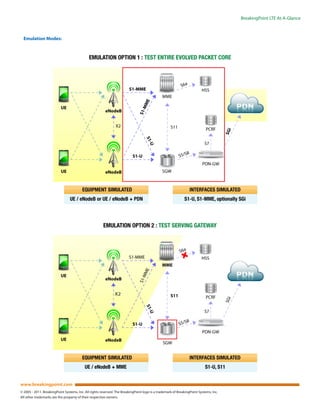
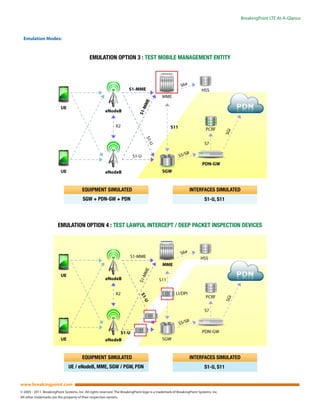
The Breakingpoint CTM products offer a solution for telecom carriers to test and validate LTE/4G networks by emulating millions of users under real-world conditions while maintaining cost-effectiveness. These products provide capabilities for high-performance simulations, security attacks, and malware testing, enabling carriers to enhance the performance, security, and stability of their network infrastructure. With user-friendly interfaces and extensive automation, the Breakingpoint CTM significantly simplifies complex testing processes for large-scale mobile networks.