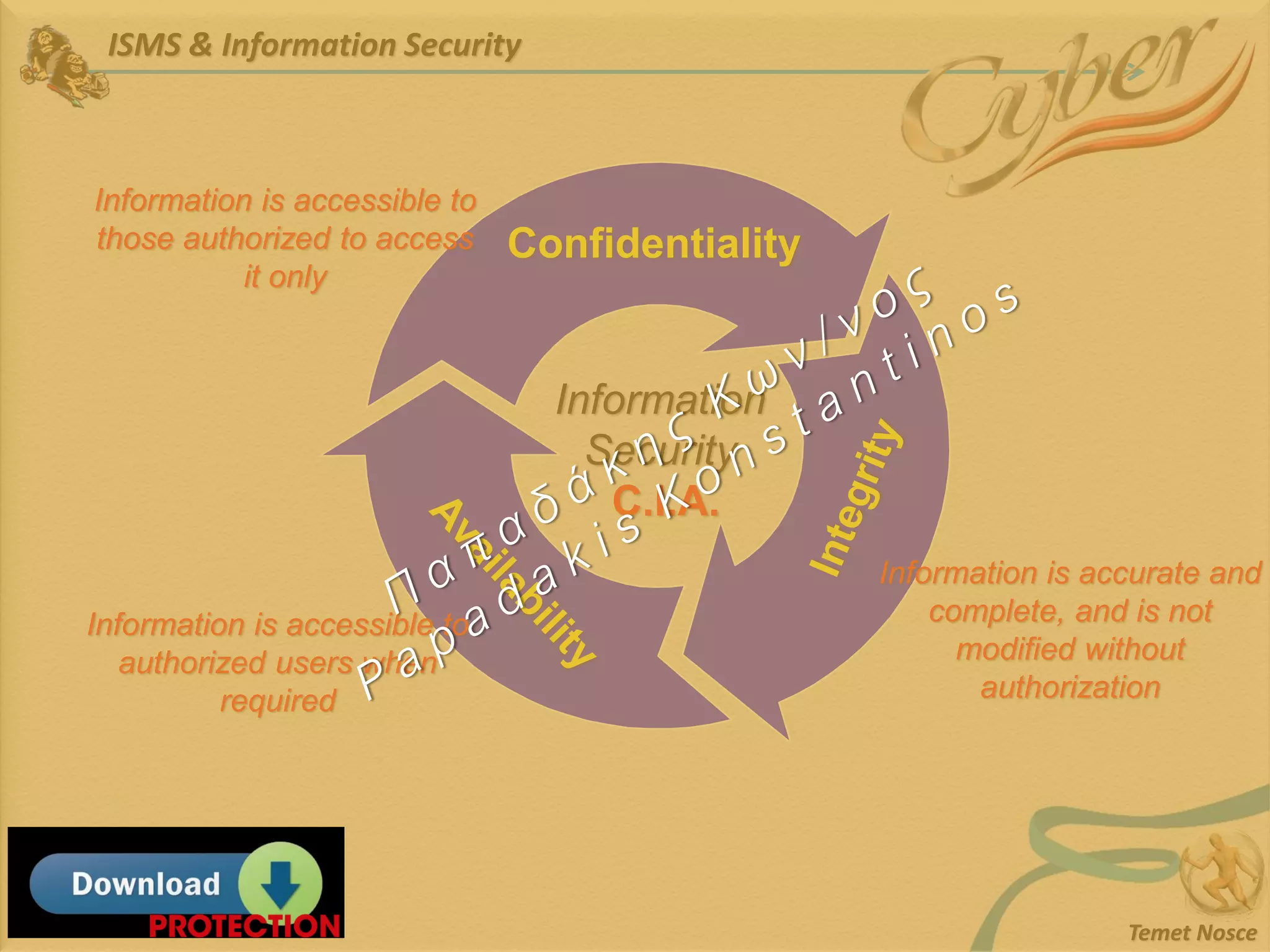
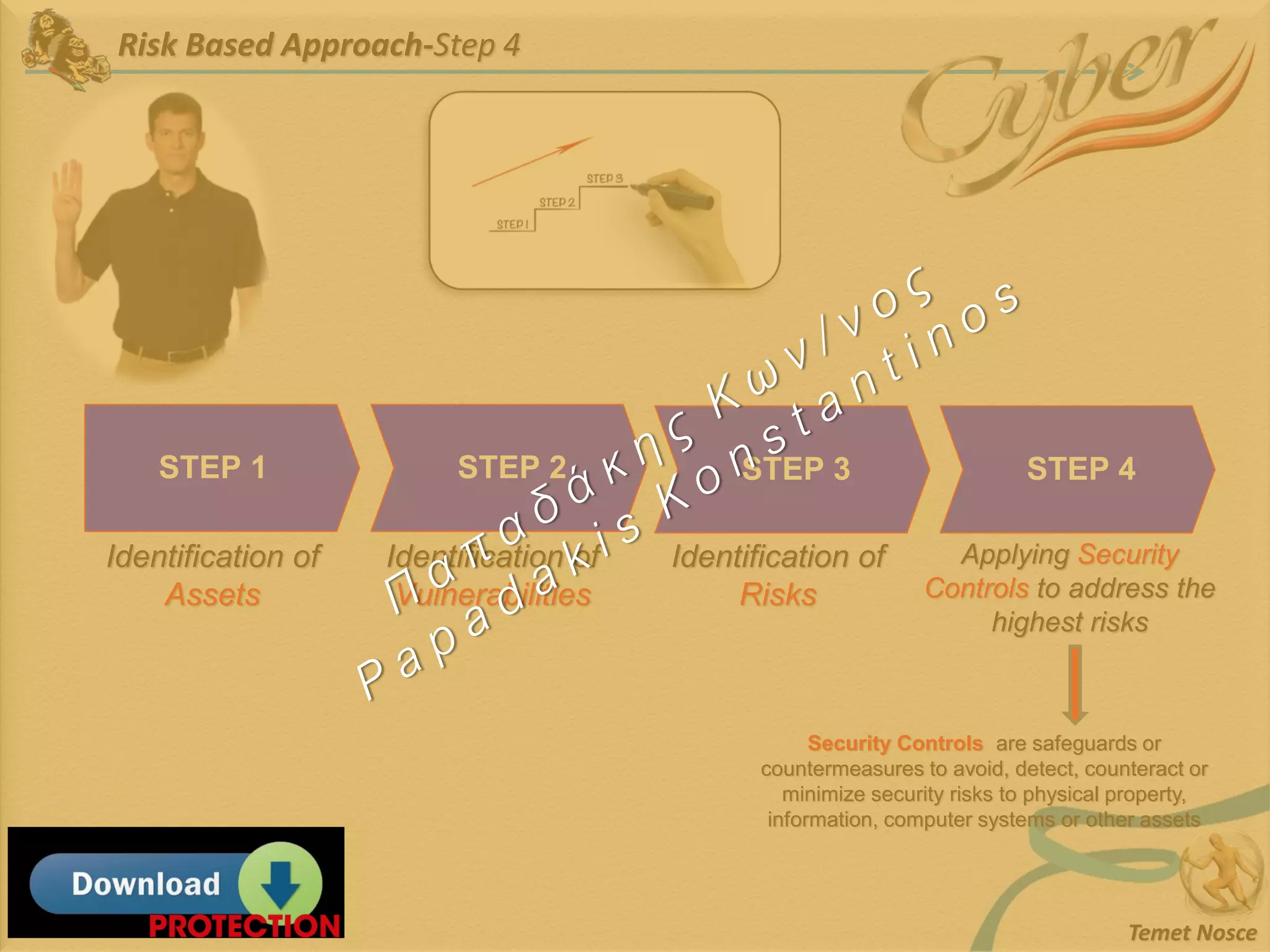
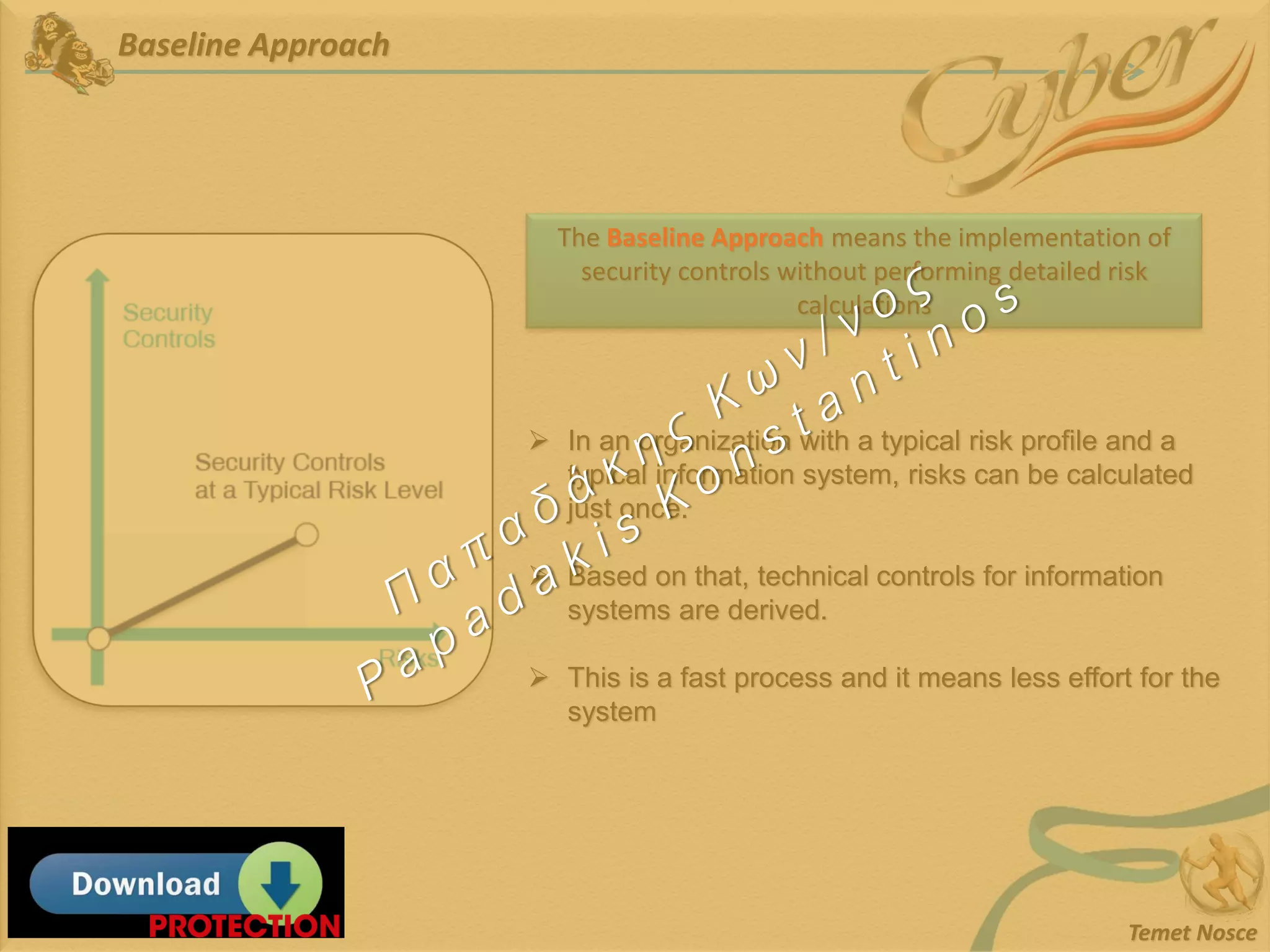
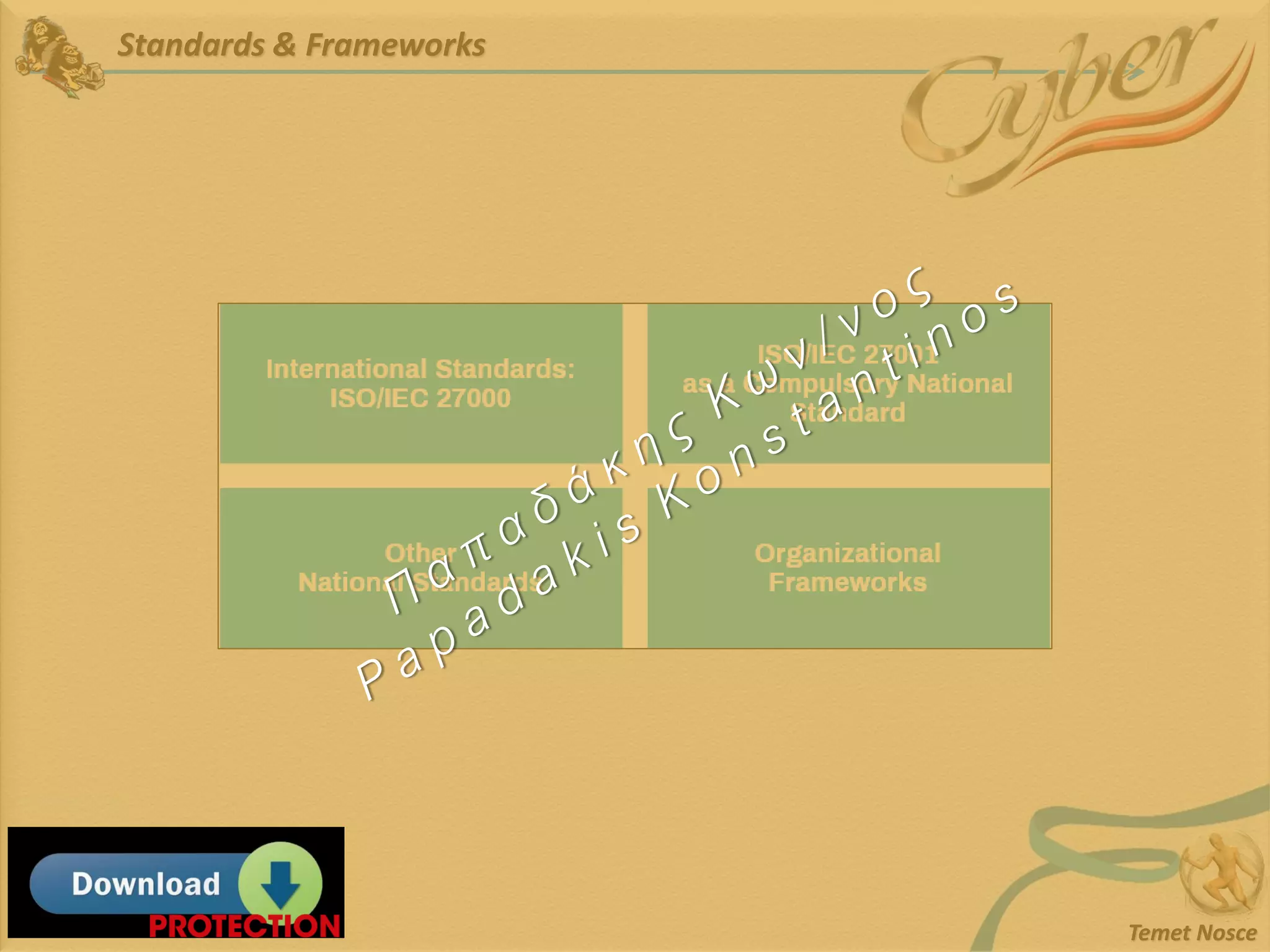
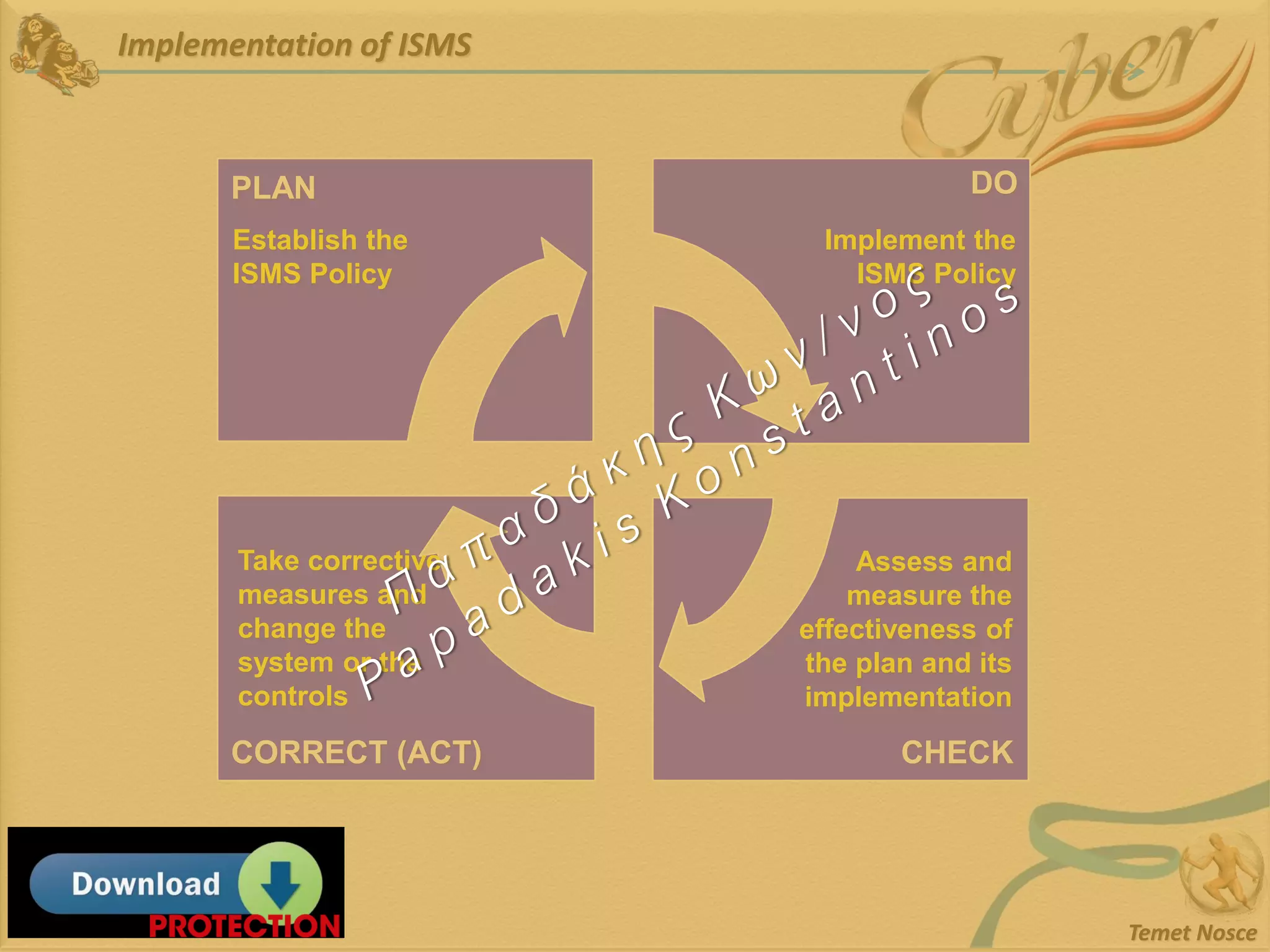
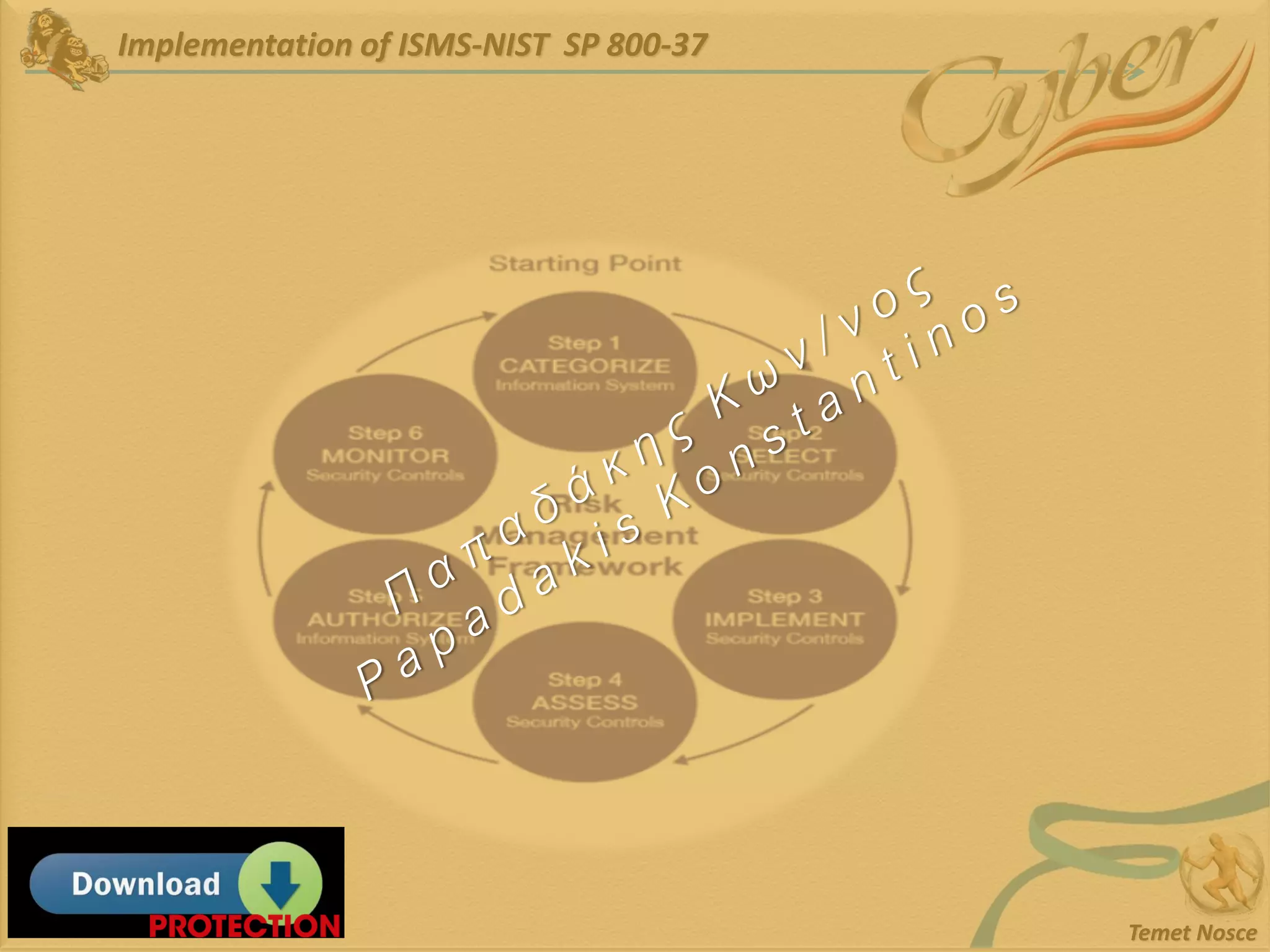
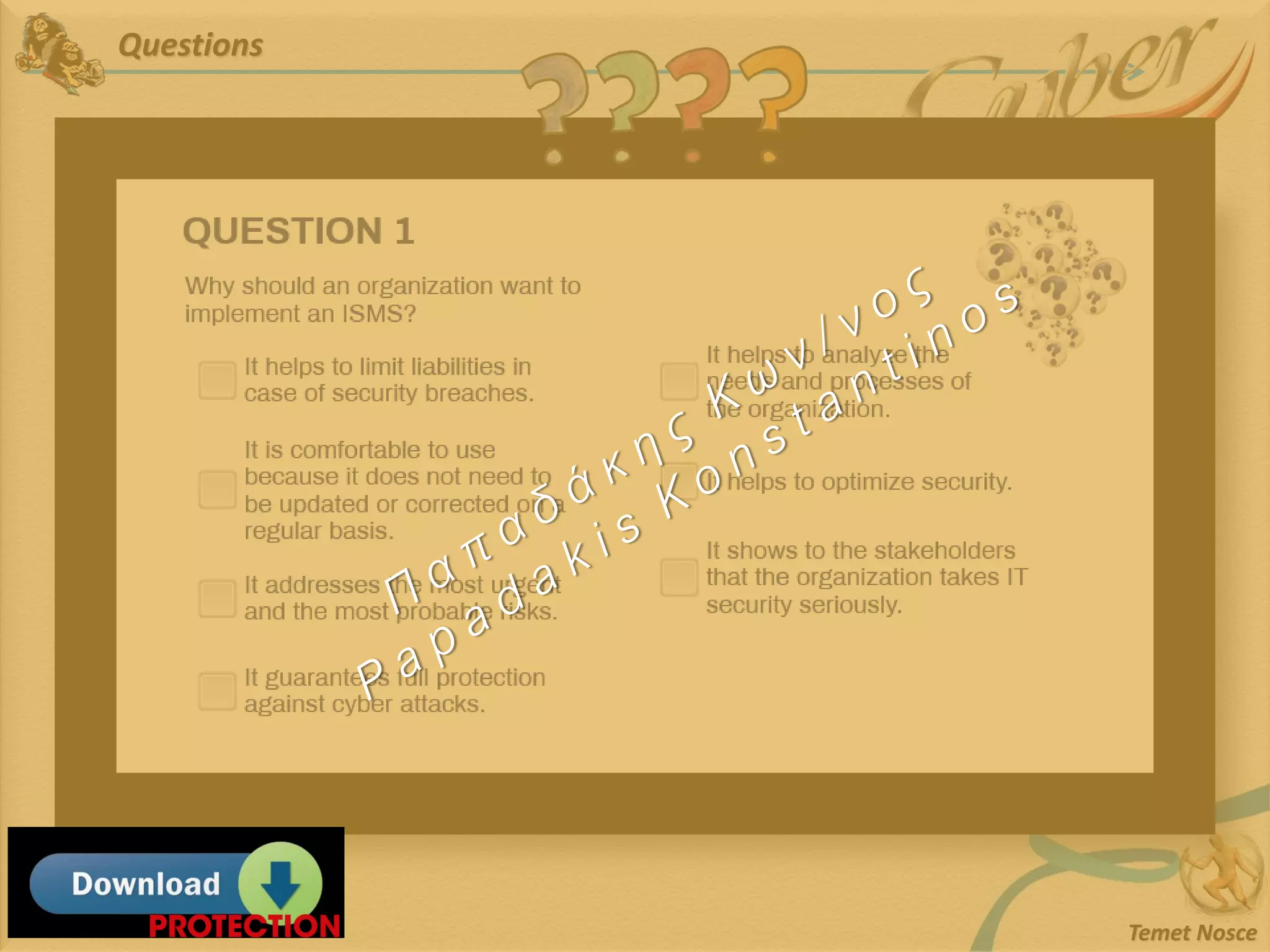
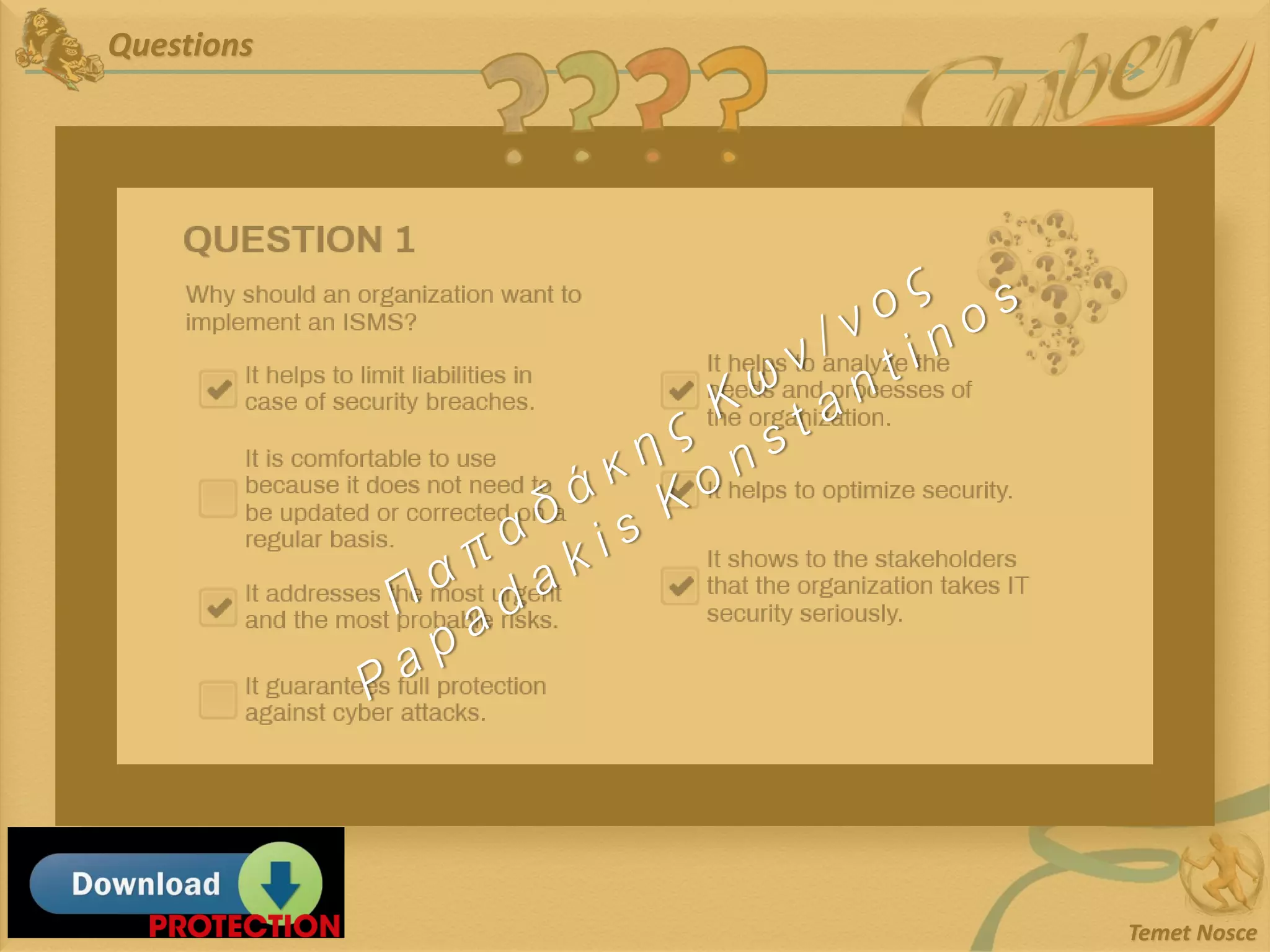
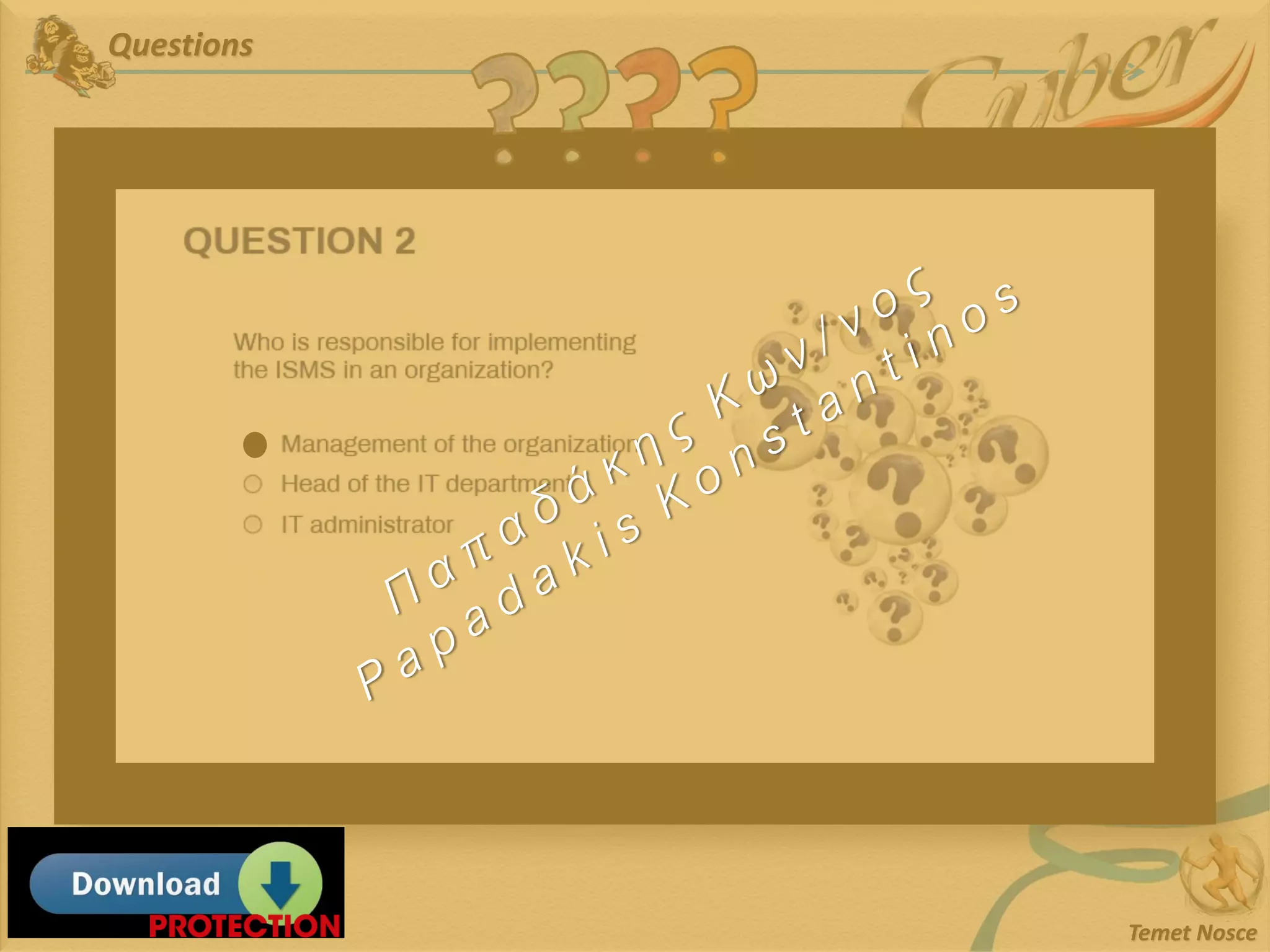
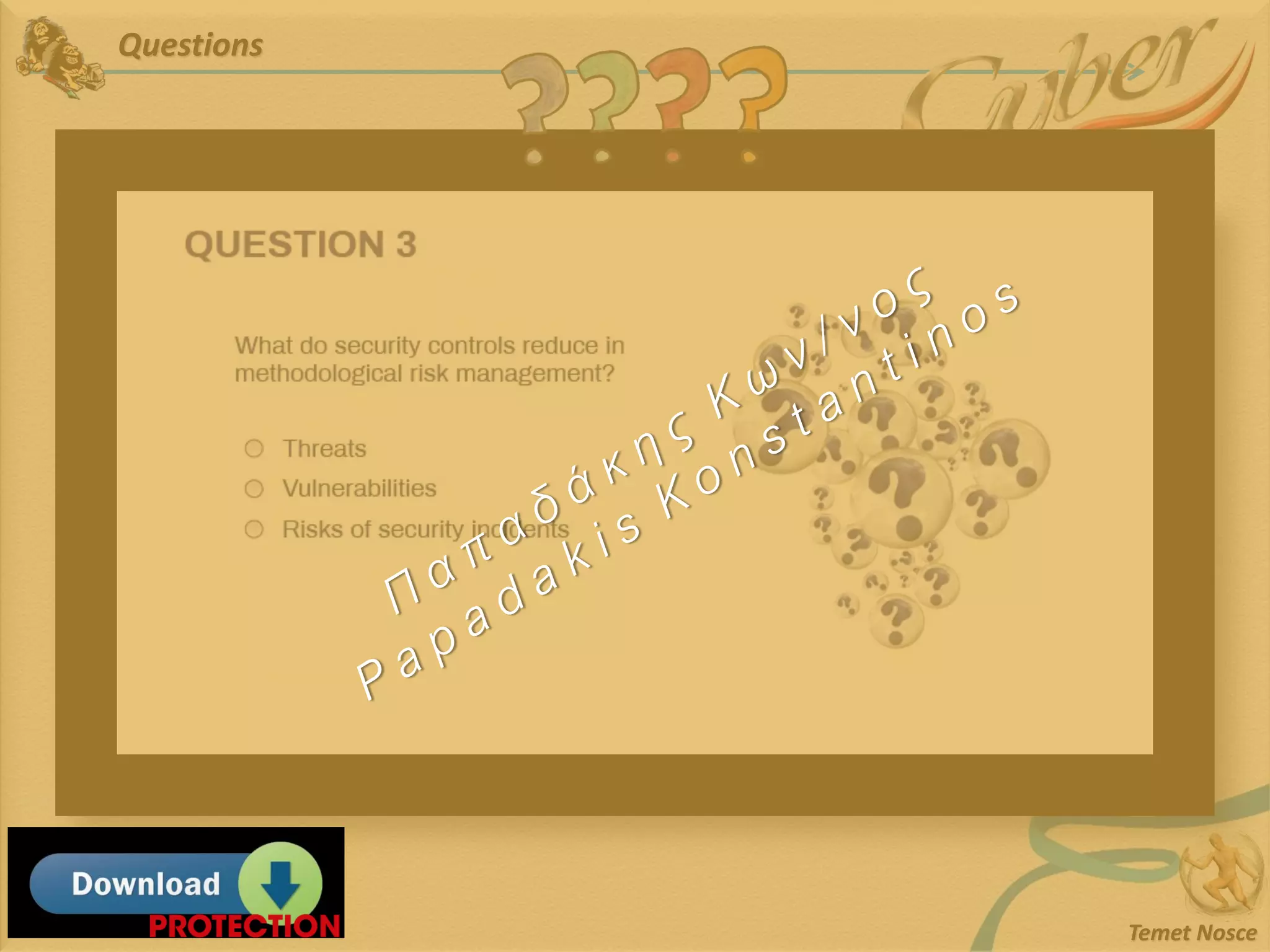
This document discusses Information Security Management Systems (ISMS). It begins by defining an ISMS as a set of practices and policies for managing security risks to information systems in a systematic way. It then describes the purposes and benefits of implementing an ISMS, which include providing governance, optimizing security, providing transparency, and reducing organizational and personal liability. The document outlines the risk-based methodology for implementing an ISMS, which involves identifying assets, vulnerabilities, risks, and applying security controls. It also discusses some common ISMS standards and frameworks.