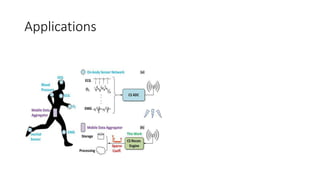
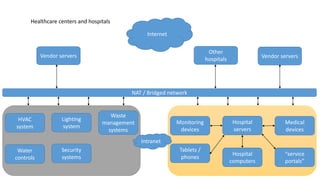
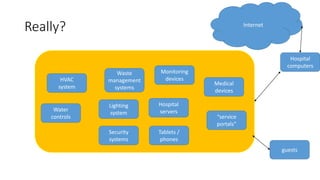
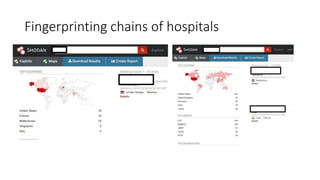
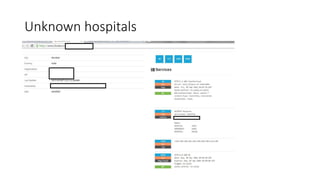
The document discusses the vulnerabilities in hospital cybersecurity and the various attack vectors targeting healthcare institutions, including insider and outsider threats. It highlights the significant risks posed by unprotected hospital infrastructure and the misuse of medical devices due to inadequate security measures. The author underscores the urgent need for improved security protocols in the face of evolving cyber threats.

























![Sample FHIR request
{
"resourceType": "Query",
"text": {
"status": "generated",
"div": "<div>[Put rendering here]</div>"
},
"identifier": "urn:uuid:42b253f5-fa17-40d0-8da5-44aeb4230376",
"parameter": [
{
"url": "http://hl7.org/fhir/query#_query",
"valueString": "example"
}
]
}](https://image.slidesharecdn.com/breakingintohospitals-160203163657/85/Breaking-into-hospitals-38-320.jpg)