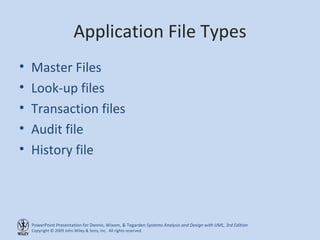
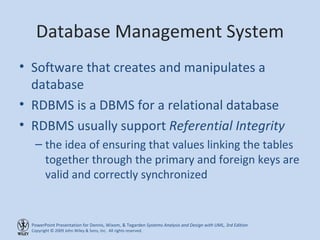
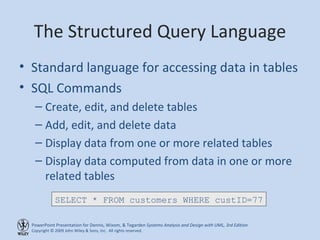
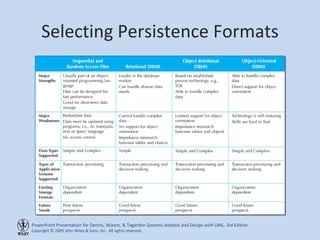
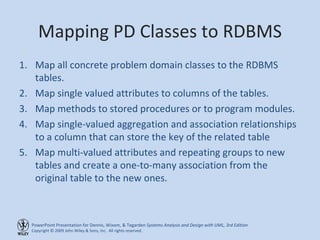
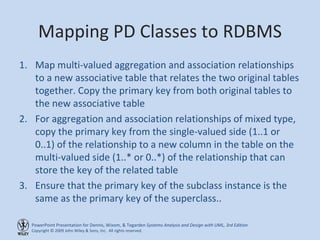
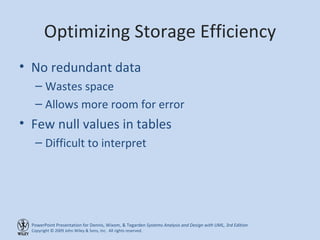
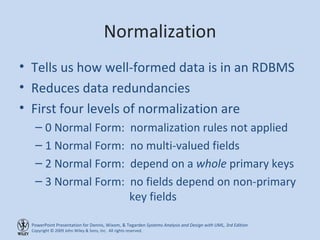
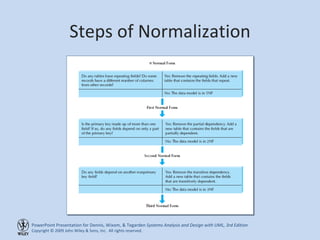
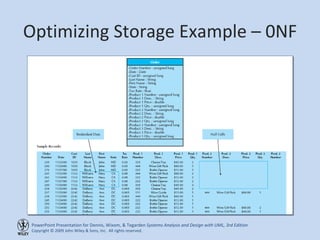
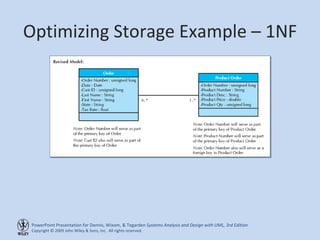
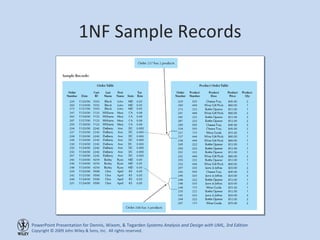
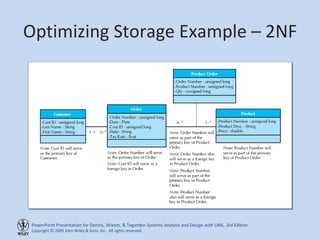
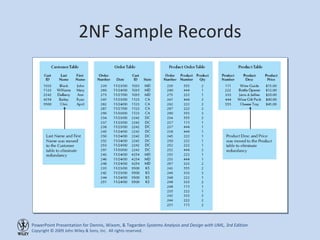
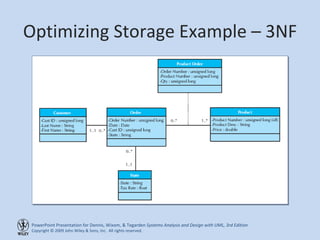
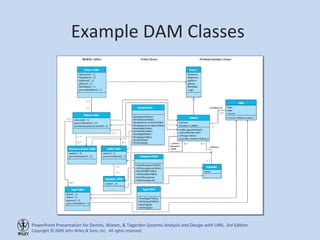
This chapter discusses database design and the data management layer. It covers selecting an object persistence format like files or relational databases, mapping problem domain objects to that format, optimizing the storage through normalization, and designing data access and manipulation classes. The goals are to familiarize with persistence formats, map objects to formats, apply normalization to optimize relational databases, and design data access classes.