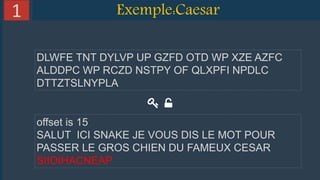
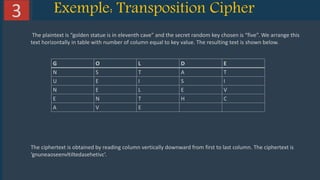
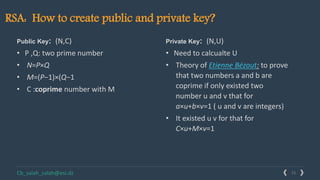
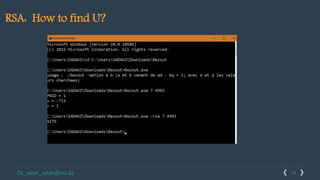
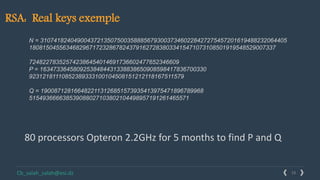
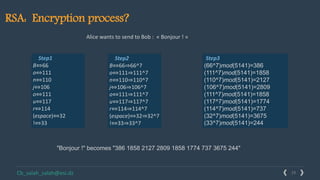
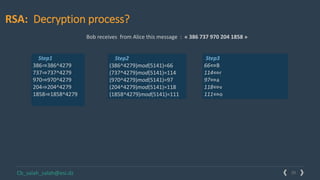
This document provides an overview of cryptography and several encryption techniques throughout history. It begins with an introduction to terminology used in cryptography. Traditional cryptography techniques are then discussed, including transposition ciphers, Playfair ciphers, and the Vigenere cipher. The document also provides examples of how to implement each of these traditional ciphers. Finally, it discusses modern cryptography and provides a detailed explanation of how the RSA algorithm works, including how to generate public/private key pairs and how the encryption and decryption processes are performed.