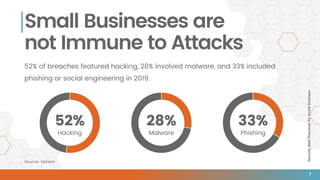
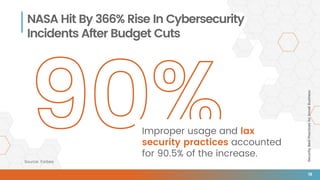
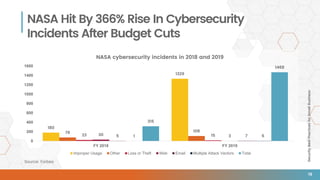
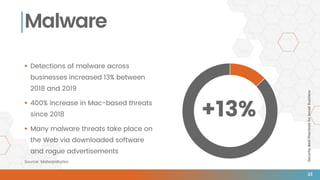
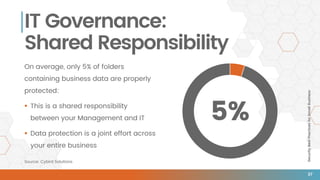
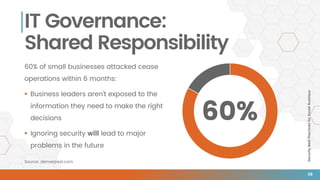
The document outlines essential security best practices for small businesses, emphasizing the importance of proactive measures to protect against cyberattacks that increasingly target this demographic. It highlights critical areas such as perimeter security, data protection, staff training, and incident response, indicating that 60% of small businesses attacked cease operations within six months. Valiant Technology provides a framework aligning the CIA triad principles with practical cybersecurity strategies tailored for small businesses.