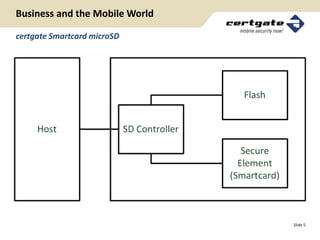
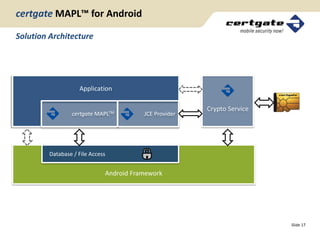
This document discusses a mobile application protection layer called certgate MAPL that provides security for Android applications. It encrypts application data, requires user authentication via PIN, and stores encryption keys securely on a hardware token. The presentation covers certgate as a company, Android security concepts, how MAPL works, its architecture and effects, and benefits like enabling BYOD policies. It concludes by promoting the product and providing a link to learn more.

![Business and the Mobile World
Agenda
About certgate
Mobile Security Solutions
Android Security Concept
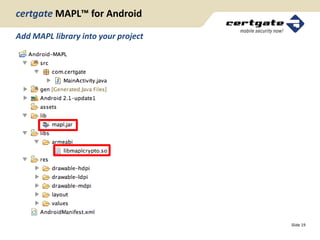
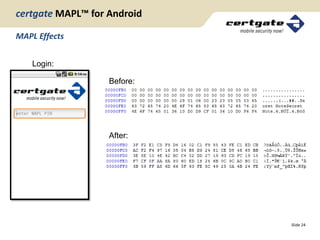
certgate Mobile Application Protection Layer
[Live Demonstration]
Q&A
Slide 3](https://image.slidesharecdn.com/certgate-120409043254-phpapp02/85/Certgate-2-320.jpg)