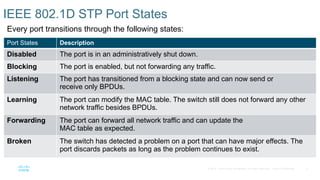
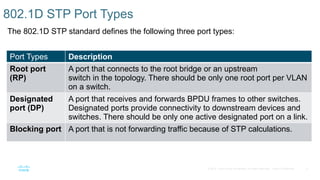
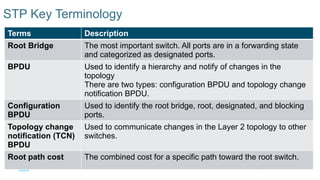
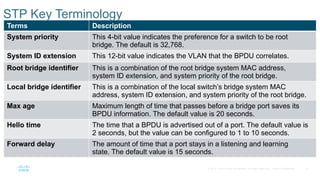
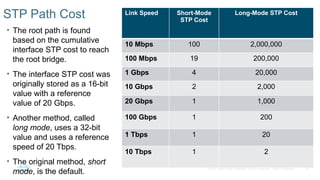
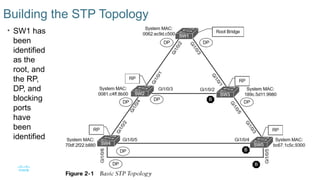
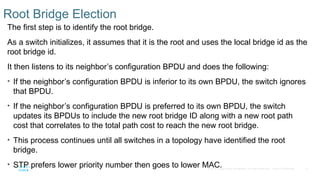
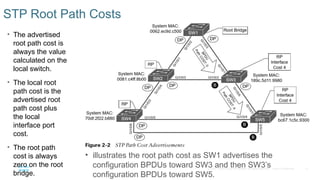
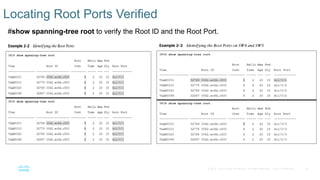
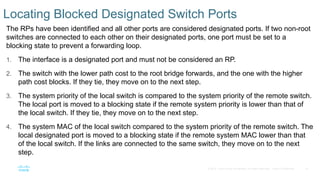
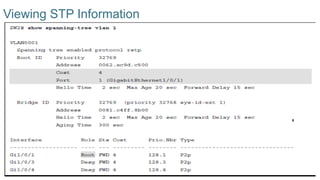
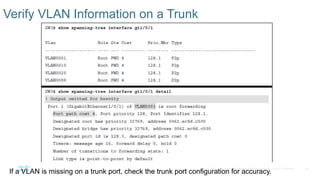
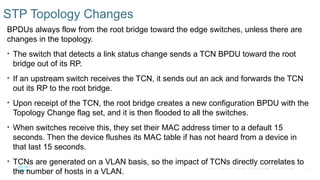
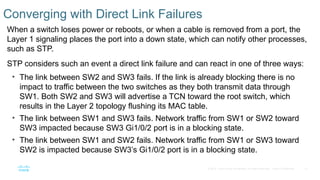
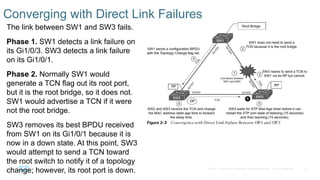
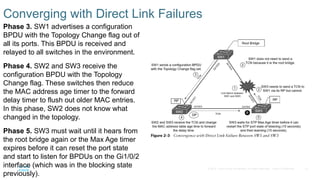
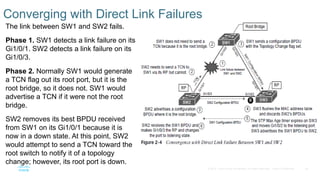
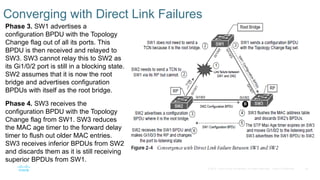
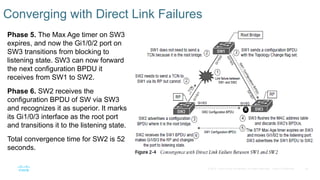
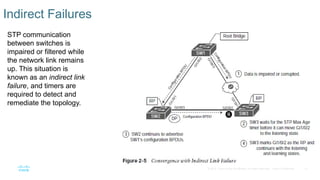
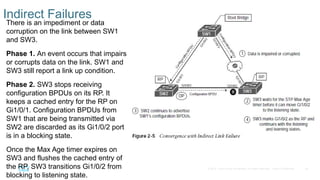
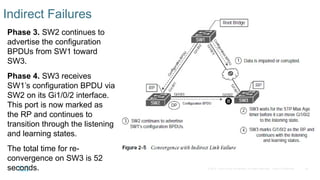
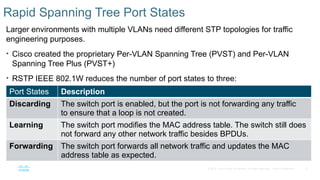
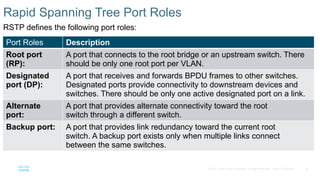
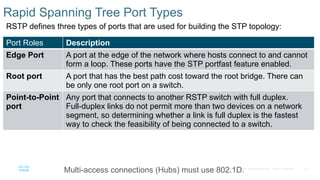
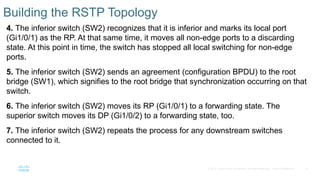
Chapter 2 discusses the fundamentals of spanning tree protocols (STP), including the rapid spanning tree protocol (RSTP) and various STP versions such as 802.1d. It details key concepts like port states, root bridge elections, and how STP manages loops and path costs while providing examples of topology changes and convergence processes. The chapter emphasizes the importance of STP in ensuring network stability and preventing packet loops in switched Ethernet networks.