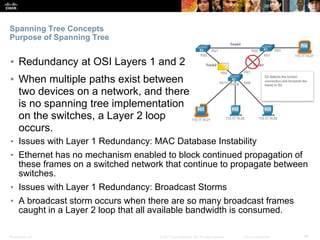
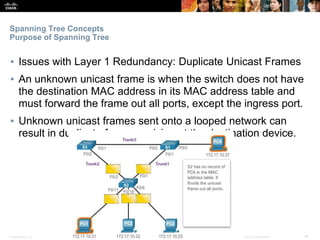
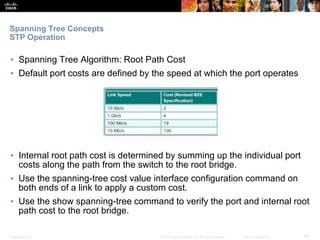
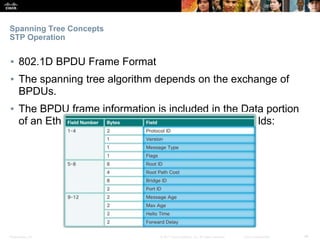
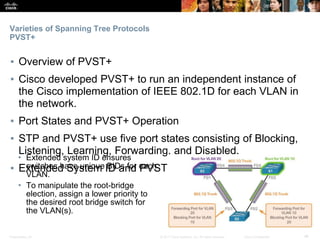
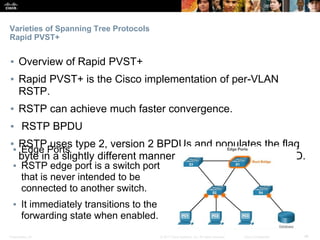
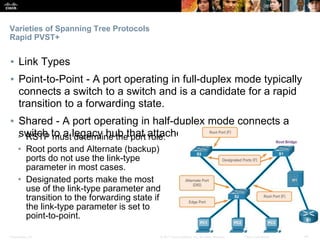
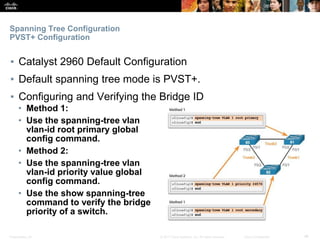
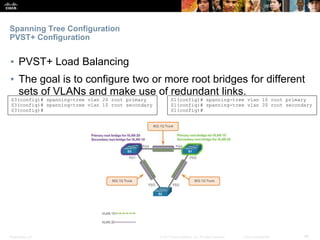
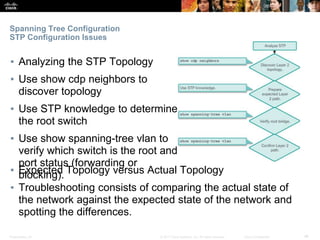
This document discusses spanning tree protocols. It begins by explaining the purpose of STP in preventing layer 2 loops. It then covers different STP varieties like PVST+ and Rapid PVST+, and how they operate independently on each VLAN. The document ends by providing instructions on configuring PVST+ and Rapid PVST+, including setting the root bridge, enabling features like PortFast and BPDU Guard, and troubleshooting the STP topology.