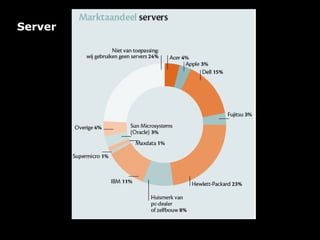
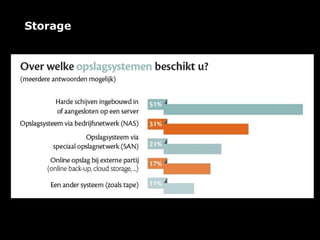
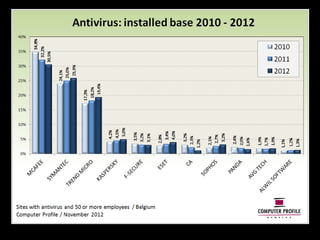
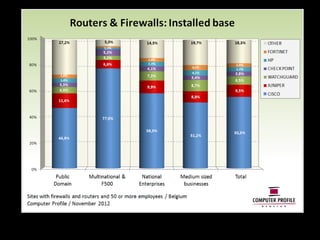
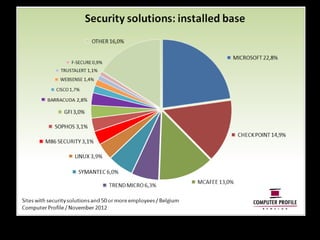
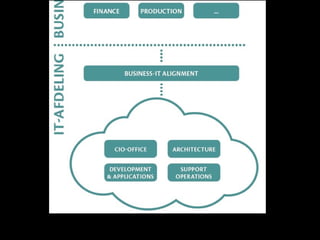
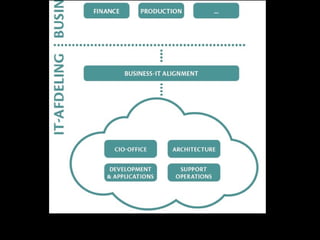
The document outlines the agenda for a seminar on business continuity. It includes presentations on market research, best practices for business continuity management, and customer cases from various organizations. There will be a break followed by three presentations from customers on their business continuity strategies, and a walking dinner will conclude the event.