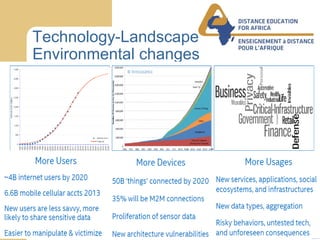
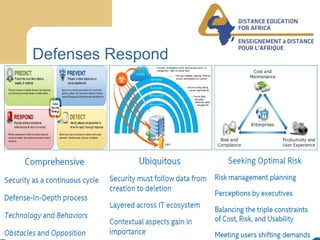
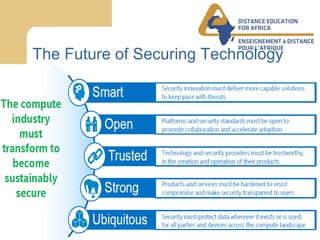
This document discusses the future of cybersecurity and the trends driving its evolution. Technology adoption is increasing the attack surface and value of information. In response, threats are becoming more professionalized and defenses are struggling to keep up. However, as impacts increase awareness, demands for better security will drive defenses to evolve towards more optimal and sustainable security practices. Leadership, awareness, best practices, and collaboration will be key to achieving security in the face of growing threats.