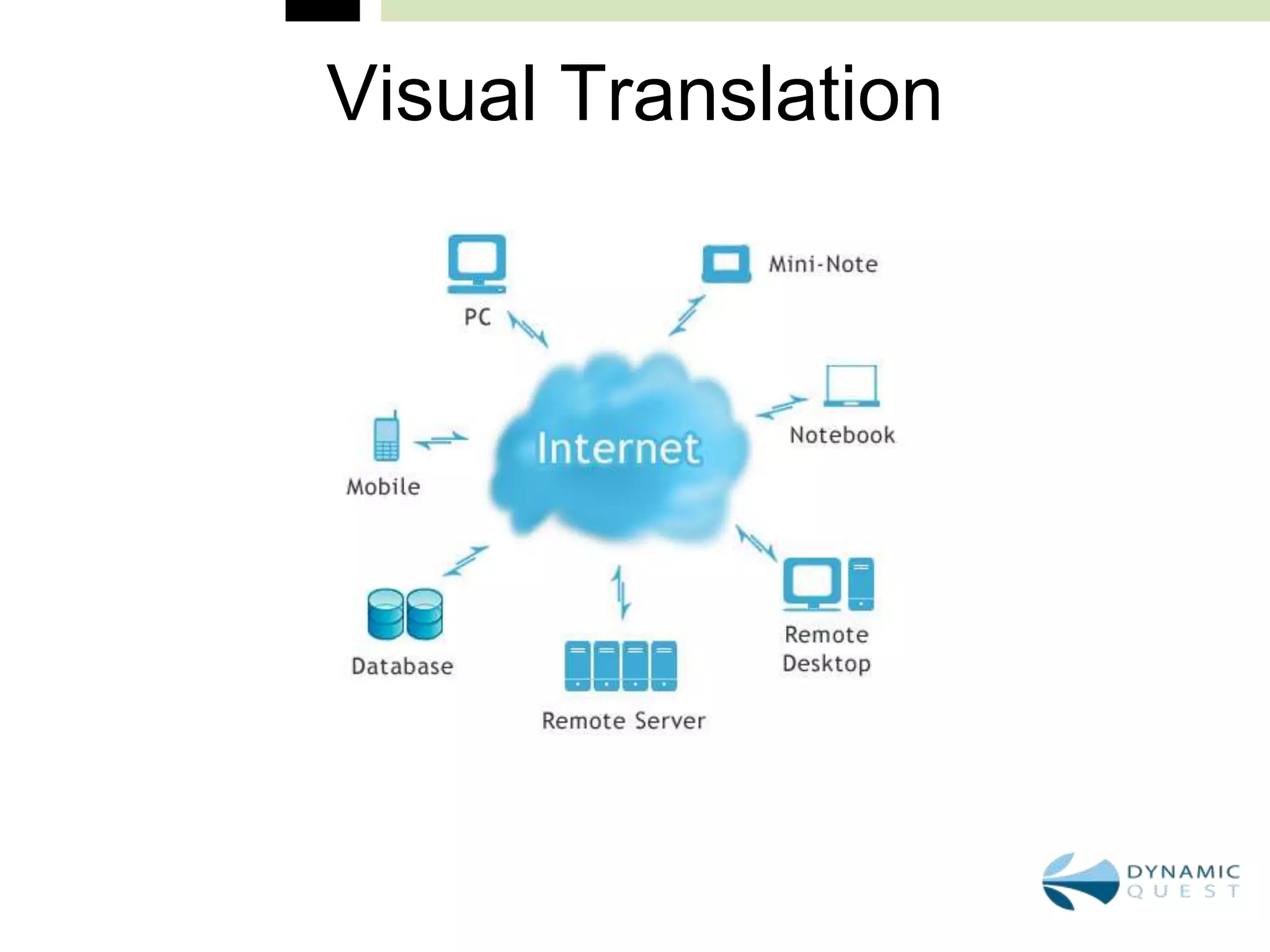
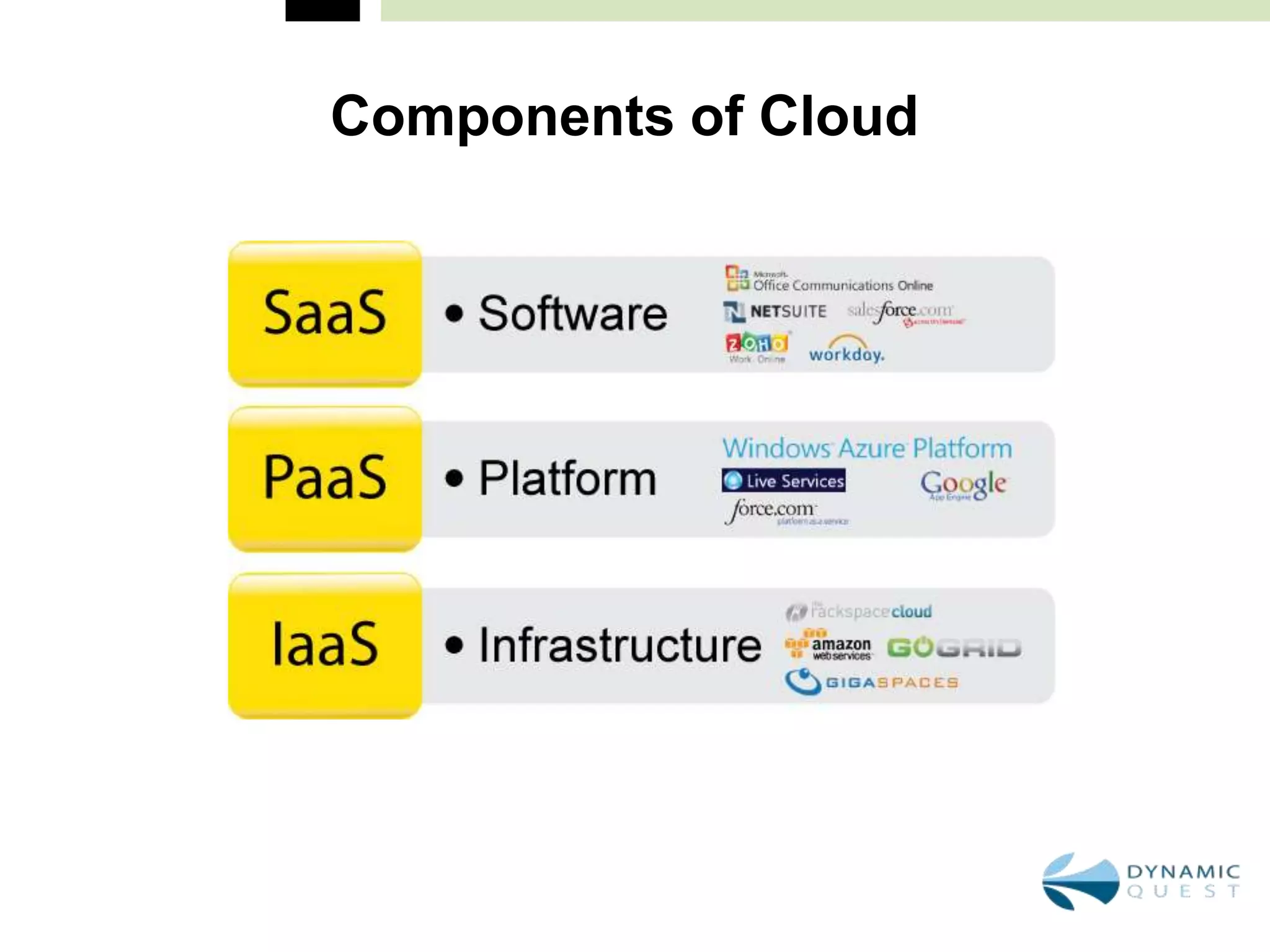
This document summarizes a continuing education conference for accounting, finance, and human resources professionals on technology updates for 2011. The conference will cover topics including cloud computing, security best practices, disaster recovery plans, and how to effectively use social media for business. The presenter will discuss what cloud computing really means, current security threats facing businesses, how to safeguard mission critical data through disaster recovery plans, and how to establish social media policies for business collaboration. The conference aims to bring professionals up to date on important technology topics and best practices.