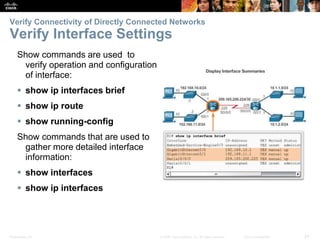
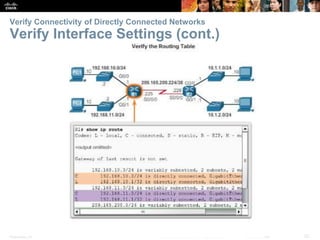
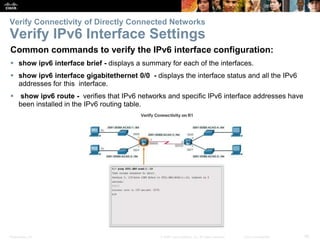
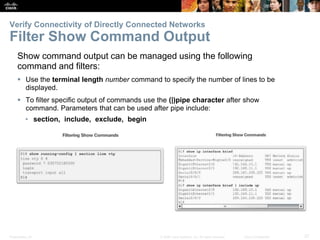
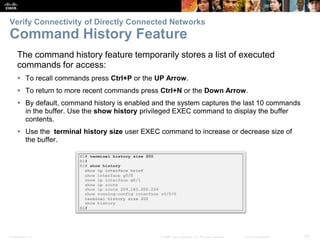
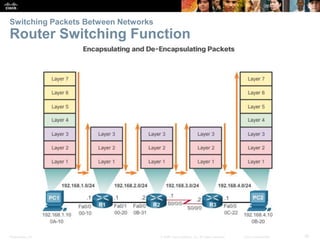
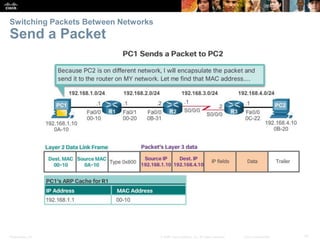
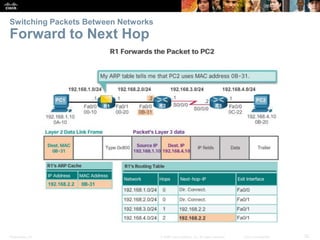
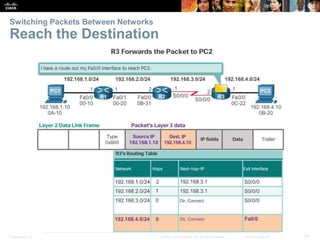
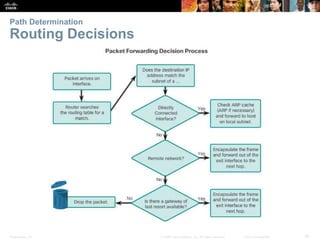
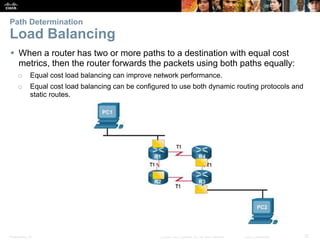
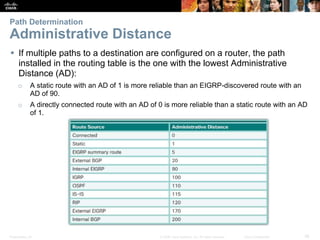
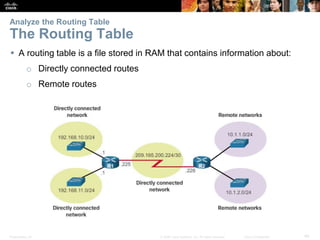
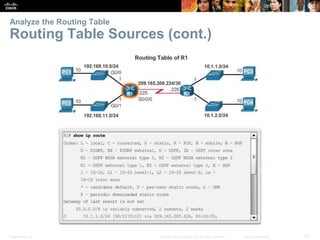
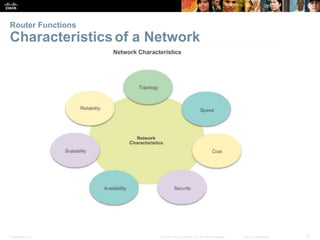
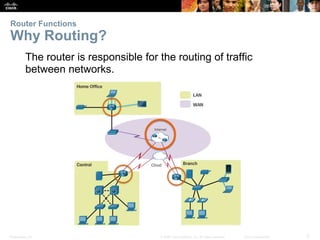
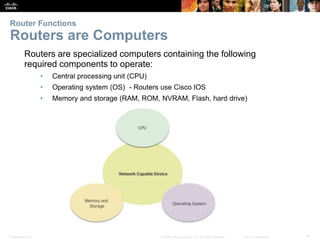
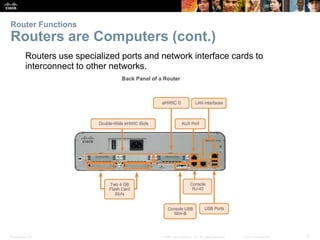
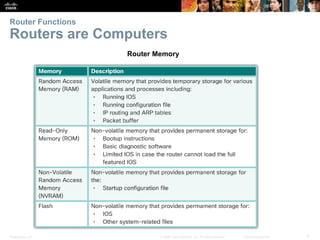
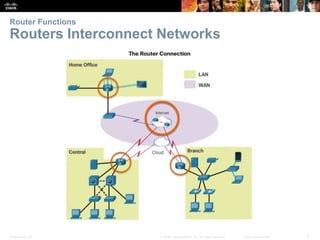
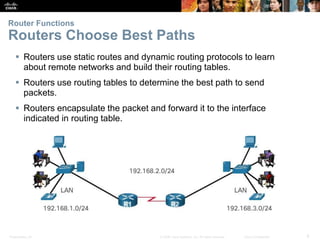
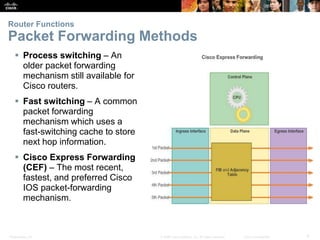
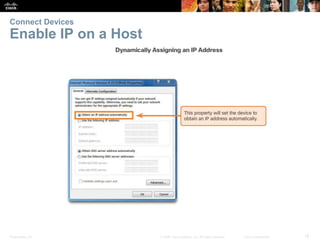
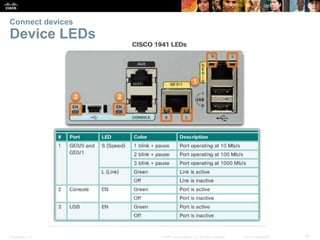
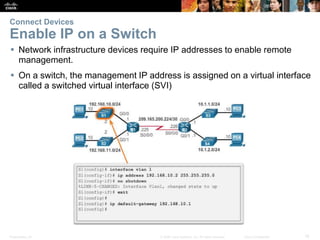
The document outlines the fundamental functions and configurations of routers, detailing their role in routing traffic between networks. It explains router components, routing methods, address configuration, and the importance of both static and dynamic routing protocols in building routing tables. The document also covers basic router settings, verification of connectivity, and the encapsulation process when switching packets.



![Presentation_ID 21© 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential
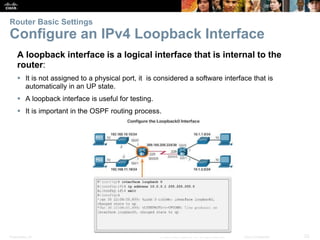
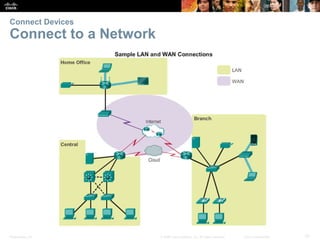
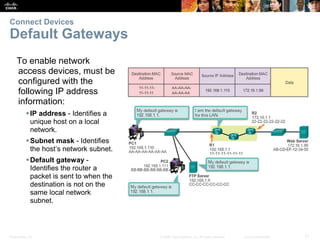
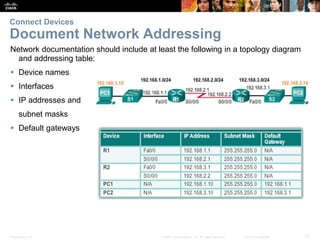
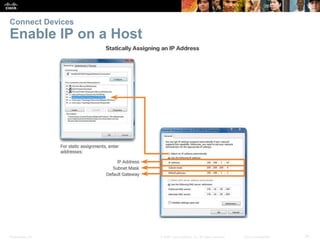
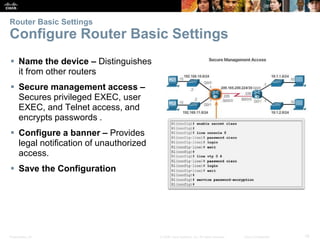
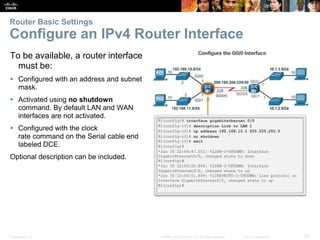
Router Basic Settings
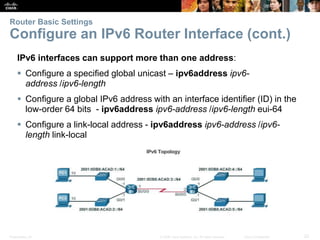
Configure an IPv6 Router Interface
Configure interface with IPv6 address and subnet mask:
Use the ipv6 address ipv6-address/ipv6-length [link-local | eui-64]interface configuration
command.
Activate using the no shutdown command.](https://image.slidesharecdn.com/rse6instructormaterialschapter1-200610102750/85/CCNA-R-S-Module-03-Routing-Switching-Essentials-Chapter-1-21-320.jpg)