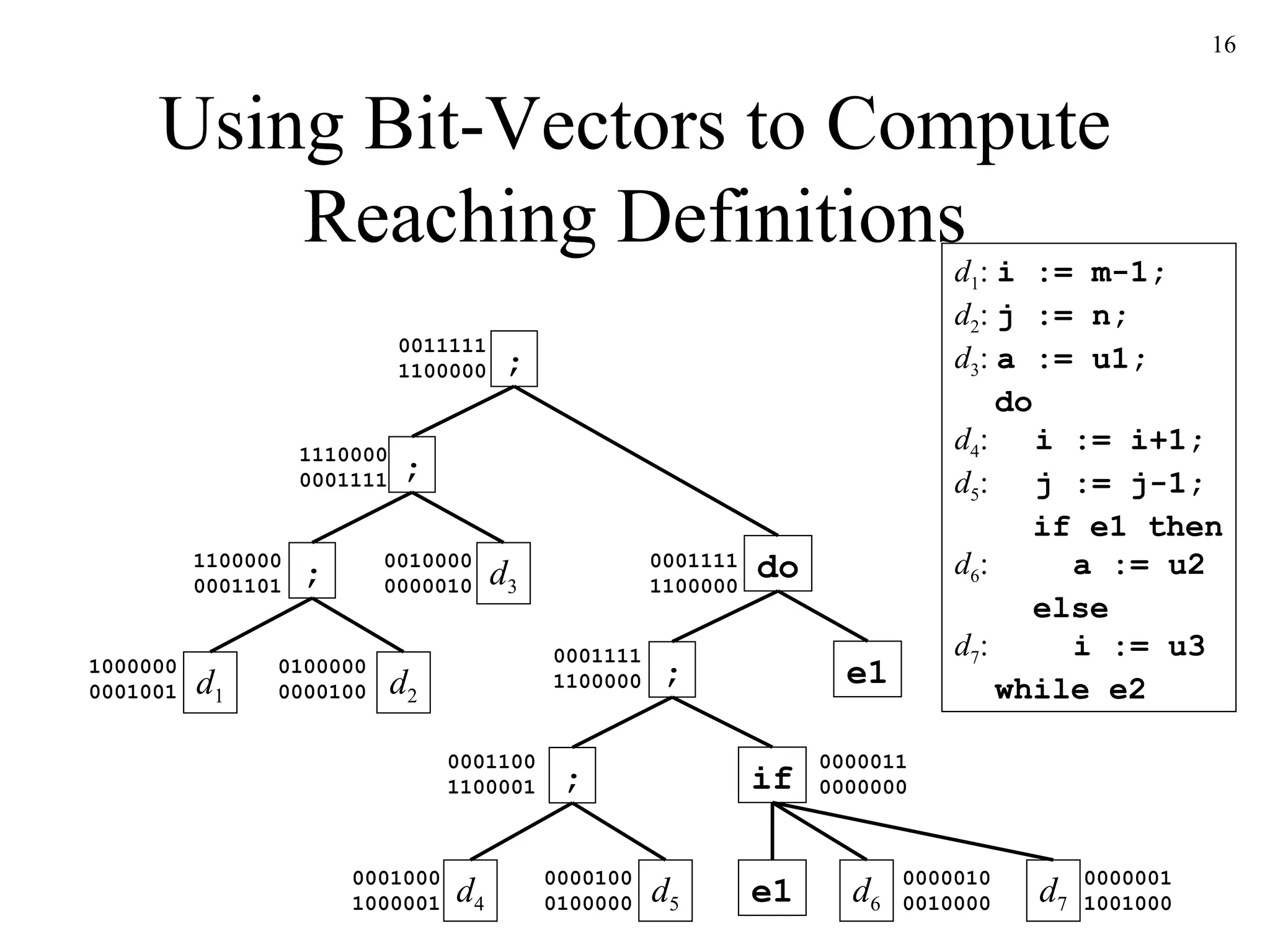
The document discusses code optimization techniques used by compilers, including control flow analysis, data flow analysis, and code transformations. It covers determining loops in a control flow graph using dominators, building dominator trees, and identifying natural loops. It also discusses reaching definitions as a data flow analysis problem and how bit vectors can be used to compute reaching definitions in a conservative manner to ensure safety.

![Global Data-Flow Analysis To apply global optimizations on basic blocks, data-flow information is collected by solving systems of data-flow equations Suppose we need to determine the reaching definitions for a sequence of statements S out [ S ] = gen [ S ] ( in [ S ] - kill [ S ]) d1: i := m-1 d2: j := n d3: j := j-1 B1: B2: B3: out [B1] = gen [B1] = {d1, d2} out [B2] = gen [B2] {d1} = {d1, d3} d1 reaches B2 and B3 and d2 reaches B2, but not B3 because d2 is killed in B2](https://image.slidesharecdn.com/ch10-091220235735-phpapp02/75/Ch10-10-2048.jpg)
![Reaching Definitions S d : a:=b+c Then, the data-flow equations for S are: gen [ S ] = { d } kill [ S ] = D a - { d } out [ S ] = gen [ S ] ( in [ S ] - kill [ S ]) where D a = all definitions of a in the region of code is of the form](https://image.slidesharecdn.com/ch10-091220235735-phpapp02/75/Ch10-11-2048.jpg)
![Reaching Definitions S gen [ S ] = gen [ S 2 ] ( gen [ S 1 ] - kill [ S 2 ]) kill [ S ] = kill [ S 2 ] ( kill [ S 1 ] - gen [ S 2 ]) in [ S 1 ] = in [ S ] in [ S 2 ] = out [ S 1 ] out [ S ] = out [ S 2 ] is of the form S 2 S 1](https://image.slidesharecdn.com/ch10-091220235735-phpapp02/75/Ch10-12-2048.jpg)
![Reaching Definitions S gen [ S ] = gen [ S 1 ] gen [ S 2 ] kill [ S ] = kill [ S 1 ] kill [ S 2 ] in [ S 1 ] = in [ S ] in [ S 2 ] = in [ S ] out [ S ] = out [ S 1 ] out [ S 2 ] is of the form S 2 S 1](https://image.slidesharecdn.com/ch10-091220235735-phpapp02/75/Ch10-13-2048.jpg)
![Reaching Definitions S gen [ S ] = gen [ S 1 ] kill [ S ] = kill [ S 1 ] in [ S 1 ] = in [ S ] gen [ S 1 ] out [ S ] = out [ S 1 ] is of the form S 1](https://image.slidesharecdn.com/ch10-091220235735-phpapp02/75/Ch10-14-2048.jpg)

![Reaching Definitions are a Conservative (Safe) Estimation S 2 S 1 Suppose this branch is never taken Estimation: gen [ S ] = gen [ S 1 ] gen [ S 2 ] kill [ S ] = kill [ S 1 ] kill [ S 2 ] Accurate: gen’ [ S ] = gen [ S 1 ] ⊆ gen [ S ] kill’ [ S ] = kill [ S 1 ] ⊇ kill [ S ]](https://image.slidesharecdn.com/ch10-091220235735-phpapp02/75/Ch10-18-2048.jpg)
![Reaching Definitions are a Conservative (Safe) Estimation in [ S 1 ] = in [ S ] gen [ S 1 ] S 1 Why gen ? S is of the form The problem is that in [ S 1 ] = in [ S ] out [ S 1 ] makes more sense, but we cannot solve this directly, because out [ S 1 ] depends on in [ S 1 ]](https://image.slidesharecdn.com/ch10-091220235735-phpapp02/75/Ch10-19-2048.jpg)
![Reaching Definitions are a Conservative (Safe) Estimation d : a:=b+c We have: (1) in [ S 1 ] = in [ S ] out [ S 1 ] (2) out [ S 1 ] = gen [ S 1 ] ( in [ S 1 ] - kill [ S 1 ]) Solve in [ S 1 ] and out [ S 1 ] by estimating in 1 [ S 1 ] using safe but approximate out [ S 1 ]= , then re-compute out 1 [ S 1 ] using (2) to estimate in 2 [ S 1 ], etc. in 1 [ S 1 ] = (1) in [ S ] out [ S 1 ] = in [ S ] out 1 [ S 1 ] = (2) gen [ S 1 ] ( in 1 [ S 1 ] - kill [ S 1 ]) = gen [ S 1 ] ( in [ S ] - kill [ S 1 ]) in 2 [ S 1 ] = (1) in [ S ] out 1 [ S 1 ] = in [ S ] gen [ S 1 ] ( in [ S ] - kill [ S 1 ]) = in [ S ] gen [ S 1 ] out 2 [ S 1 ] = (2) gen [ S 1 ] ( in 2 [ S 1 ] - kill [ S 1 ]) = gen [ S 1 ] ( in [ S ] gen [ S 1 ] - kill [ S 1 ]) = gen [ S 1 ] ( in [ S ] - kill [ S 1 ]) Because out 1 [ S 1 ] = out 2 [ S 1 ], and therefore in 3 [ S 1 ] = in 2 [ S 1 ], we conclude that in [ S 1 ] = in [ S ] gen [ S 1 ]](https://image.slidesharecdn.com/ch10-091220235735-phpapp02/75/Ch10-20-2048.jpg)