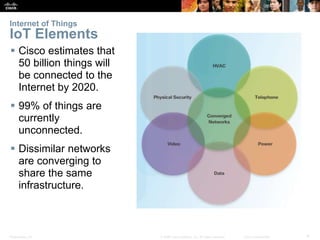
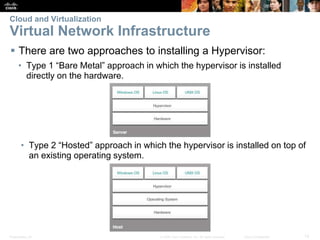
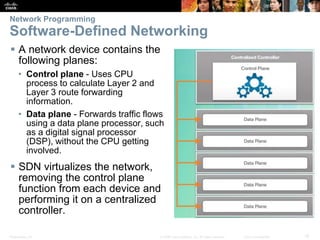
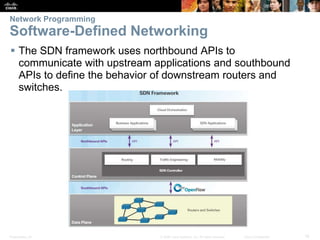
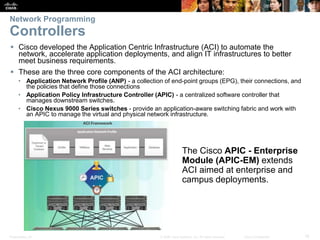
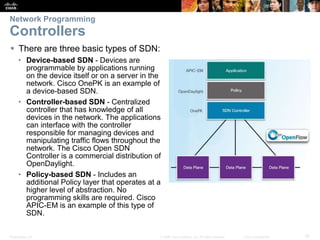
The document covers Chapter 7 on network evolution, focusing on the Internet of Things (IoT), cloud computing, and network programming. Key highlights include the significant growth of IoT expected by 2020, the essential role of cloud services like SaaS and PaaS, and the development of Software-Defined Networking (SDN) to enhance network management and programmability. Additionally, it outlines various cloud models and the three types of SDN—device-based, controller-based, and policy-based, emphasizing the advantages of virtualization and security in evolving networks.