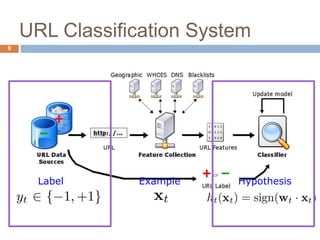
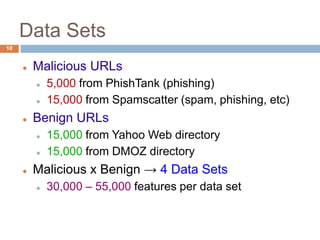
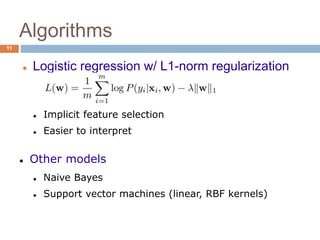
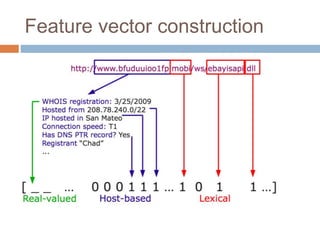
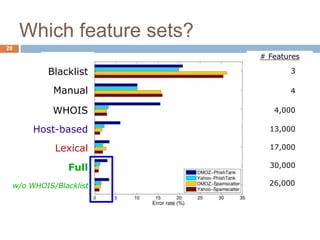
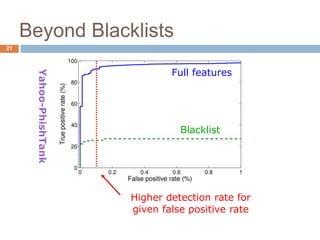
This document discusses using machine learning to detect malicious URLs. It proposes extracting various features from URLs, including querying blacklists, domain registration information, host properties, and lexical features of the URL. These features are then used to train classifiers like logistic regression to distinguish benign from malicious URLs. The approach is shown to achieve over 86.5% accuracy in detecting malicious URLs using a diverse set of over 18,000 features, performing better than blacklists alone. Future work includes scaling the approach for deployment and incorporating webpage content analysis.



![State of the Practice
8
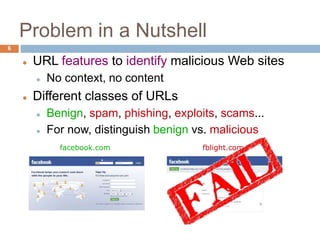
Current approaches
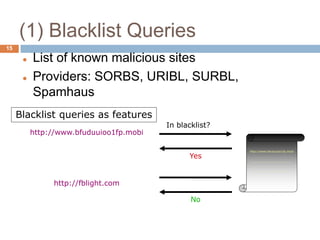
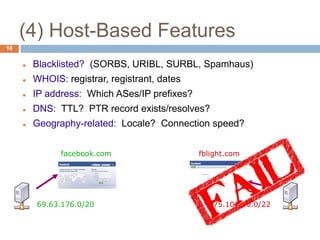
Blacklists [SORBS, URIBL, SURBL, Spamhaus]
Learning on hand-tuned features [Garera et al, 2007]
Limitations
Cannot predict unlisted sites
Cannot account for new features
Arms race: Fast feedback cycle is critical
More automated approach?](https://image.slidesharecdn.com/maliciousurldetectionusingmachinelearning-150126024719-conversion-gate02/85/Malicious-Url-Detection-Using-Machine-Learning-8-320.jpg)