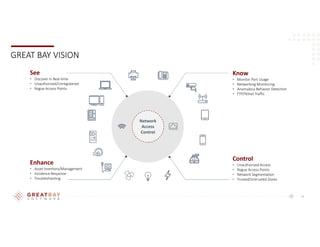
The document outlines strategies for reducing cyber risk at community banks, focusing on challenges faced, the FFIEC Cybersecurity Assessment Tool (CAT), and best practices for security controls. Key areas include risk management, threat intelligence, cybersecurity controls, and incident management, emphasizing the importance of comprehensive assessments and employee training. Recommendations also highlight the need for ongoing monitoring, secure access management, and adherence to regulatory guidelines to protect customer information.