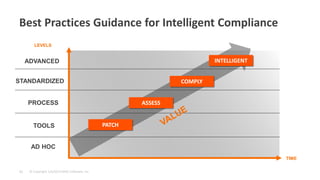
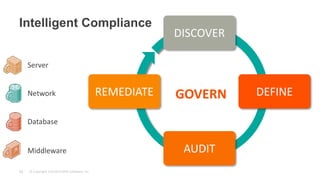
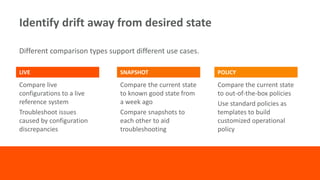
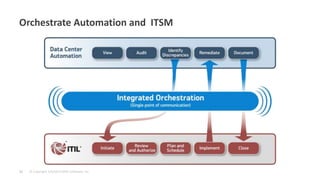
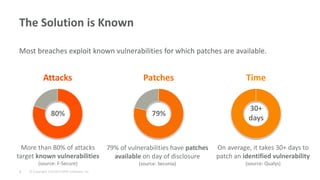
The document discusses best practices for implementing intelligent compliance to protect systems from security vulnerabilities, emphasizing the importance of addressing known vulnerabilities through timely patching. It highlights the challenges organizations face in maintaining compliance and outlines the need for collaboration between security and operations teams, automated processes, and continuous monitoring. Key takeaways stress that compliance is complex and must be addressed in stages with no one-size-fits-all solution.




![© Copyright 1/6/2015 BMC Software, Inc6
“ ”
[…] the breadth of at-risk machines is going to be
significantly higher with Shellshock than with Heartbleed.
Shellshock
NIST: 10/10
A new bug every week](https://image.slidesharecdn.com/intelligent-compliance-engage-slidesharev2-150106134300-conversion-gate02/85/Best-Practices-for-Intelligent-Compliance-6-320.jpg)