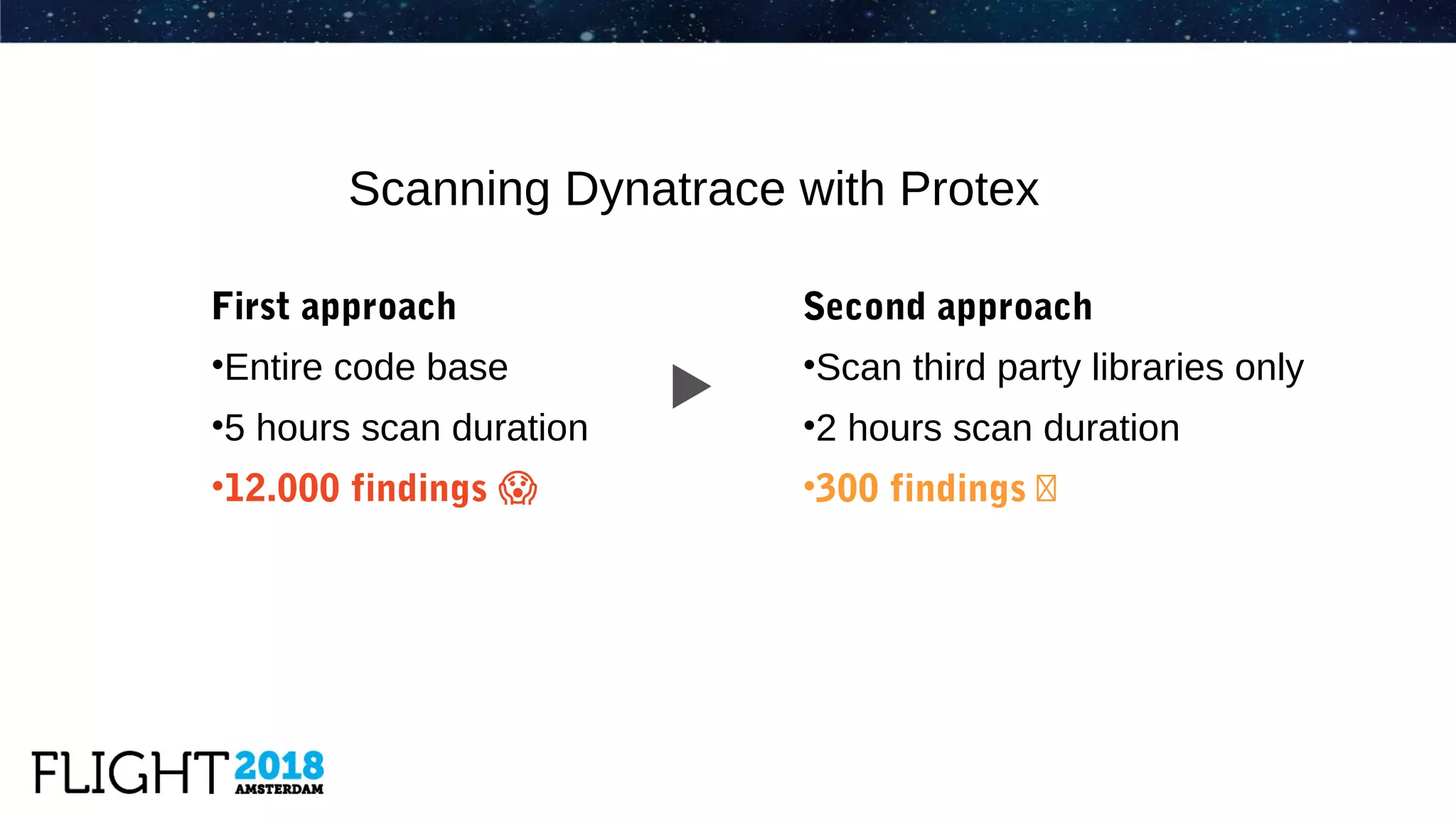
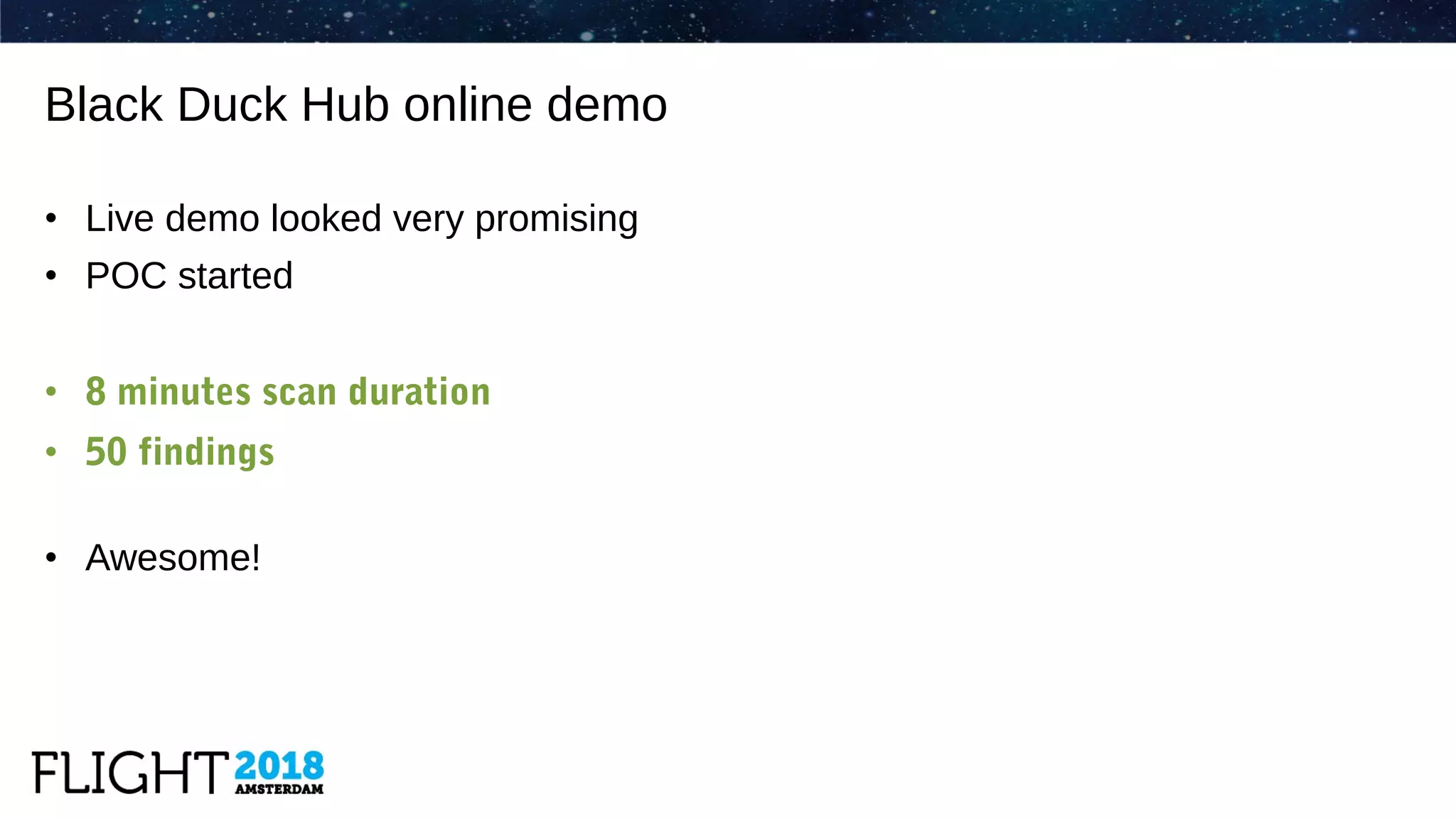
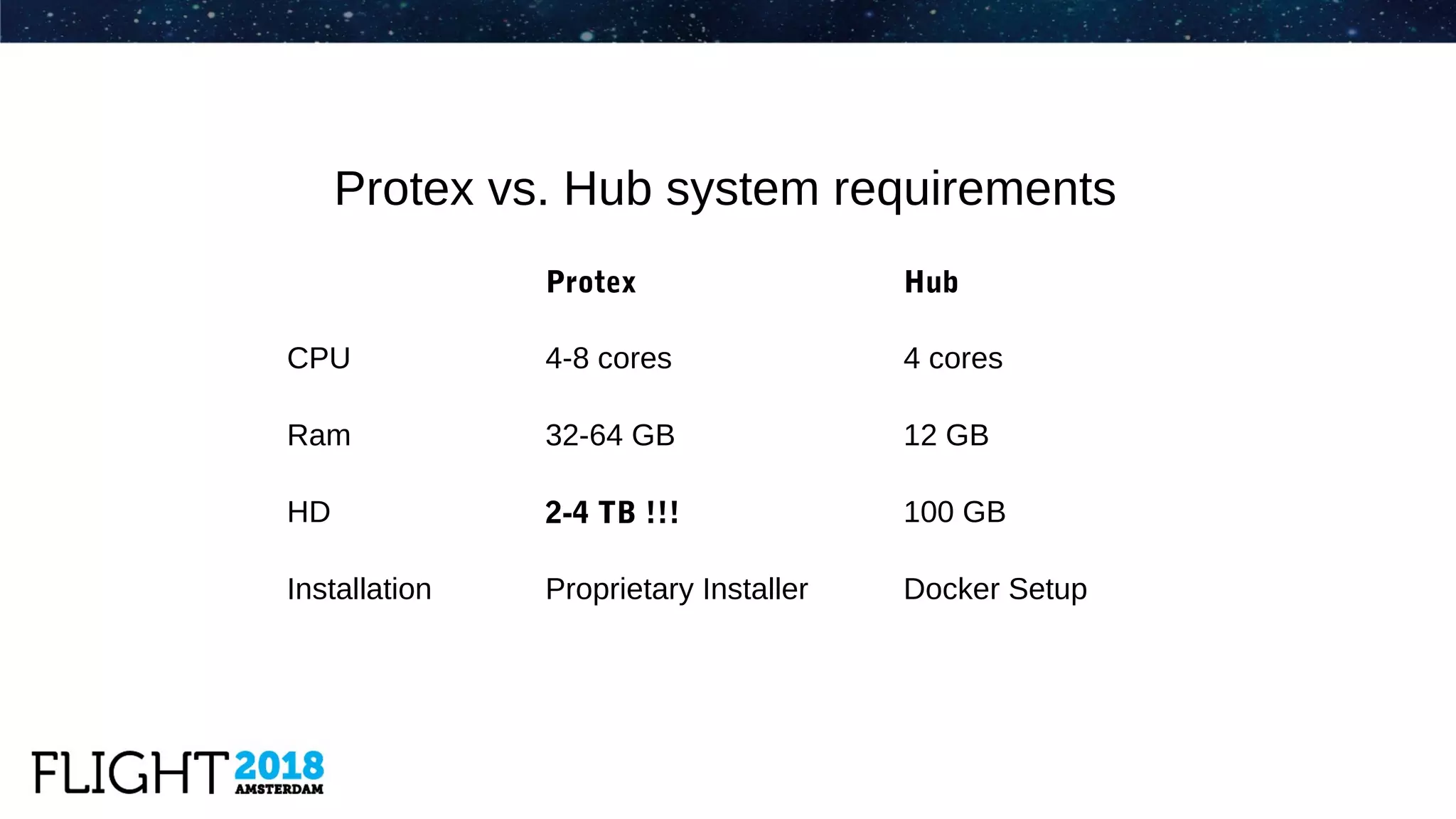
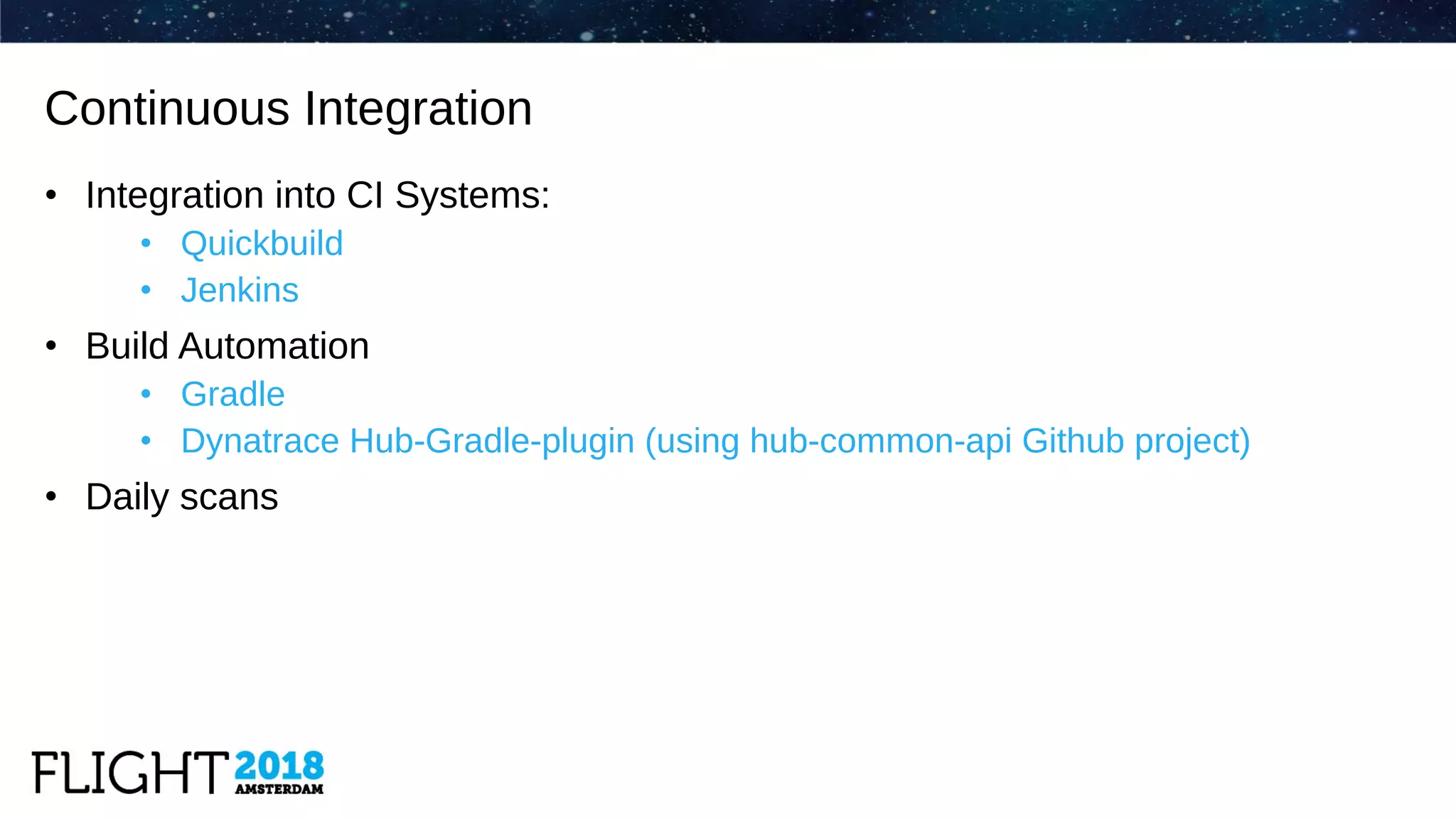
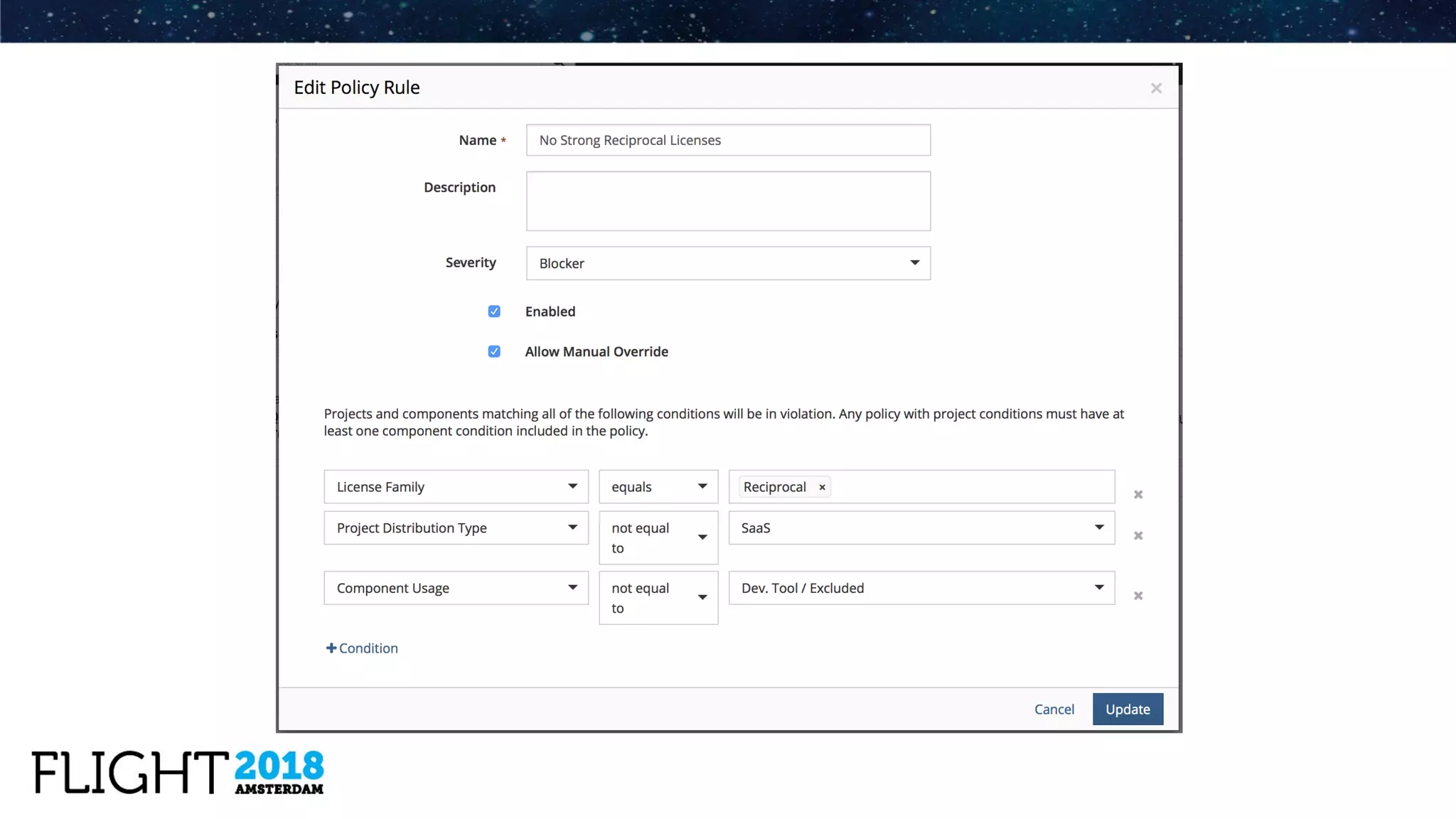
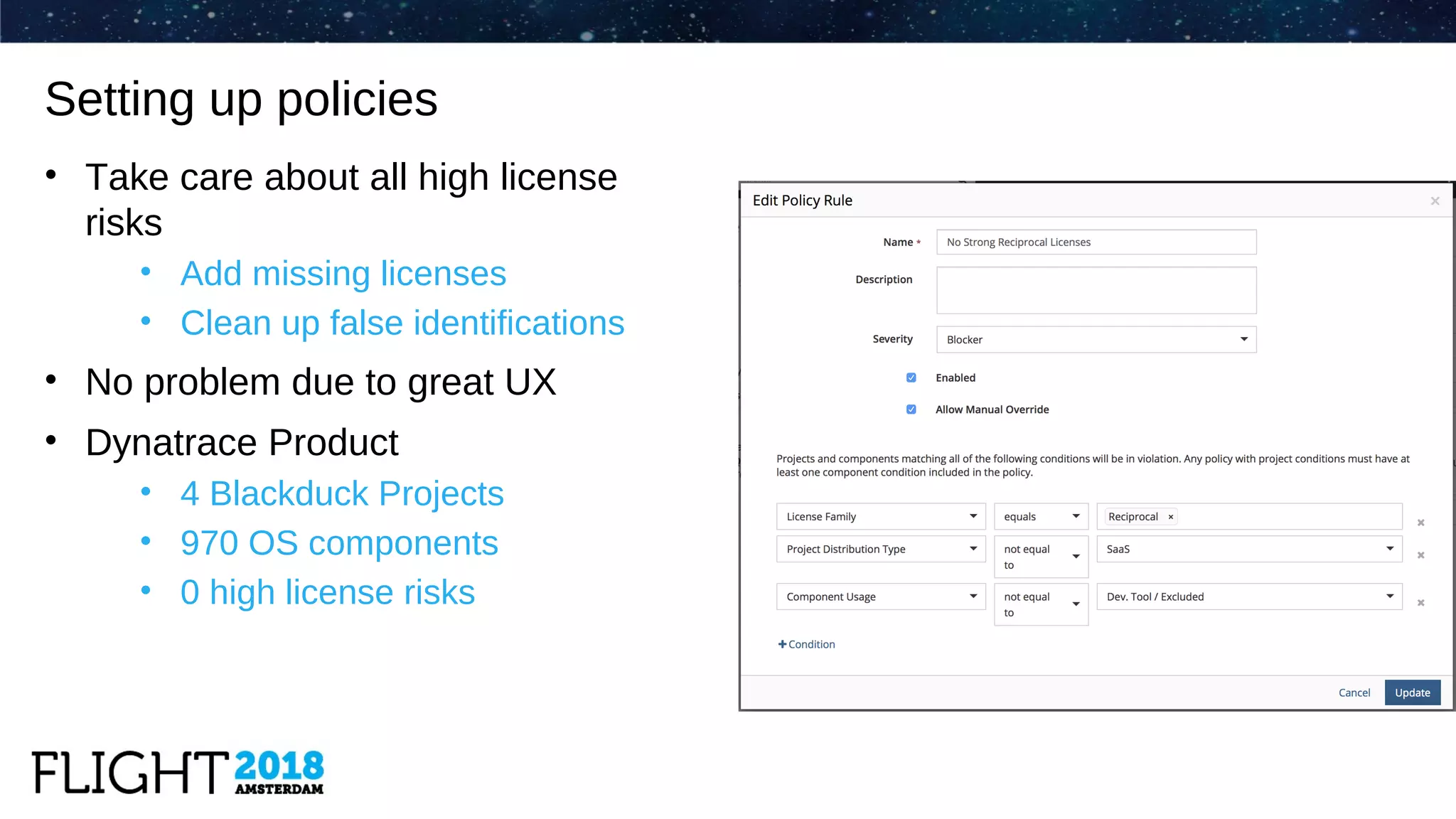
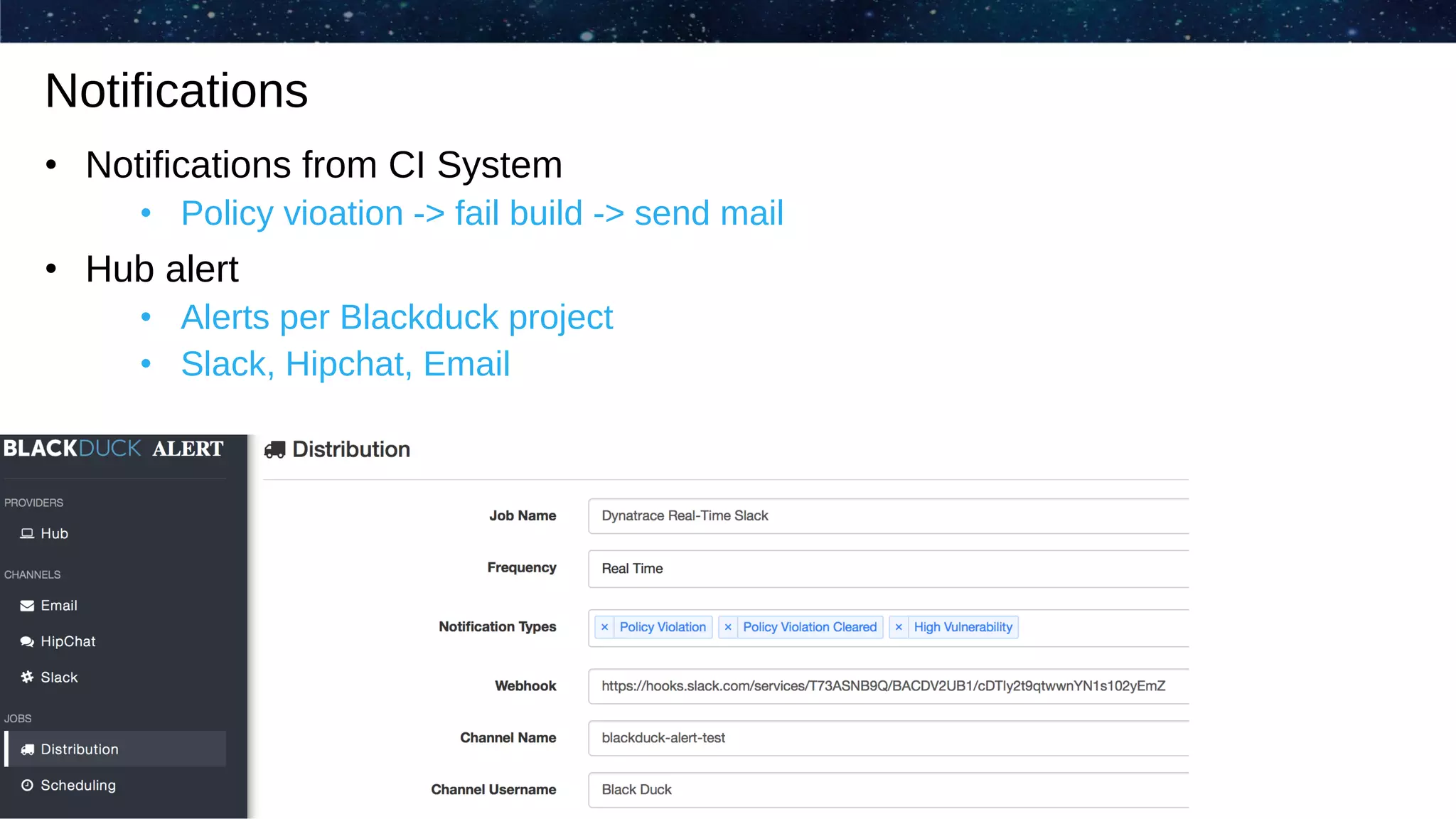
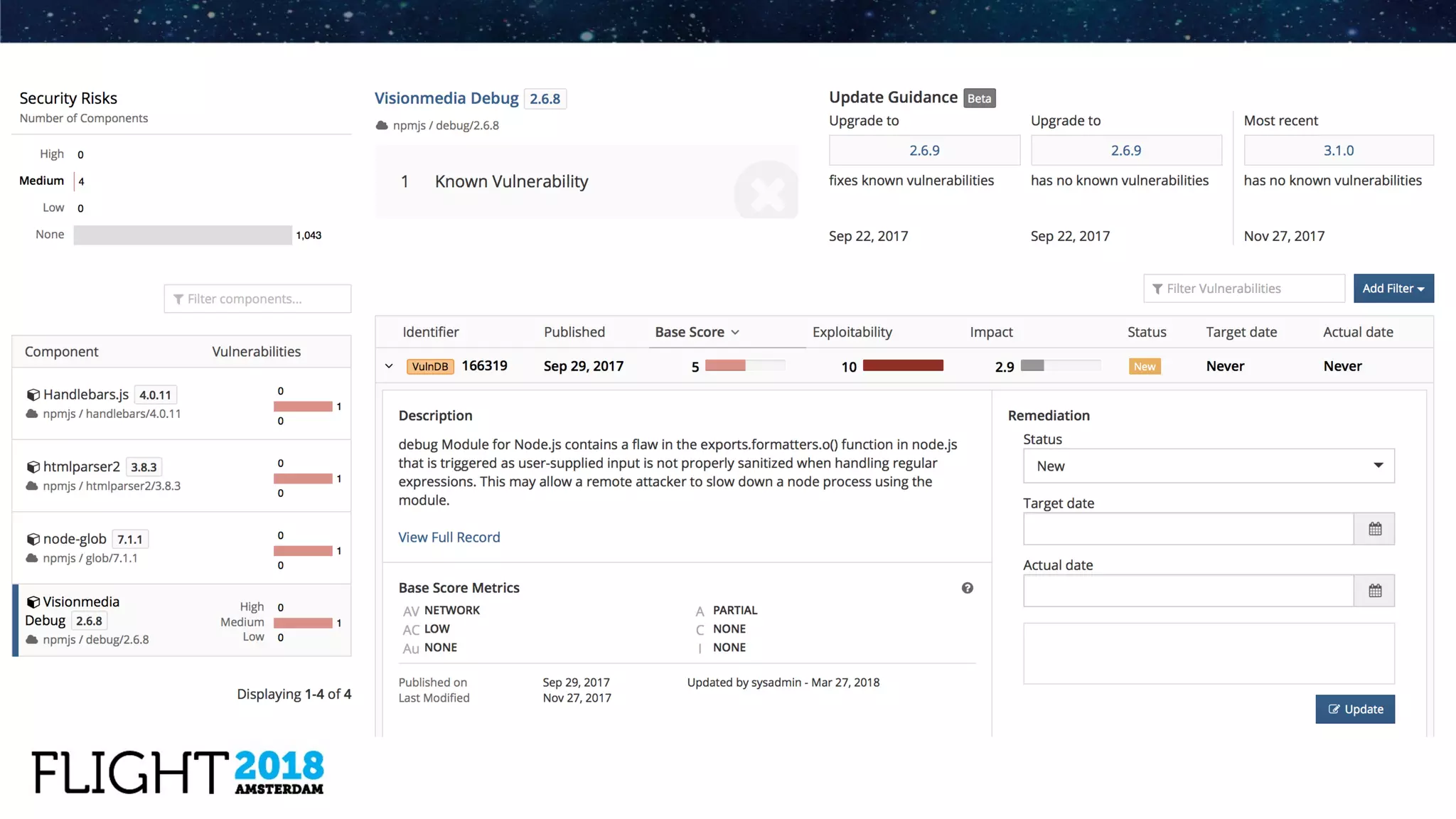
The document outlines the evolution of Dynatrace from using Protex for yearly scans to adopting Black Duck Hub for daily scans, reflecting significant advancements in product development and user experience over the years. It describes various challenges faced, including GPL license issues, and the transition to more efficient scanning methods that integrate well into continuous integration systems. The ultimate goal was to achieve a zero high license risks environment, while maintaining consistent software security and compliance as part of a secure development lifecycle.