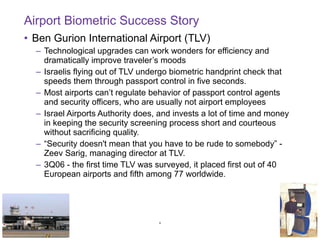
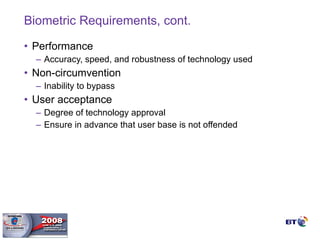
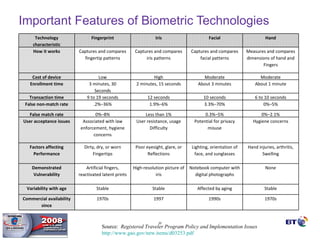
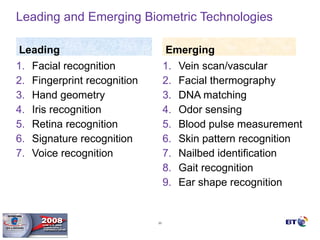
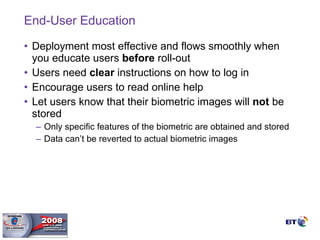
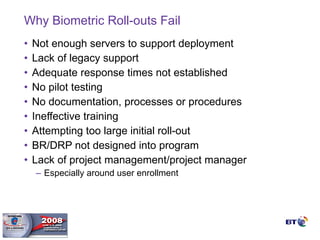
- Biometrics can be an effective technology for aviation security if properly implemented, but requires careful planning and management to be successful.
- Key factors for a successful biometric deployment include having clearly defined security objectives, starting small and gaining successes before expanding, and ensuring effective user education and buy-in.
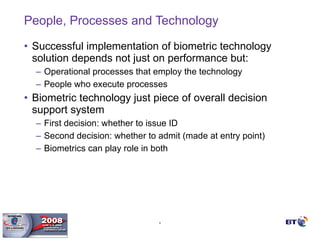
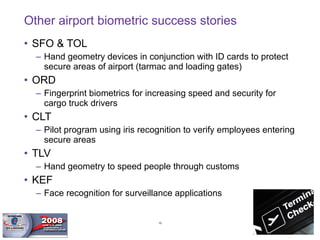
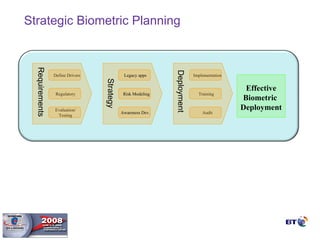
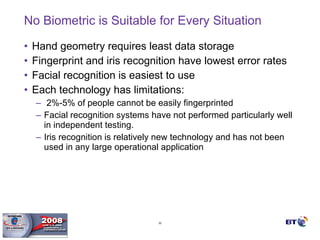
- Biometrics are one part of an overall security system and must be integrated with operational processes and personnel to be effective. Proper project methodology is essential.





























![Q/A – Contact info Ben Rothke, CISSP, QSA Senior Security Consultant BT Professional Services [email_address]](https://image.slidesharecdn.com/benrothkeaoa2008-biometrics-100112110532-phpapp01/85/Ben-Rothke-Aoa-2008-Biometrics-41-320.jpg)