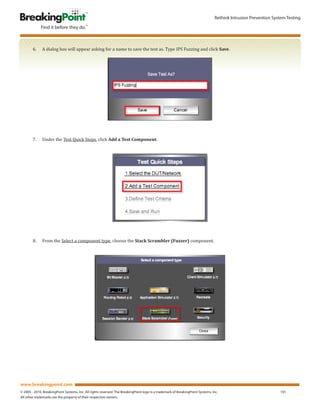
The document outlines a methodology for testing intrusion prevention systems (IPS) to evaluate their performance, security, and stability under real-world conditions. It emphasizes the importance of thoroughly testing IPS devices to ensure they can effectively mitigate malicious traffic while allowing legitimate access. Various tests are described, including assessment of maximum connections, throughput, and responses to syn floods and malicious traffic, using the BreakingPoint Storm CTM for detailed measurements.